Microsoft recently shared a vision for the future of American technology and economic competitiveness, highlighting Artificial Intelligence (AI) as central to this change. The company views AI as “the electricity of our age,” capable of boosting innovation and productivity across all sectors. Microsoft’s vision rests on three pillars: Advancements in …
Read More »TimeLine Layout
January, 2025
-
5 January
City Bank Customer financial reports posted dark market for sale
According to Bangladesh Cyber Security Intelligence (BCSI) report, City Bank has been the victim of a cyber attack. The hacker group was selling the bank’s customer financial reports on a dark web market. BCSI has contacted the hacker. In the published report, BCSI shared screenshots of the conversation with the …
Read More » -
4 January
3.3 Million Email Server Expose User Passwords and Messages in Plain Text
Around 3.3 million servers are running POP3/IMAP email services without encryption (TLS) enabled, the Shadowserver Foundation, a nonprofit security organization, has discovered. Most of these servers reside in the US, Germany, and Poland. POP3 (Post Office Protocol version 3) is an aging protocol used by email clients to retrieve emails …
Read More » -
2 January
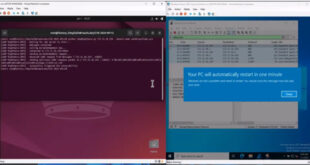
Memory-Dump-UEFI
Researcher dumping memory to bypass BitLocker on Windows 11Researchers have demonstrated a method to bypass Windows 11’s BitLocker encryption, enabling the extraction of Full Volume Encryption Keys (FVEKs) from memory. This vulnerability underscores the risks associated with physical access attacks and highlights potential weaknesses in memory protection mechanisms. The attack revolves around capturing the contents of a computer’s …
Read More » -
2 January
CVE-2024-49112
PoC Exploit Released for Zero-Click vulnerability in WindowsSafeBreach Labs revealed a zero-click vulnerability in the Windows Lightweight Directory Access Protocol (LDAP) service, dubbed “LDAP Nightmare”. This critical vulnerability, tracked as CVE-2024-49112, has been assigned a CVSS score of 9.8, highlighting its severe implications for enterprise networks. SafeBreach researchers demonstrated how the exploit could crash unpatched Windows Servers, …
Read More »
December, 2024
-
31 December
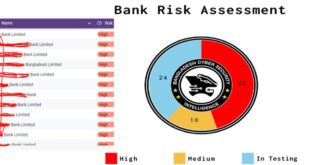
Financial Threat Assessment 2024
BCSI marks Bangladeshi 28 banks high, 10 medium for cyber attackBangladesh Cyber Security Intelligence (BCSI) has published Financial Threat Assessment report for 2024. In an era where financial institutions and Critical Information Infrastructure (CII) are essential to both economic and national stability, the growing frequency and complexity of cyber threats have underscored a pressing truth: Bangladesh’s national security is under …
Read More » -
31 December
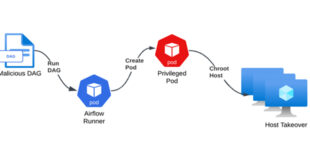
Misconfigured Kubernetes RBAC in Azure Airflow Could Expose Entire Cluster
Cybersecurity researchers have uncovered three security weaknesses in Microsoft’s Azure Data Factory Apache Airflow integration that, if successfully exploited, could have allowed an attacker to gain the ability to conduct various covert actions, including data exfiltration and malware deployment. “Exploiting these flaws could allow attackers to gain persistent access as …
Read More » -
31 December
US Treasury says it was hacked by China via third party: Beijing denies
The US Treasury Department said on Monday that Chinese-linked hackers were able to gain access to ‘unclassified documents’ after compromising the agency’s networks earlier this month. According to a US Treasury letter addressed to US Senators Sherrod Brown (D-OH) and Tim Scott (R-SC) on Monday – the Chinese hackers gained …
Read More » -
30 December
PoC Exploited Released for Oracle Weblogic Server Vul
Security researchers have warned that a Proof-of-Concept (PoC) exploit has been publicly released for a critical vulnerability affecting Oracle WebLogic Server. The flaw tracked as CVE-2024-21182, poses a significant risk to organizations using the server, as it allows an unauthenticated attacker with network access to compromise the targeted system. The …
Read More » -
30 December
Microsoft warn dev urgently to update .NET installer link
Microsoft is forcing .NET developers to quickly update their apps and developer pipelines so they do not use ‘azureedge.net’ domains to install .NET components, as the domain will soon be unavailable due to the bankruptcy and imminent shutdown of CDN provider Edgio. Specifically, the domains “dotnetcli.azureedge.net” and “dotnetbuilds.azureedge.net” will be …
Read More »
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind