Security researchers have warned that a Proof-of-Concept (PoC) exploit has been publicly released for a critical vulnerability affecting Oracle WebLogic Server.
The flaw tracked as CVE-2024-21182, poses a significant risk to organizations using the server, as it allows an unauthenticated attacker with network access to compromise the targeted system.
By F2
/ Tuesday , June 24 2025
The U.S. House of Representatives has banned congressional staff from using WhatsApp on government devices due to security concerns, as...
Read More
By F2
/ Tuesday , June 24 2025
Kaspersky found a new mobile malware dubbed SparkKitty in Google Play and Apple App Store apps, targeting Android and iOS....
Read More
By F2
/ Tuesday , June 24 2025
OWASP has released its AI Testing Guide, a framework to help organizations find and fix vulnerabilities specific to AI systems....
Read More
By F2
/ Tuesday , June 24 2025
In a major milestone for the country’s digital infrastructure, Axentec PLC has officially launched Axentec Cloud, Bangladesh’s first Tier-4 cloud...
Read More
By infosecbulletin
/ Monday , June 23 2025
A hacking group reportedly linked to Russian government has been discovered using a new phishing method that bypasses two-factor authentication...
Read More
By infosecbulletin
/ Wednesday , June 18 2025
Russian cybersecurity experts discovered the first local data theft attacks using a modified version of legitimate near field communication (NFC)...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
Cybersecurity researcher Jeremiah Fowler discovered an unsecured database with 170,360 records belonging to a real estate company. It contained personal...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
GreyNoise found attempts to exploit CVE-2023-28771, a vulnerability in Zyxel's IKE affecting UDP port 500. The attack centers around CVE-2023-28771,...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently included two high-risk vulnerabilities in its Known Exploited Vulnerabilities (KEV)...
Read More
By infosecbulletin
/ Monday , June 16 2025
SafetyDetectives’ Cybersecurity Team discovered a public post on a clear web forum in which a threat actor claimed to have...
Read More
The vulnerability impacts Oracle WebLogic Server versions 12.2.1.4.0 and 14.1.1.0.0, among the most widely used middleware solutions for deploying enterprise applications.
The exploitation is possible through T3 and IIOP (Internet Inter-ORB Protocol), which are commonly enabled by default for remote communication.
Cybersecurity advisors have highlighted that this vulnerability is classified as “easily exploitable.”
An attacker can leverage it without requiring credentials or sophisticated technical expertise, broadening the scope of potential misuse.
According to the advisory, successful exploitation could lead to arbitrary code execution, granting attackers full control over the compromised server.
Concerns surrounding CVE-2024-21182 grew rapidly after an exploit was shared on GitHub by a user named “k4it0k1d.”
The repository includes a ready-to-use PoC that lowers the barrier for potential attackers. Cybersecurity updates posted on social media platforms, such as X (formerly Twitter), have also drawn attention to the vulnerability.
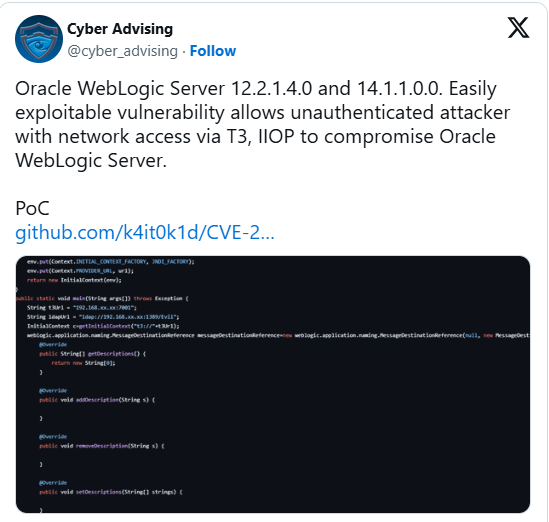
A post shared by Cyber Advising includes a link to the exploit and warns of its accessibility.
With the exploit now public, proactive defense measures are critical to protecting sensitive systems and data.

 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














