A sophisticated South Asian APT group is conducting a widespread espionage campaign against military personnel and defense organizations in Sri Lanka, Bangladesh, Pakistan, and Turkey.
Threat actors are using a multi-stage attack strategy that combines phishing with new Android malware to target the mobile devices of military-related individuals.
The campaign shows strong operational security and advanced techniques, using legitimate cloud services and altered open-source tools to avoid detection.
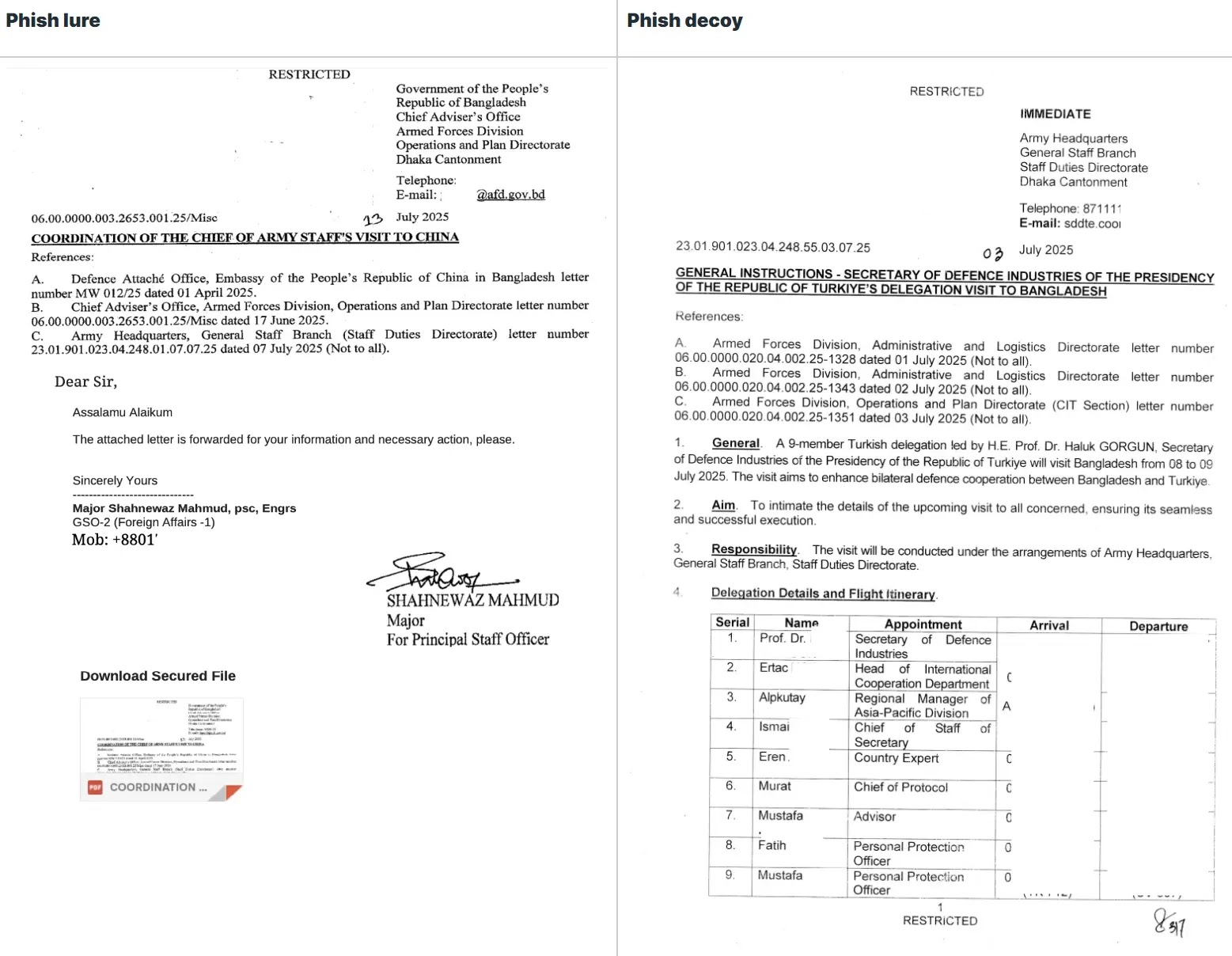
Recent findings show ZIP files such as “Coordination of the Chief of Army Staff’s Visit to China.zip,” (MD5: cf9914eca9f8ae90ddd54875506459d6) which hold compressed PDFs meant to trick users.
These documeFraudulent domains are created to imitate legitimate organizations like the Bangladesh Army, DGDP, and Turkish defense companies, redirecting users who are misled by malicious links.
StrikeReady analysts identified that embedded JavaScript is used to hinder source code visibility, a tactic seen in various campaigns.
Documents are directing victims to phishing sites on compromised Netlify domains, such as mail-mod-gov-bd-account-conf-files.netlify.app and coordination-cas-visit.netlify.app, which look like real government and military email portals.
Researchers found over 50 malicious domains impersonating South Asian military and government organizations, such as the Bangladesh Air Force, DGDP, and Turkish defense firms like Roketsan and Aselsan.
Malware, distributed via APK files like Love_Chat.apk (MD5: 9a7510e780ef40d63ca5ab826b1e9dab), pretends to be real chat apps but creates a backdoor to access hacked devices.
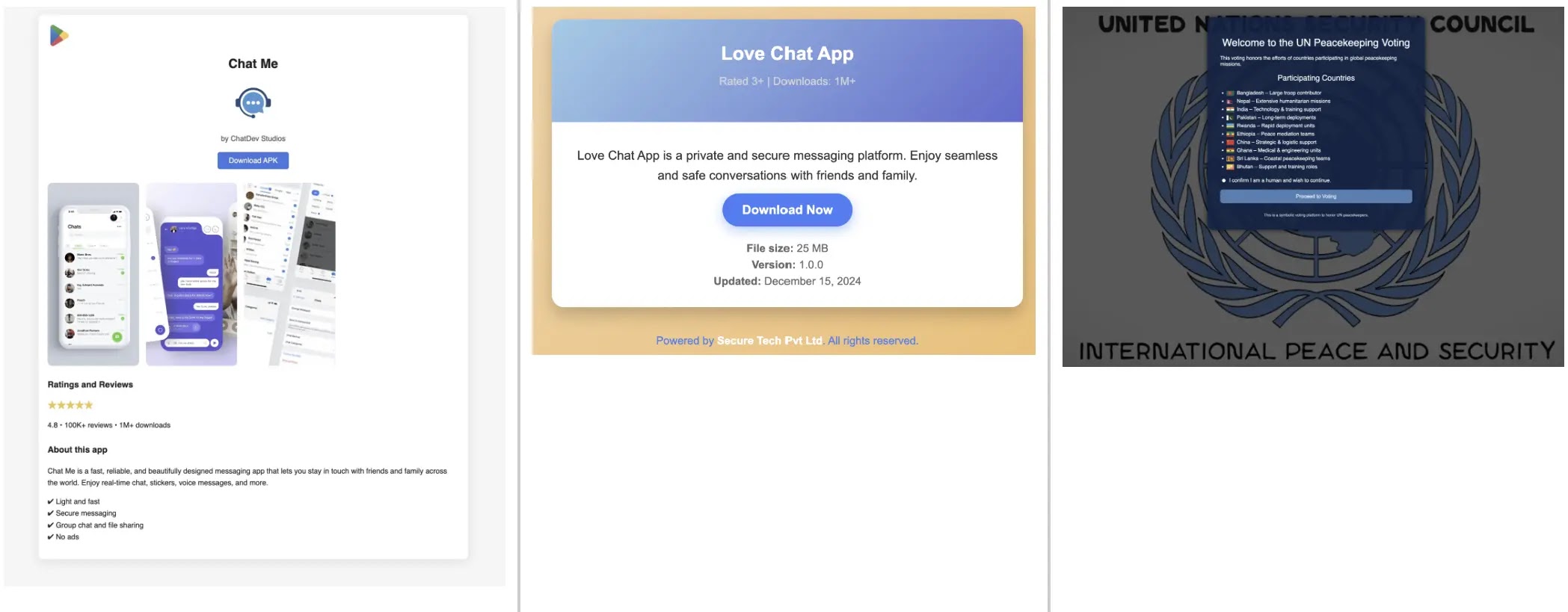
The decompiled application shows it can extensively steal data, sending different document types to command-and-control servers.
Android RAT Infrastructure:
The attackers changed the original Rafel RAT code, removing credit information and creating their own command-and-control communications through domains like quickhelpsolve.com and kutcat-rat.com.
 Decoys (Source – StrikeReady)
Decoys (Source – StrikeReady)
The malware requests dangerous permissions including ADD_DEVICE_ADMIN, READ_EXTERNAL_STORAGE, MANAGE_APP_ALL_FILES_ACCESS_PERMISSION, and READ_CONTACTS, enabling comprehensive device compromise.
The C2 infrastructure utilizes base64-encoded communication channels, with the primary command endpoint located at https://quickhelpsolve.com/public/commands.php.
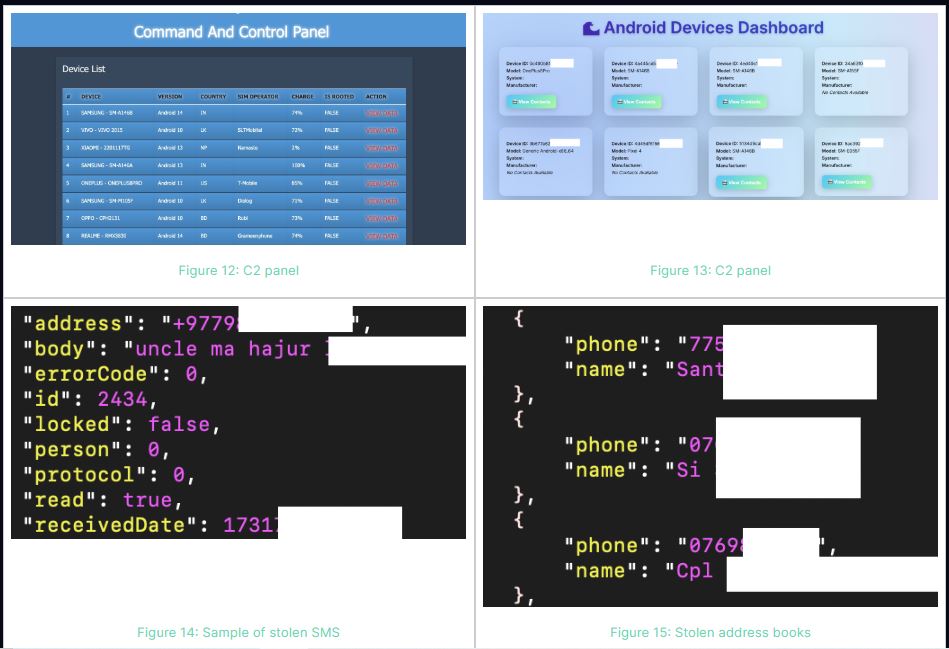
This central control lets operators send commands to hacked devices, gather stolen data, and keep ongoing access to victim networks.
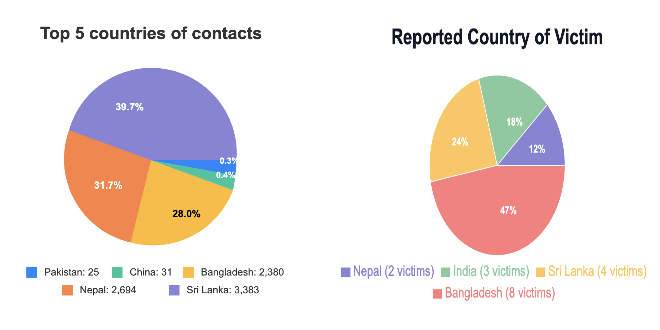
Security researchers found that hackers successfully breached military personnel in several countries, stealing SMS messages, contact lists with military ranks and duty stations, and sensitive documents.
BGD E-gov CIRT reported a coordinated phishing campaign has been uncovered targeting critical Bangladeshi infrastructure — particularly government organizations and law enforcement agencies. This attack leveraged compromised official email credentials to distribute fraudulent emails containing malicious attachments and deceptive login pages.
Bangladeshi gov.t/law enforcement email accounts compromised
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind