LockBit ransomware creators were working on a new version of their file-encrypting malware, called LockBit-NG-Dev, possibly to be known as LockBit 4.0, before law enforcement dismantled their
operation this week.
Multiple Versions:
“Security experts said LockBit previously released various versions of its ransomware:”
By F2
/ Tuesday , June 24 2025
The U.S. House of Representatives has banned congressional staff from using WhatsApp on government devices due to security concerns, as...
Read More
By F2
/ Tuesday , June 24 2025
Kaspersky found a new mobile malware dubbed SparkKitty in Google Play and Apple App Store apps, targeting Android and iOS....
Read More
By F2
/ Tuesday , June 24 2025
OWASP has released its AI Testing Guide, a framework to help organizations find and fix vulnerabilities specific to AI systems....
Read More
By F2
/ Tuesday , June 24 2025
In a major milestone for the country’s digital infrastructure, Axentec PLC has officially launched Axentec Cloud, Bangladesh’s first Tier-4 cloud...
Read More
By infosecbulletin
/ Monday , June 23 2025
A hacking group reportedly linked to Russian government has been discovered using a new phishing method that bypasses two-factor authentication...
Read More
By infosecbulletin
/ Wednesday , June 18 2025
Russian cybersecurity experts discovered the first local data theft attacks using a modified version of legitimate near field communication (NFC)...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
Cybersecurity researcher Jeremiah Fowler discovered an unsecured database with 170,360 records belonging to a real estate company. It contained personal...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
GreyNoise found attempts to exploit CVE-2023-28771, a vulnerability in Zyxel's IKE affecting UDP port 500. The attack centers around CVE-2023-28771,...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently included two high-risk vulnerabilities in its Known Exploited Vulnerabilities (KEV)...
Read More
By infosecbulletin
/ Monday , June 16 2025
SafetyDetectives’ Cybersecurity Team discovered a public post on a clear web forum in which a threat actor claimed to have...
Read More
LockBit version 1.0 was released in January 2020 and originally known as “ABCD” ransomware.
LockBit version 2.0, aka “Red,” was released in June 2021 together with StealBit, the group’s primary data exfiltration tool.
LockBit Linux was released in October 2021 to infect Linux and VMWare ESXi systems.
LockBit version 3.0, aka “Black,” was released in March 2022 and leaked six months later by the group’s disgruntled developer, leading to multiple knockoffs.
LockBit Green was released in January 2023 and heralded as being a major new version, which security experts quickly dispelled, finding it to be a rebranded version of a Conti encryptor.

LockBit next-gen:
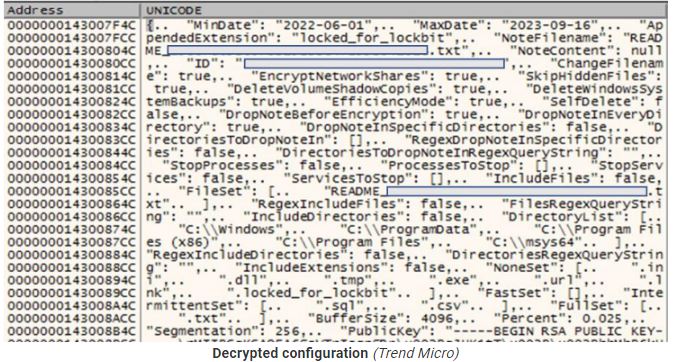
Trend Micro provides a JSON configuration file containing relevant execution parameters and operational flags.
The security firm says the new encryptor is in its final development stages, even though it doesn’t have all the features of previous versions, like the ability to spread on breached networks and print ransom notes. However, it already has most of the expected functionality.
It has three encryption modes (using AES+RSA): “fast,” “intermittent,” and “full.” ItIt supports three encryption modes (using AES+RSA), namely “fast,” “intermittent,” “full,” and “intermittent intermittent,” has custom file or directory exclusion, and can randomize the file naming to complicate restoration efforts.
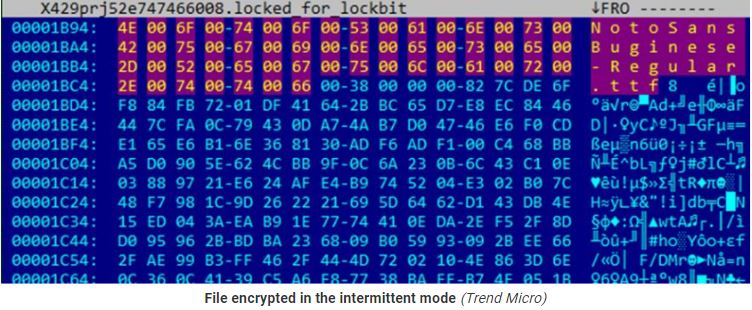
Additional options include a self-delete mechanism that overwrites LockBit’s own file contents with null bytes.
Trend Micro published a detailed analysis of the LockBit-NG-Dev malware, including its configuration parameters.
Source: Trend Micro research


 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind















