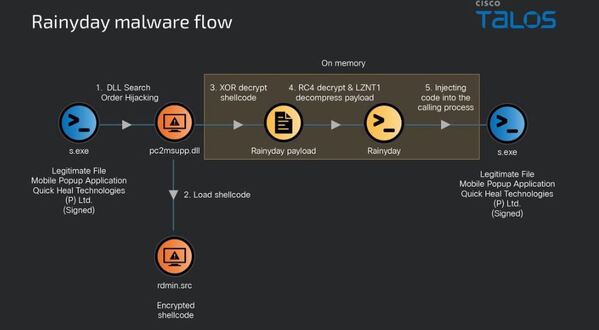
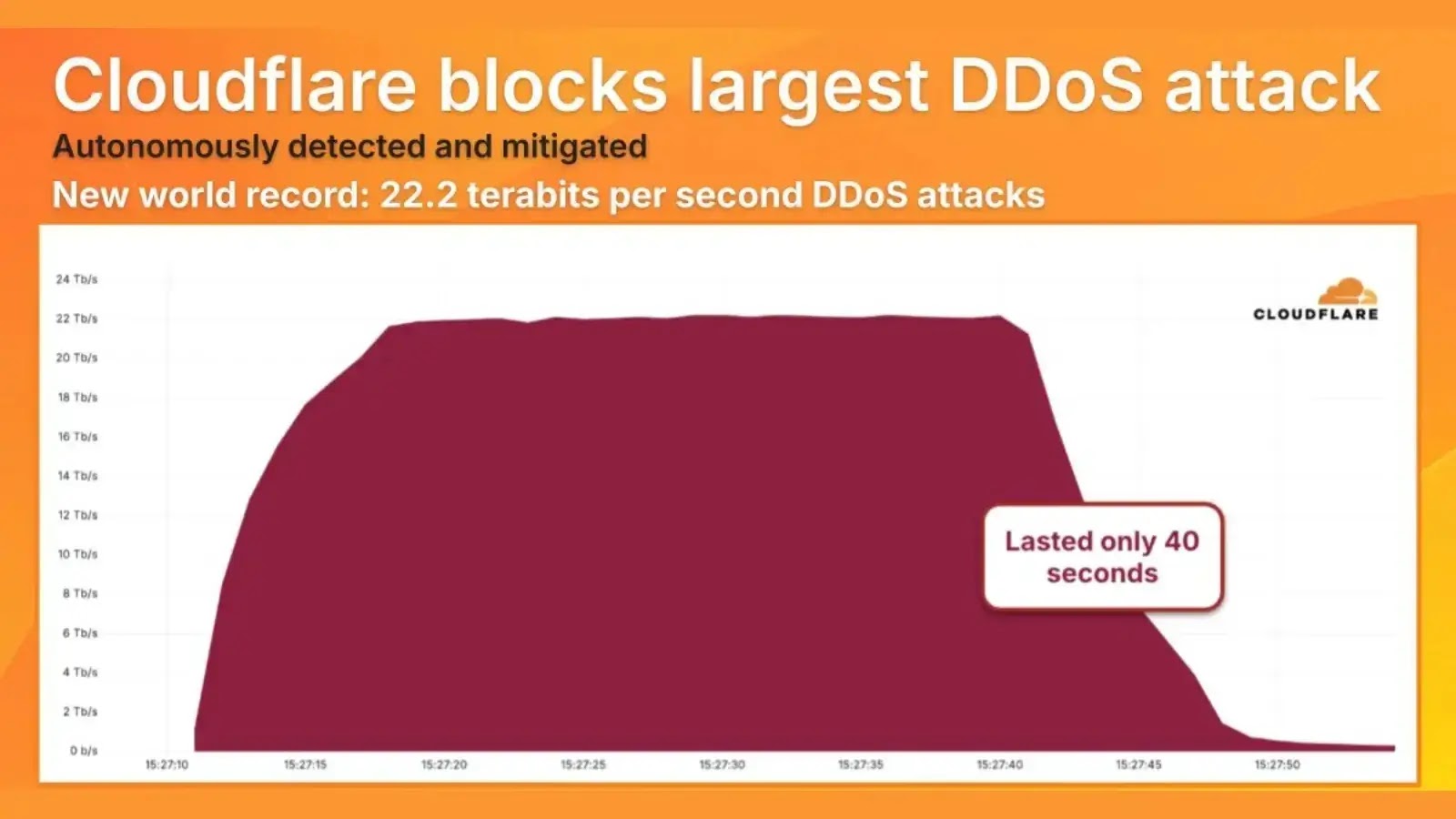
A cyber attack on the financial services division of China’s biggest bank has caused disruptions in the US Treasury market. Clients of the Industrial and Commercial Bank of China have had to redirect their trades.
ICBC Financial Services, a member of the Securities Industry and Financial Markets Association, was targeted by ransomware software. This type of software immobilizes computer systems until a payment is made.
An attack affected ICBC FS’s ability to settle Treasury trades for other market participants. As a result, some equity trades were also influenced. Hedge funds and asset managers had to redirect their trades due to the disruption caused by the attack. Although the incident affected Treasury market liquidity to some extent, it did not cause significant harm to the overall functioning of the market.
A notice on ICBC FS’s website on Thursday evening confirmed that it had “experienced a ransomware attack that resulted in disruption to certain [financial services] systems” starting on Wednesday.
ICBC FS said it had contained the incident by disconnecting and isolating affected systems, adding that it was “conducting a thorough investigation and . . . progressing its recovery efforts” with the help of information security experts.
ICBC FS cleared US Treasury trades executed on Wednesday and repo financing trades done on Thursday. The notice clarified that ICBC FS operates independently from ICBC in China, and that neither the head office nor the New York branch of ICBC itself were affected.
A Treasury department spokesperson said: “We are aware of the cyber security issue and are in regular contact with key financial sector participants, in addition to federal regulators. We continue to monitor the situation.”
“This is a large party on [the Fixed Income Clearing Corporation], so [it is] certainly of major concern, and potentially impacting liquidity of US Treasuries,” said an executive at a large bank that clears US Treasuries. The Fixed Income Clearing Corporation handles the settlement and clearing of US Treasury trades.
Other experts in the Treasury market also mentioned that traders often have relationships with multiple banks, so they were able to reroute trades to other banks and execute them successfully. Kevin McPartland, head of market structure and technology research at Coalition Greenwich, said, “Everyone has a backup plan in these situations.”
Treasury bond yields went up quickly on Thursday afternoon due to a bad auction for 30-year bonds. The 30-year yield increased by 0.12 percentage points to 4.78%. It’s not clear if the auction was influenced by the attack on ICBC FS.
The company reported the incident to the police. Ransomware attacks have increased during the coronavirus pandemic because remote working has made businesses more vulnerable and cyber criminal groups have become more organized.
Allan Liska, a threat intelligence analyst at cyber security company Recorded Future, mentioned that it is very rare for a bank the size of ICBC FS to be affected in this manner. He also pointed out that the financial sector invests more in protecting against cyber attacks compared to any other industry.
LockBit 3.0 software was used in the attack, as confirmed by two sources. This software was developed by LockBit, a notorious cybercriminal group known for carrying out damaging attacks on ION, the City of London, and the Royal Mail.
The group, believed to operate out of Russia and eastern Europe, also rents out its software to affiliates, a model known as RaaS, or ransomware as a service. It was unclear if Thursday’s hack was carried out by the criminal group or one of its customers.
Earlier on Thursday, Allen & Overy confirmed it was hit by a ransomware attack on its servers. The “magic circle” law firm said it was investigating the impact of the attack and informing affected clients.
Source: Financial Times
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind