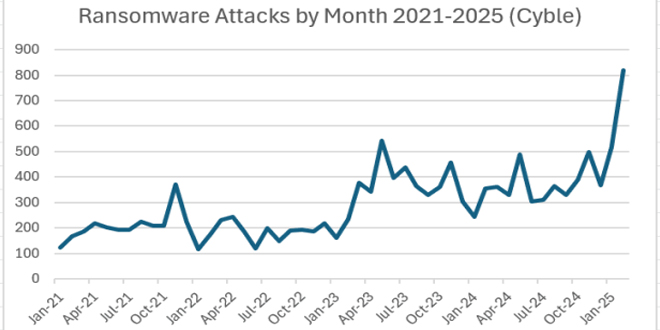
Ransomware attacks reached a record high in February, surpassing previous months, according to a Cyble report. The Cyble report tracked the number of victims listed by ransomware groups on their Tor-based data leak sites (DLS), which are used to shame victims and threaten data release unless ransoms are paid. Although not all victims are included, Cyble suggests that this data provides a valuable insight into ransomware trends.
Cyble reported that February 2025 saw a record number of ransomware attacks, over 50% higher than the previous record from two years earlier.
CL0P Sends Ransomware Attacks to Record Highs
The last peak for ransomware attacks was in May 2023, with 544 victims reported.
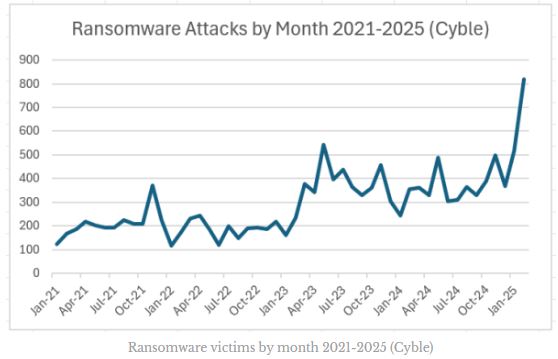
Despite the CL0P ransomware group’s 267 victims, February’s numbers would still be impressive, but with the CL0P victims, the total number of victims claimed by ransomware groups in February hit 821, far beyond previous highs. (image below).
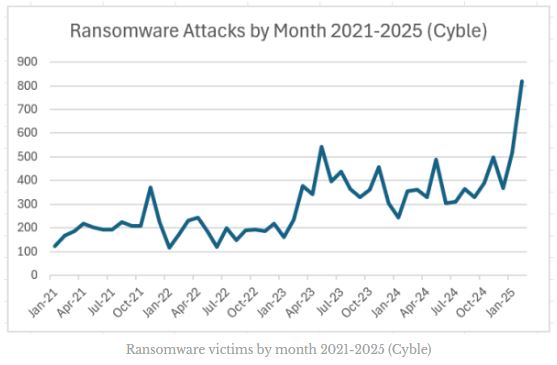
Ransomware victims by month
Ransomware victims by month 2021-2025 (Cyble)
According to Cyble, CL0P has exploited Cleo MFT vulnerabilities, affecting 386 victims. This high number makes CL0P the most active ransomware group of the month, followed by RansomHub and Akira. (chart below).
Most active ransomware groups, February 2025
Most active ransomware groups, February 2025 (Cyble)
The U.S. had significantly more ransomware victims than any other country, with 10 times more than Canada (chart below).
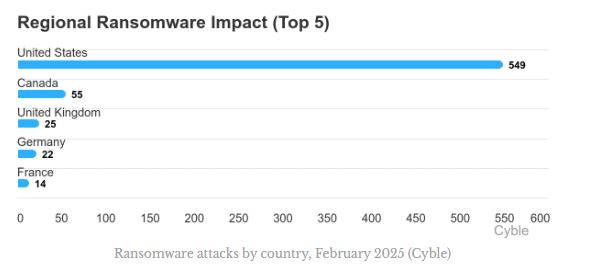
Ransomware attacks by country, February 2025
Ransomware attacks by country, February 2025 (Cyble)
February saw a significant increase in ransomware victims, surpassing long-term trends. Cyble is investigating whether this rise indicates a new, higher level of ransomware attacks by analyzing major ransomware groups for insights.
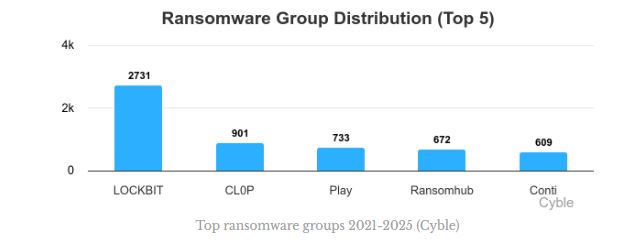
In the past four years, LockBit has outperformed other ransomware groups, claiming over 2,700 victims. However, it has declined significantly in the last year due to global law enforcement actions and is now trying to recover with LockBit 4.0.

Top ransomware groups 2021-2025
Top ransomware groups 2021-2025 (Cyble)
CL0P had significantly fewer victims than the top group, with 901 claimed victims over that four-year period. Play, RansomHub, Conti, and Akira followed with 608 victims each, making them the next most active ransomware groups.
The six-year-old CL0P group has primarily targeted managed file transfer (MFT) vulnerabilities, particularly Cleo and MOVEit. This strategy has resulted in a concentrated group of victims, with over 40% (383) occurring in recent months. Cyble noted that, with only 22 new victims in the past year, CL0P’s victim numbers are likely to keep changing over time.
The report stated that with RansomHub, Akira, Play, and FOG increasing ransomware activity recently, we may have seen a rise in the number of victims claimed by ransomware groups.
Cyble recommends that organizations enhance cyber resilience by patching web vulnerabilities, training employees to identify phishing, and adopting zero trust, network segmentation, monitoring, and ransomware-resistant backups.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind