Bank Rakyat Indonesia (BRI), the largest state bank by assets, has assured customers that their data and funds are secure and that normal transactions continue uninterrupted, despite rumors of a ransomware attack on social media.
On Wednesday evening, BRI’s Director of Digital and IT, Arga M. Nugraha, confirmed via Instagram that the bank’s systems are fully operational.
“We confirm that both customer data and funds are secure. All BRI banking systems are functioning normally, and our transaction services are operating smoothly,” Arga said in the statement.
He assured customers that they can continue using BRI’s banking services, including digital platforms like BRImo, QLola, ATMs, CRMs, and more, with full data security.
The bank stated that its information security systems meet international standards and are regularly updated to tackle new threats.
“Proactive measures are in place to ensure that customer information remains protected,” Arga added.
The statement follows social media rumors on Wednesday evening about a possible data breach at BRI.
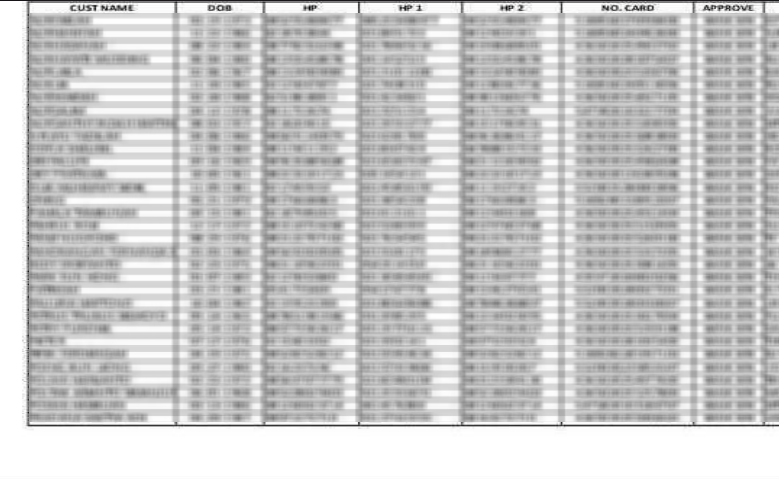
The attack is thought to be connected to Bashe Ransomware, which has ties to the infamous LockBit group responsible for breaching Indonesia’s National Data Center in June.
Bashe Ransomware mainly targets high-value sectors such as technology, business services, manufacturing, finance, transportation, and healthcare. Its attacks occur in North America and Europe.
Bashe Ransomware usually spreads via phishing emails with malware. When a victim opens the email, the malware quickly encrypts their data across the network. Victims must pay a ransom to access their files again.
Source: darkwebinformer, jakartaglobe, indonesiabusinesspost
((Media Disclaimer: This report is based on research conducted internally and externally using different ways. The information provided is for reference only, and users are responsible for relying on it. Infosecbulletin is not liable for the accuracy or consequences of using this information by any means))
Uganda confirms hack of central bank accounts, Refutes $17 Million Claim
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














