Ransomware activity soared in September after a temporary decrease in August, which was still higher than usual for summer.
In September, ransomware groups conducted 514 attacks, surpassing the 459 attacks recorded in March 2023 according to NCC group cyber threat intelligence report. The March attacks were mainly caused by the Clop group’s MOVEit Transfer data theft attacks.
Clop hardly did anything in September, suggesting that the advanced ransomware group is getting ready for their next major attack.
However, the record was achieved by other threat groups, led by LockBit 3.0 (79 attacks), LostTrust (53), and BlackCat (47).
LostTrust is a new threat actor in the list, making a dynamic entrance straight to second place.
LostTrust is thought to be an updated version of MetaEncryptor. It has already encrypted the networks of several organizations, some of which have also had data leaks.
RansomedVC is a newcomer in extortion attacks that use GDPR reporting threats. They are currently ranked fourth by NCC, with 44 attacks. It’s important to mention that some of the attacks claimed by RansomedVC were later found to be exaggerated.
This means that roughly one out of five attacks in September came from a new ransomware operation, highlighting their aggressiveness and capability for scale.
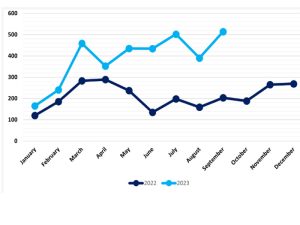
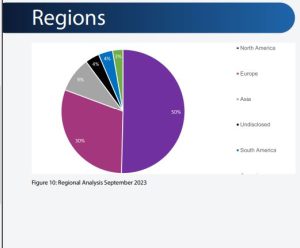
Running parallel with the rest of the year, the top three most targeted regions remain static, with North America coming in at the top with 258 attacks, then Europe with 155, and finally Asia with 47. It is interesting that in relative terms, North America’s targeting has increased by 3% and Europe’s by 2%, while Asia has experienced considerable 6% decrease, which highlights a shift in the threat landscape away from Asia towards Western nations, bringing levels back towards baseline behavior.
Asia’s baseline for hack and leak instances usually hovers around 10% but this deviated in February 2023 and August 2023 to 15%. Therefore, when compared to August, the threat landscape is trending away from Asia towards Western nations bringing levels back to baseline behavior. The remaining regions feature the undisclosed category which has the equivalent percentage of attacks (19 in absolute figures) as August 2023.
This category is characterized by BianLian’s tendency to redact company names before they pay the ransom to further pressurize them into paying. Then we have South America equally with 19 attacks and Africa with just 2. Like the distribution of total attacks for threat actors, where regions are concerned it is similarly a similarly even spread, with the highest contribution being LockBit 3.0’s 42 attacks accounting for 22% of North America’s total figure and is expected behavior. The predominant conclusion to be drawn from September’s activity, it is that the vast total of ransomware attacks in the month cannot be attributed to just one or two threat actors, but the independent efforts of many.
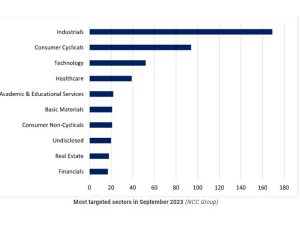
The most targeted sectors were ‘industrials’ with 169 attacks, ‘consumer cyclicals’ with 94, technology with 52, and healthcare with 3.8.
NCC’s report highlights that from January 2023 until September 2023, it has recorded nearly 3,500 attacks, and it’s now likely that the final figure will be close to 4,000 by the end of the year.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind