Sygnia’s recent report highlights the changing strategies of ransomware groups targeting VMware ESXi appliances. These attackers exploit vital virtual infrastructure to disrupt operations and remain hidden in compromised networks.
ESXi appliances have become prime targets due to their role in hosting vital virtual machines. “Damaging them renders virtual machines inaccessible, severely disrupting the business operations of affected organizations,” notes Sygnia.
By infosecbulletin
/ Wednesday , September 17 2025
A threat actor claims to have breached Link3, a major IT solutions and internet service provider based in Bangladesh. The...
Read More
By infosecbulletin
/ Wednesday , September 17 2025
Check point, a cyber security solutions provider hosts an event titled "securing the hyperconnected world in the AI era" at...
Read More
By infosecbulletin
/ Tuesday , September 16 2025
Cross-Site Scripting (XSS) is one of the oldest and most persistent vulnerabilities in modern applications. Despite being recognized for over...
Read More
By infosecbulletin
/ Monday , September 15 2025
Every day a lot of cyberattack happen around the world including ransomware, Malware attack, data breaches, website defacement and so...
Read More
By infosecbulletin
/ Monday , September 15 2025
A critical permission misconfiguration in the IBM QRadar Security Information and Event Management (SIEM) platform could allow local privileged users...
Read More
By infosecbulletin
/ Monday , September 15 2025
Australian banks are now using bots to combat scammers. These bots mimic potential victims to gather real-time information and drain...
Read More
By infosecbulletin
/ Saturday , September 13 2025
F5 plans to acquire CalypsoAI, which offers adaptive AI security solutions. CalypsoAI's technology will be added to F5's Application Delivery...
Read More
By infosecbulletin
/ Saturday , September 13 2025
The Villager framework, an AI-powered penetration testing tool, integrates Kali Linux tools with DeepSeek AI to automate cyber attack processes....
Read More
By infosecbulletin
/ Saturday , September 13 2025
Samsung released its monthly Android security updates, addressing a vulnerability exploited in zero-day attacks. CVE-2025-21043 (CVSS score: 8.8) is a...
Read More
By infosecbulletin
/ Saturday , September 13 2025
Albania has appointed the first AI-generated government minister to help eliminate corruption. Diella, the digital assistant meaning Sun, has been...
Read More
Ransomware operators use ESXi devices to secretly tunnel malicious traffic within networks, often avoiding detection because of minimal monitoring.
The report highlights SSH tunneling as a tactic where attackers create a semi-persistent backdoor by using stolen admin credentials or vulnerabilities to access ESXi devices.
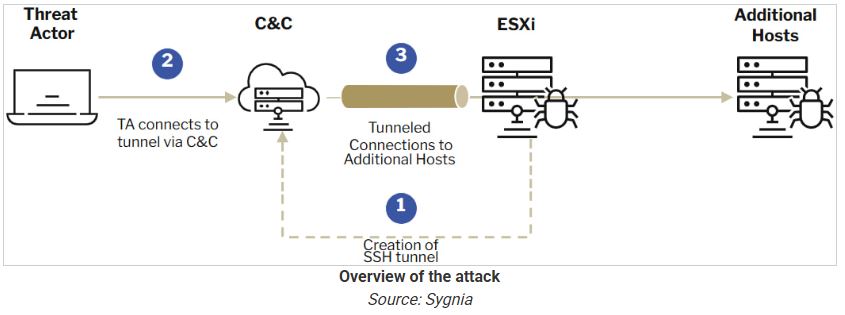
Threat actors use SSH to create a remote port-forwarding SOCKS tunnel, allowing them to mix malicious traffic with legitimate activity.
Sygnia explains, “Since ESXi appliances are resilient and rarely shutdown unexpectedly, this tunneling serves as a semi-persistent backdoor within the network.”
This method lets attackers avoid security measures and keep access for a long time.
ESXi’s logging structure complicates forensic investigations. Unlike traditional syslogs, ESXi organizes logs by activity, spreading critical events across multiple files, such as /var/log/shell.log, /var/log/auth.log, and /var/log/hostd.log. Sygnia emphasizes, “Configuring syslog forwarding from the ESXi server to an external syslog server can solve the issue.”
The report shows how Abyss Locker ransomware exploits ESXi appliances. Attackers exploited ESXi devices and NAS for network access, highlighting the importance of strong monitoring and defense strategies.

 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














