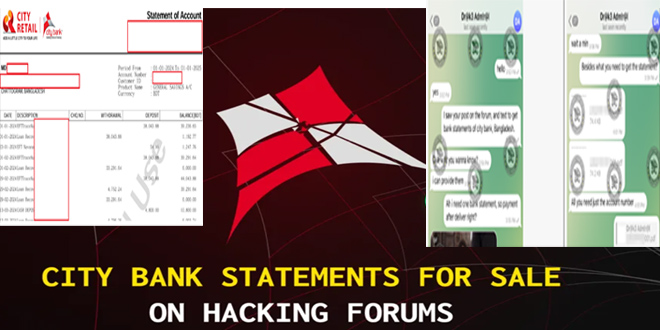
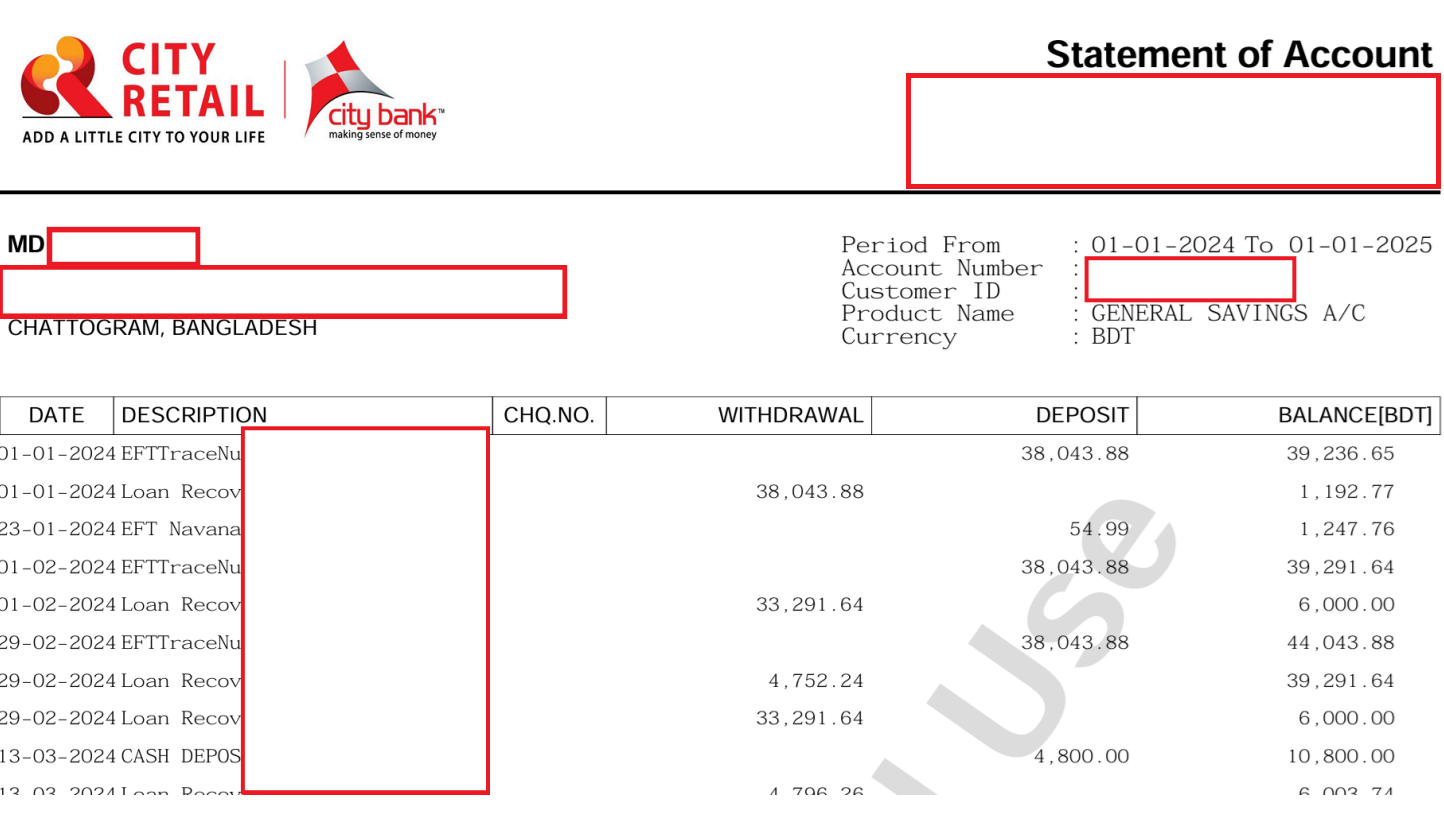
According to Bangladesh Cyber Security Intelligence (BCSI) report, City Bank has been the victim of a cyber attack. The hacker group was selling the bank’s customer financial reports on a dark web market.
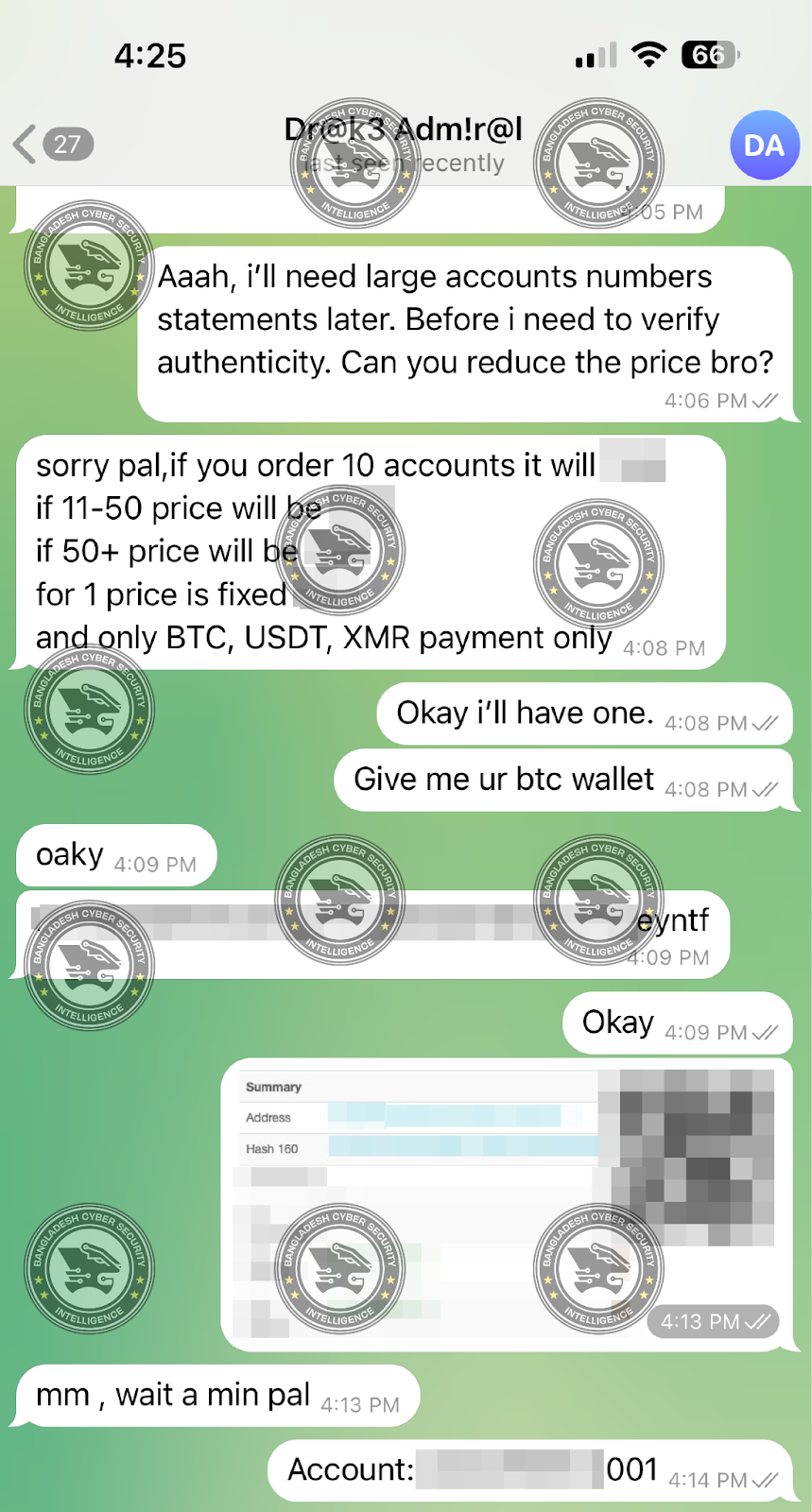
BCSI has contacted the hacker. In the published report, BCSI shared screenshots of the conversation with the hacker. It is claimed that it obtained some documents from the hacker through the conversation and checked them and found their authenticity.
BCSI says that the security gap was reported to the bank in mid-2024. Then in December of that year, a contributor to BCSI’s CS-CERT reported the matter again to BCSI. After that, BCSI conducted research and confirmed the cyber attack on the bank.
Exploitation Overview:
The attacker bypassed the multi-factor authentication process due to weak session management.
Once logged in, previously authenticated sessions could be reused to access other accounts.
Session Issues:
Session tokens were not properly invalidated, allowing attackers to reuse them and gain unauthorized access.
With this vulnerability, the threat actor could retrieve City Bank customers’ statements without needing further authentication.
BCSI informed City Bank about the issue earlier this year. After learning about it, the bank authorities identified the vulnerability on Friday (January 3) and took remedial measures.
Sumon Ahmed Sabir, EC member, APNIC said, “The news of customer information of a well-known bank like City Bank being sold on dark forums is really sad as it is customer crucial information. Banks should be more proactive in protecting customer data.
In addition, this expert emphasizes on regular VAPT and IT audits to ensure the cyber security of banks. He said vulnarabilities can be identified through regular assessments. He also emphasizes on various trainings on cyber security to make skilled manpower.”
Updated: (01/07/2025)
City bank’s MD and CEO Mashrur Arefin told media in a statement that, “City Bank provides a web portal where customers can download their account statements using Two-Factor Authentication (2FA), which involves a One-Time Password (OTP). This portal, referred to as the “Statement Portal,” is solely for generating account statements,” said the statement.
According to the official statement, “on January 2, 2025, a system “glitch” occurred that allowed a hacker to bypass the 2FA process and gain access to account statements of other customers. The number of account statements accessed that way was low because the hacker could access only those accounts whose numbers were known to him. However, due to the glitch, the system failed to send OTPs to the account holders’ registered phone numbers, enabling unauthorized access to the statement(s) by the hacker.”
“This vulnerability was limited to viewing account statements only. That is, no transactions or other unauthorized activities were or could be performed by the hacker,” as per City Bank’s statement.
According to the statement, City bank has taken timely action regarding the matter, their tech security team reviewed the portal’s ecosystem, revoked all access, and terminated all bypassed sessions. Moreover, the bank deployed a dedicated real-time monitoring team to oversee further activities.
“To ensure such incidents do not recur, the IT team, through its developer wing, has already implemented robust measures to prevent similar vulnerabilities in our portals. Also our Security Operations Center (SOC) team has enhanced its 24/7 monitoring capabilities. With full assurance we can inform our customers that such incidents will not take place again,” mentioned City bank in their official statement regarding the issue.”
Source: BCSI, Banglavision, Daily star
(Media Disclaimer: This report is based on research conducted internally and externally using different ways and quoted 3 published reports . The information provided in this report is for reference only from those report, and users are responsible for relying on it. Infosecbulletin is not liable for the accuracy or consequences of using this information by any means)
Uganda confirms hack of central bank accounts, Refutes $17 Million Claim
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind