A covert attack on ATM systems has been detected, using a hidden Raspberry Pi to access internal bank networks. The intrusion involved physical access, a rarely seen anti-forensics technique and malware designed to avoid standard detection methods.

Attackers Gained Physical Access to ATM Network:
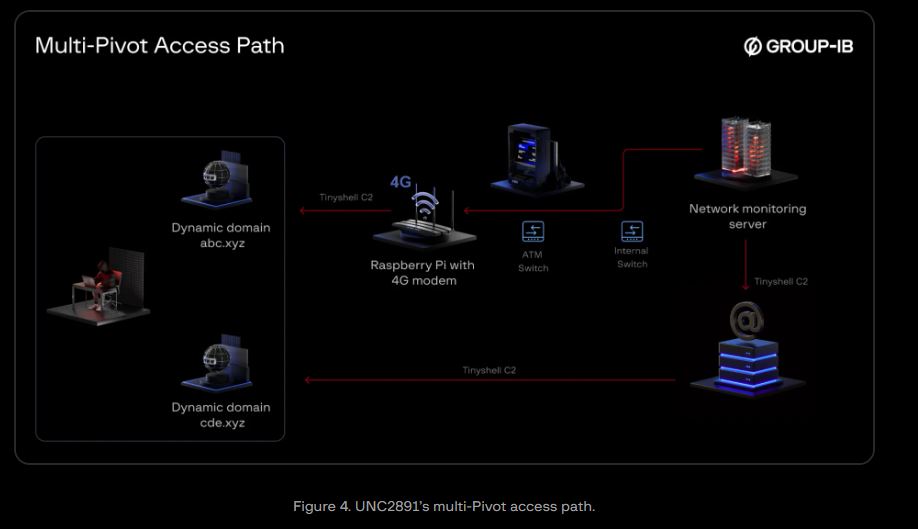
A group named UNC2891 connected a Raspberry Pi to a network switch shared with an ATM. With a 4G modem, the device enabled attackers to remotely access the bank’s internal network, avoiding perimeter firewalls.
Attackers used a backdoor named TINYSHELL to create outgoing connections through a dynamic DNS domain. This gave them continuous external access and enabled ongoing communication with command-and-control (C2) systems.
Forensic analysts at Group-IB noticed regular beaconing every 600 seconds, but no suspicious processes appeared during the initial assessment. This prompted a deeper look into system behavior during idle times.
Malware Masked as Legitimate System Process:
Deeper analysis revealed a stealthy malware component masquerading as a legitimate system process.
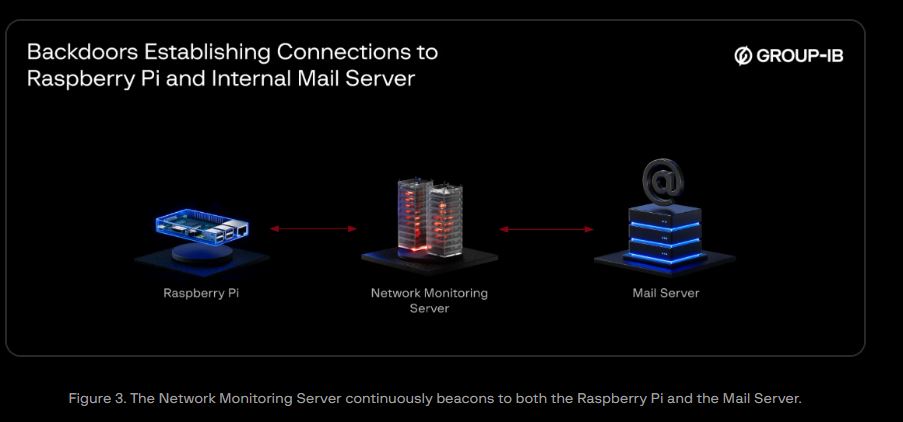
Two instances of a process named “lightdm” were found running from unusual locations, /tmp/lightdm and /var/snap/.snapd/lightdm. These backdoor processes appeared normal at a glance but were actually establishing connections to the Raspberry Pi and the bank’s internal mail server.
The malware used a technique called T1564.013 from MITRE ATT&CK. It exploited Linux bind mounts to hide the backdoor from process listings, evading most forensic tools.
ATM Switching Server and HSM Manipulation Aims:
UNC2891 aimed to hack the ATM switching server to install a rootkit called CAKETAP, designed to fake authorization responses from hardware security modules and enable fraudulent ATM withdrawals.
The attackers were stopped before achieving their goal, but the investigation uncovered important insights.
They kept access via the Raspberry Pi and the bank’s mail server, using a dynamic DNS to hide changes and prevent disruption.
The network monitoring server connected to almost every system in the data center, enabling lateral movement within the environment.
Detection and Response Recommendations
Group-IB advised organizations to:
Monitor mount and unmount syscalls with tools like auditd or eBPF
Alert on /proc/[pid] mounted to tmpfs or external filesystems
Block or monitor binaries executed from /tmp or .snapd directories
Secure all physical switch ports and ATM-connected infrastructure
Capture memory images in addition to disk during incident response
The case demonstrates how financially motivated attackers are adapting their methods. It reveals that physical access, along with hidden Linux features and memory-based malware, can compromise even secure systems.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














