A critical flaw in Google’s “Sign in with Google” system has put millions of Americans at risk of data theft. This vulnerability primarily impacts former employees of startups that have shut down.
Truffle Security identifies that the issue arises from how Google’s OAuth login handles changes in domain ownership.
When a startup fails and its domain is available for purchase, anyone who buys it can recreate email accounts for former employees.
These recreated accounts can’t access old email data but can log into previous SaaS products used by the organization.
To demonstrate the severity of this issue, a security researcher purchased a defunct startup’s domain and successfully logged into multiple services, including:
ChatGPT
Slack
Notion
Zoom
HR systems (containing social security numbers)
The most alarming breaches involved HR systems, which contained sensitive information like tax documents and social security numbers.
Interview platforms contained confidential candidate feedback and hiring decisions, while chat platforms exposed private messages and sensitive communications.
The scale of this vulnerability is staggering:
Approximately 6 million Americans currently work for tech startups
90% of tech startups eventually fail
50% of those startups rely on Google Workspaces for email
An analysis of Crunchbase’s startup dataset revealed over 100,000 domains from failed startups currently available for purchase.
With an average of 10 employees per startup and 10 different SaaS services used, this vulnerability could risk sensitive data from over 10 million accounts.
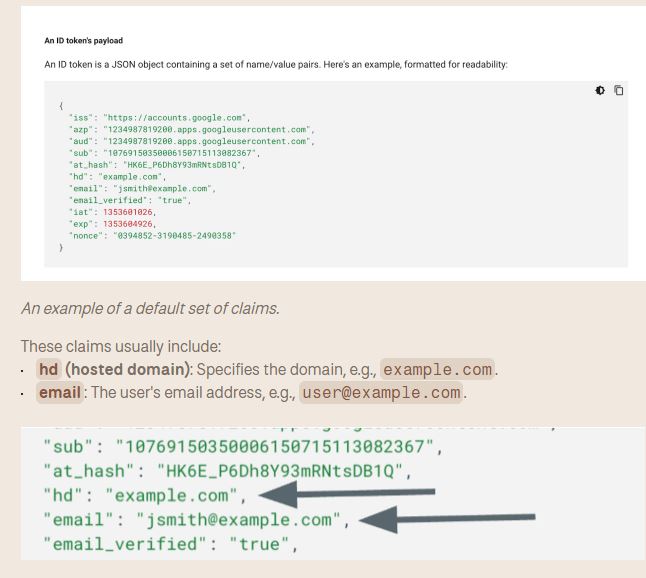
The issue stems from how service providers like Slack handle user authentication, primarily using two claims from Google’s OAuth: the HD (hosted domain) claim and the email claim.
The HD claim provides access to anyone from a certain domain, while the email claim logs users into their accounts. If domain ownership changes, these claims don’t reset, allowing new owners to access former employees’ accounts.
A potential solution proposed to Google involves implementing two immutable identifiers within its OpenID Connect (OIDC) claims:
A unique user ID that remains constant over time
A unique workspace ID tied to the domain
Despite the researcher reporting this vulnerability to Google’s security team, the initial response was to mark it as “Won’t fix.” It was only after the issue gained wider attention that Google reopened the case.
As of now, there is no comprehensive fix for this vulnerability. Downstream providers like Slack cannot fully protect against this issue unless Google implements the proposed OIDC claims.
Former startup employees lose control over their data protection when they leave the company, making them vulnerable to the startup’s future and ownership. This security flaw highlights the need for stronger authentication systems and the risks of using third-party login services.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind