India’s Communications Minister Chandra Sekhar Pemmasani confirmed a breach at the state-owned telecom operator BSNL on May 20 during a session in the Lok Sabha on July 24. The Minister provided this information in a written response to a question from Congress MP Amar Singh.
CERT-In, India’s national agency for incident response, detected a possible intrusion and data breach at BSNL. Minister Pemmasani confirmed that although the breach did not cause any service disruptions, one BSNL server was found to contain data that resembled the sample data provided by CERT-In.
According to Hindustan times, “The same was analysed and found that one File Transfer Protocol (FTP) server had the data similar to the sample data shared by CERT-In. No breach into the Home Location Register (HLR) of the telecom network has been reported by the equipment manufacturer, hence no service outage in BSNL’s network,” the minister said.
The government formed a committee to investigate telecom networks. The committee will audit the networks and suggest ways to prevent future breaches.
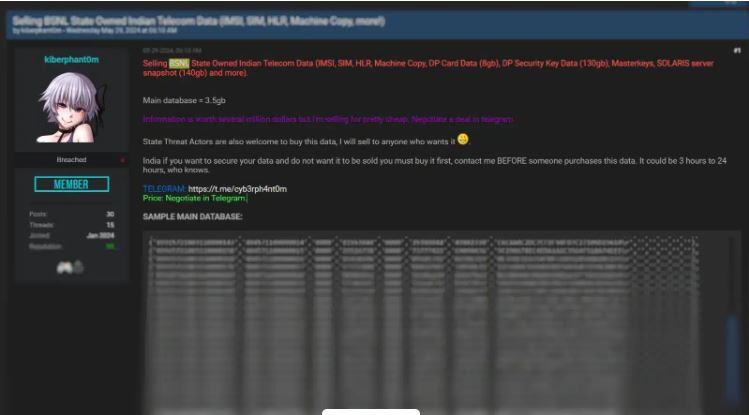
Previously Infosecbulletin reported, according to digital risk management firm Athenian Technology, BSNL, India’s state-owned telecom provider, suffered a significant data breach. A cybercriminal named “kiberphant0m” performed the attack, resulting in the exposure of a large amount of sensitive data. This puts millions of users at risk.
Zee news reported, Kanishk Gaur, CEO of Athenian Technology stated that the data breach at BSNL was carried out by a threat actor named ‘kiberphant0m’, as per report by ET. Gaur further explained, The breach involved over 278 GB of data from BSNL’s telecom operations. This includes server snapshots which could be used for activities like SIM cloning and extortion.
The report reveals that the cybercriminal responsible for the BSNL data breach is selling the stolen data for $5,000. This offer was available only from May 30 to May 31, 2024.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














