Cybersecurity researchers at ThreatFabric have identified a new and more dangerous variant of the Octo banking malware, called “Octo2.” This evolved version of ExobotCompact is already targeting European financial institutions, with attacks reported in Italy, Poland, Moldova, and Hungary. Octo2 features improved remote access and advanced anti-detection methods, making it a serious threat to mobile banking users in the area.
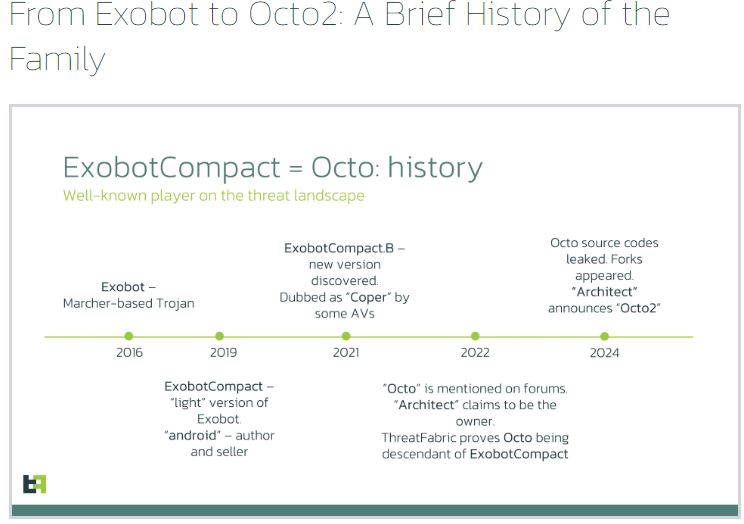
Initially called Exobot in 2016, this malware family has evolved into a major mobile banking threat. Its predecessor, Octo, was known for overlay attacks and intercepting notifications. The new version, Octo2, has enhanced remote access tools for full device takeover and unauthorized transactions.
Malware developers have improved the stability of remote control sessions by adding a “low-quality” setting, allowing attackers to maintain connections on weak networks. This enhancement enables Octo2 to execute attacks even in poor conditions, ensuring reliable device access.
In early 2024, ThreatFabric uncovered the first Octo2 campaigns that pretended to be legitimate apps like Google Chrome and NordVPN. When installed, these fake apps introduced Zombinder, enabling Octo2 to bypass Android 13+ security by pretending to be an essential plugin.
After installation, Octo2 can intercept push notifications and hide them from the user, which cybercriminals use to prevent important security alerts. Its operators plan to expand its reach beyond Europe to target users in the U.S., Canada, Singapore, and elsewhere.

Octo2 uses a Domain Generation Algorithm (DGA) to create various command-and-control (C2) domain names, making it difficult for security systems to block. It also employs a unique encryption method, generating a new cryptographic key for each communication with the C2 server, complicating efforts to monitor its traffic.
Octo2 uses advanced obfuscation techniques, including multiple encryption layers and dynamic loading of malicious libraries, to avoid detection by security researchers.
With the spread of Octo2 campaigns, mobile users and financial institutions must stay vigilant. The malware poses a serious threat due to its stealthy execution of targeted attacks.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














