A passback vulnerability has been found in some Canon printers, including production and multifunction models. If an attacker gains administrative access, they could obtain sensitive authentication information, including SMTP and LDAP connections.
Affected Products:
By infosecbulletin
/ Friday , June 13 2025
SoftBank has disclosed that personal information of more than 137,000 mobile subscribers—covering names, addresses, and phone numbers—might have been leaked...
Read More
By infosecbulletin
/ Friday , June 13 2025
Serious security vulnerabilities in Trend Micro Apex One could allow attackers to inject malicious code and elevate their privileges within...
Read More
By infosecbulletin
/ Thursday , June 12 2025
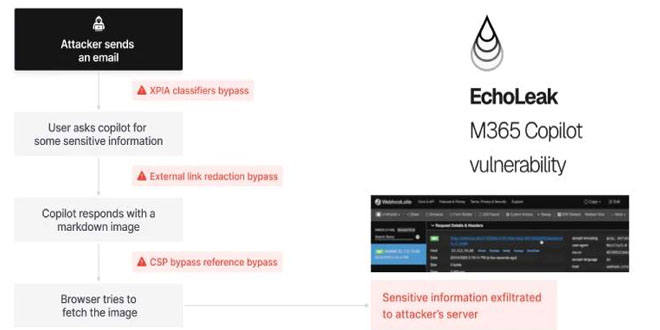
Aim Labs discovered a zero-click AI vulnerability named “EchoLeak” in Microsoft 365 Copilot and reported several ways to exploit it...
Read More
By infosecbulletin
/ Wednesday , June 11 2025
On Tuesday, Adobe released security updates for 254 vulnerabilities in its software, mainly affecting Experience Manager (AEM). There are 254...
Read More
By infosecbulletin
/ Wednesday , June 11 2025
A new report from Bitsight reveals that over 40,000 internet-connected security cameras around the world are exposed, broadcasting live footage...
Read More
By infosecbulletin
/ Wednesday , June 11 2025
Microsoft's June Patch Tuesday update has arrived, addressing 66 vulnerabilities across its product line. One of these flaws was actively...
Read More
By infosecbulletin
/ Tuesday , June 10 2025
More than 84,000 Roundcube webmail installations are at risk due to CVE-2025-49113, a severe remote code execution (RCE) vulnerability that...
Read More
By infosecbulletin
/ Monday , June 9 2025
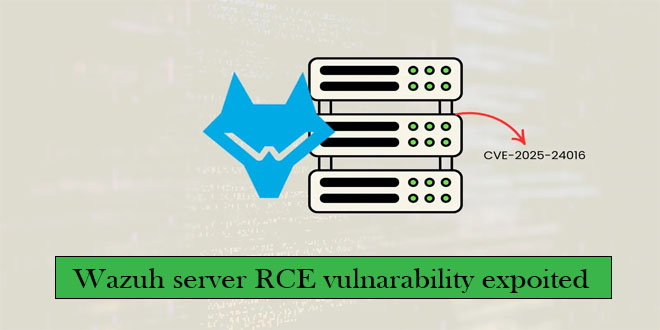
The Security Intelligence and Response Team (SIRT) at Akamai has found that multiple Mirai-based botnets are exploiting CVE-2025-24016, a critical...
Read More
By infosecbulletin
/ Sunday , June 8 2025
On June 5, 2025, CISA released seven advisories regarding Industrial Control Systems (ICS) that highlight current security issues, vulnerabilities, and...
Read More
By infosecbulletin
/ Sunday , June 8 2025
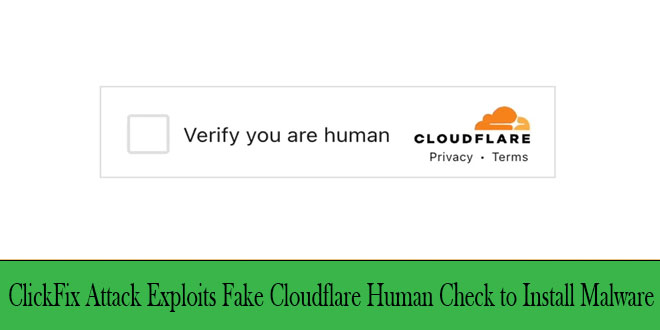
A new social engineering attack uses familiar security checks to trick users into downloading malware via fake Cloudflare verification pages....
Read More
imageRUNNER ADVANCE Series
imageRUNNER Series
imagePRESS V Series
imagePRESS Series
imageCLASS Series
i-sensys Series
Satera Series
Mitigation/Remediation:
To ensure the security of our customers’ print infrastructure, Canon recommends following these guidelines:
- Avoid connecting products directly to public internet networks. Instead, when connecting to the internet, use a private IP address in an environment where the internet can be accessed from a secure private network, built with firewall products, wired routers or Wi-Fi routers.
- Change the product’s default password to a new password.
- Set up administrator and general user IDs and passwords.
- Ensure that passwords and other similar settings for various functions are sufficiently difficult to guess.
- If the product has single or multi-factor authentication functions, use them to confirm the identity of the end-user who is using the product.
- Be aware of physical security needs, including those related to the location of the product etc.
Canon advises to see here for more information on securing products when For enhanced security, some products have special features. More details are available on local Canon websites.
Palo Alto Networks Warns of XSS Flaw: PoC Released
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind