By 2028, there will be over 25 billion Internet of Things (IoT) devices. Attackers are increasingly targeting various devices, operating systems, and firmware to gain access. Forescout Technologies, a cybersecurity leader, has released a report called “The Riskiest Connected Devices in 2024.” The report is based on data from 19 million devices and was conducted by Vedere Labs, a research team specializing in uncovering vulnerabilities and threats to critical infrastructure.
“The device has evolved from a pure asset to a reliable, sophisticated, intelligent platform for communications and services, driving a transformation in the relationship between devices, people, and networks,” said Elisa Costante, VP of Threat Research, Forescout.
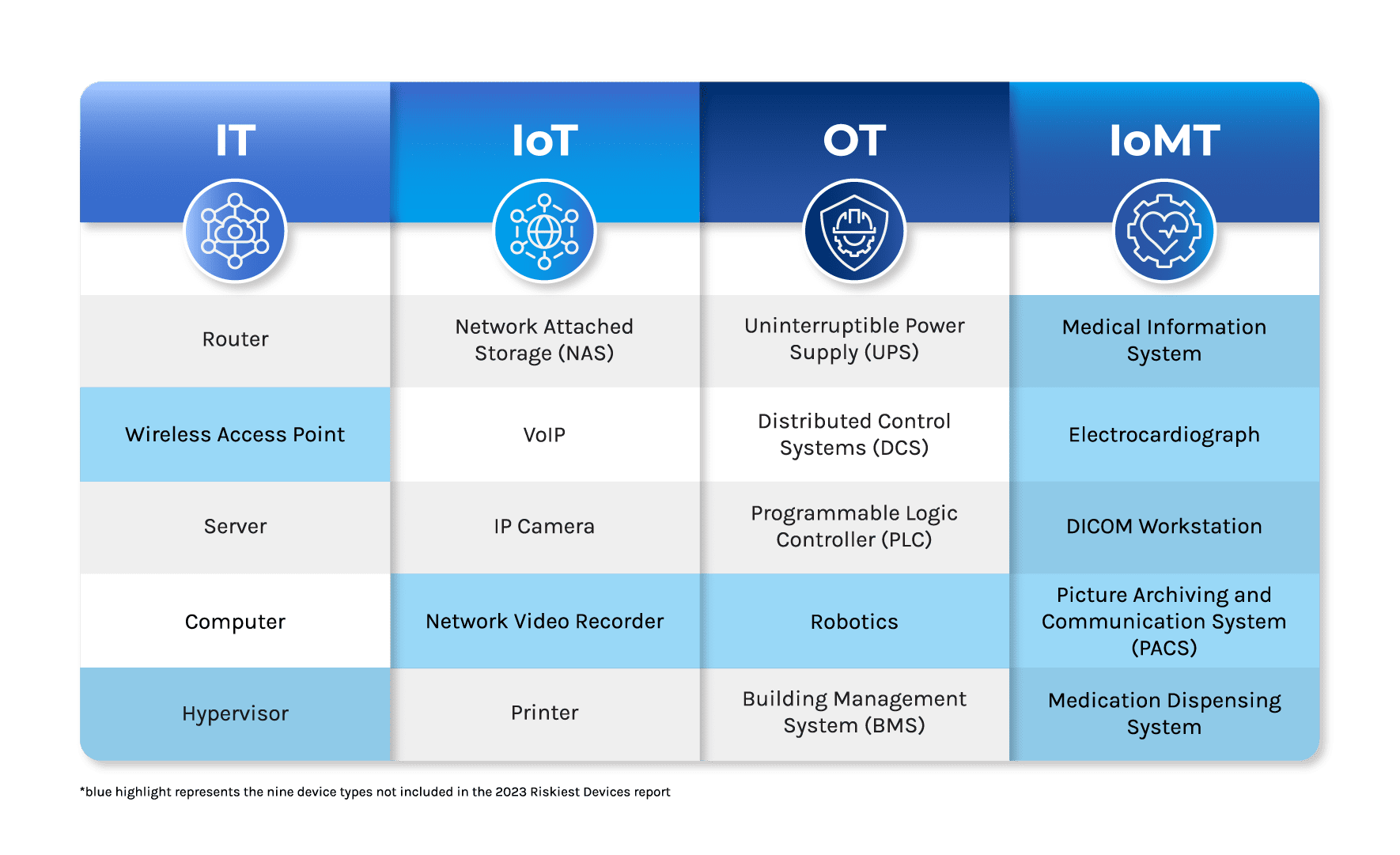
“We analyze millions of data points to publish the Riskiest Connected Devices report to integrate important threat context into how organizations use different devices and to redefine what it means to connect and interact securely. Forescout is committed to delivering device threat intelligence that helps organizations respond faster to potential threats and take advantage of opportunities to enhance security postures.”
The Riskiest Connected Devices in 2024 report lists the top five risky device types in four categories: IT, IoT, OT, and IoMT. Here are the main highlights.
IT devices accounted for 58% of vulnerabilities this year, down from 78% in 2023. At the same time, IoT vulnerabilities increased to 33% from 14%. The most vulnerable types of devices were wireless access points, routers, printers, voice-over-internet-protocol equipment, and IP cameras. Unmanaged devices like VoIP equipment, networking equipment, and printers were identified as highly exposed.
Routers and wireless access points are now more vulnerable than servers and computers, which was not the case in 2023. This change is due to a significant increase in vulnerabilities targeting network infrastructure devices since the second half of 2023.
In industry, technology, education, and manufacturing have the riskiest devices. On the other hand, healthcare has significantly reduced risk by using fewer remote desktop protocols and old Windows versions.
The report shows that the technology sector is the one using the oldest versions of Windows. Education, retail, and healthcare are also mentioned as sectors using old versions.
Attackers commonly target exposed ports such as Server Message Block Protocol, RDP, Secure Shell, and Telnet. Healthcare, technology, and manufacturing sectors have reduced Telnet exposure but increased SSH usage.
Computers, mobile devices, and servers were the most common exposed devices, while VoIP equipment, networking equipment, and printers were the most exposed unmanaged devices.
“The attack surface now encompasses IT, IoT and OT in almost every organization — with IoMT in healthcare,” the report concludes. “It is not enough to focus defenses on risky devices in a single category since attackers can leverage devices of different categories to carry out attacks.”
The report adds, “organizations need new security approaches to identify and reduce risk. Modern risk and exposure management must encompass devices in every category to identify, prioritize and reduce risk across the whole organization.”
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














