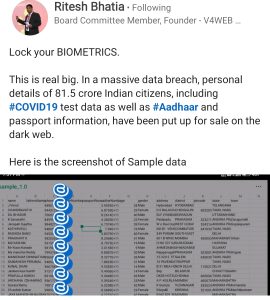
A report found that someone, using the name ‘X’ on Twitter, exposed a data breach. This person advertised the stolen database on a dark web forum. The database contains records of 81.5 million Indian citizens, including sensitive information like Aadhaar and passport details, names, phone numbers, and addresses. The person who exposed the breach claimed that the data was taken from Covid-19 test records of Indian citizens and came from ICMR.
 ICMR has faced many cyber-attacks since February. Over 6,000 incidents were reported last year. Central agencies and the council were aware of these threats. They urged ICMR to take corrective measures to prevent data breaches.
ICMR has faced many cyber-attacks since February. Over 6,000 incidents were reported last year. Central agencies and the council were aware of these threats. They urged ICMR to take corrective measures to prevent data breaches.
A query, calls and messages sent to ICMR DG on Saturday remained unanswered and his response is awaited.
It has been learnt that CERT-In has informed ICMR about the breach and the verification of sample data, which is on sale, matches with the actual data of ICMR after which all agencies were ropes in.
Officials from various agencies and ministries are working together to address the serious situation. A top-tier agency is conducting a thorough investigation to determine if foreign actors are responsible. Actions have already been taken to fix the issue and procedures have been implemented to reduce the damage.
The report stated that the source of the leak has not yet been found. Covid-19 test data is shared among the National Informatics Centre (NIC), ICMR, and the Ministry of Health.
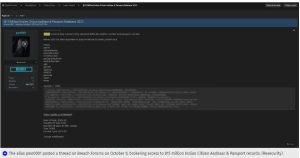
According to the American cybersecurity and intelligence agency Resecurity, a hacker called ‘pwn0001′ posted on Breach Forums on October 9, offering access to 815 million records of Indian citizens’ Aadhaar and Passport details. This is significant considering India’s total population is over 1.486 billion people.
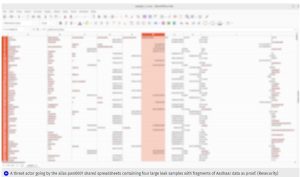
News18 reported that Pwn0001 shared spreadsheets containing four significant leak samples, including parts of Aadhaar data. Resecurity stated that one of these leaked samples contained 100,000 records of Personally Identifiable Information (PII) related to Indian residents. The leaked sample confirmed the validity of Aadhaar Card IDs through a government portal’s “Verify Aadhaar” feature. Instances of India’s health system being a target for hackers have been observed previously.
“Media disclaimer: This report is based on research from various sources. It’s important to note that the information provided here is for reference only. Users are responsible for their reliance on this information. Infosecbulletin does not guarantee its accuracy and is not liable for any consequences that may arise from using it.”
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














