Cybersecurity researchers are alerting users about phishing email campaigns using a toolkit called “Rockstar 2FA” to steal Microsoft 365 account credentials.
These campaigns use advanced techniques to create fake landing pages resembling real Microsoft 365 login pages. Their main goal is to steal user credentials, targeting Microsoft accounts.
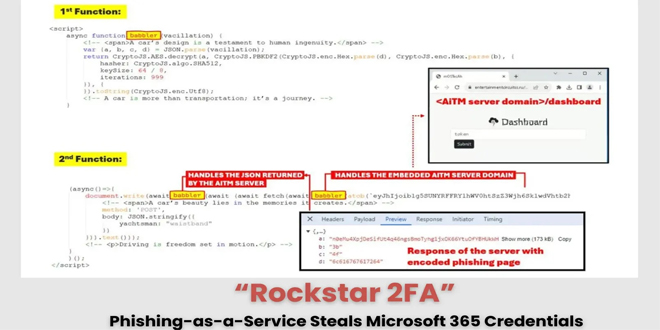
This campaign stands out because it features car-themed web pages, attracting over 5,000 visits to related domains since May 2024.
Rockstar 2FA is an updated phishing kit that uses a PaaS model, making it easily accessible to cybercriminals.
Rockstar 2FA offers features like 2FA bypass, cookie harvesting, antibot protection, login page themes that look like popular services, undetectable links, and Telegram bot integration.
It offers a modern, user-friendly admin panel that lets customers track their phishing campaigns, generate URLs and attachments, and customize themes for their links.
Trustwave has identified email campaigns that use different methods to gain access, including URLs, QR codes, and document attachments. These messages come from compromised accounts or spamming tools and feature various lures, such as file-sharing notifications and e-signature requests.
“This campaign employs an AiTM attack, allowing attackers to intercept user credentials and session cookies, which means that even users with multifactor authentication (MFA) enabled can still be vulnerable,” Trustwave research said.
Rockstar 2FA phishing campaigns use different email delivery methods, like compromised accounts and legitimate services. Because they come from trusted sources, they are less likely to be flagged by traditional filters, making them more effective.
The attacks have impacted users in different sectors and regions, using various phishing themes, such as:
Password/account-related alerts
Voicemail notifications
HR and payroll-related messages
MFA lures
IT department notifications
Document and file-sharing notifications
E-signature platform-themed messages
Threat actors bypass antispam detection using obfuscation methods, FUD links, and QR codes. They also employ Cloudflare Turnstile on their phishing landing pages to block automated analysis.
Researchers found significant domains hosting decoy content on the AiTM server, which show a decoy page when accessed.
Commodity phishing attacks, like those targeting Rockstar 2FA, are common because they are cheap and easy to execute.
AiTM techniques can bypass added security measures such as multifactor authentication (MFA), increasing the risk of account takeovers and business email compromise (BEC) attacks.
Cybersecurity experts warn that ongoing Rockstar-led phishing activities may lead to continuous updates or the creation of more advanced phishing tools, posing ongoing challenges for digital security.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind