Chinese AI startup DeepSeek has exposed two databases with sensitive user and operational information from its DeepSeek-R1 LLM model.
Unsecured ClickHouse instances are believed to have exposed over a million log entries that include user chat histories in plaintext, along with API keys, backend information, and operational metadata.
Wiz Research found this vulnerability while assessing DeepSeek’s external infrastructure for security.
The security firm discovered two public database instances at oauth2callback.deepseek.com:9000 and dev.deepseek.com:9000 that allowed anyone to run SQL queries through a web interface without needing authentication.
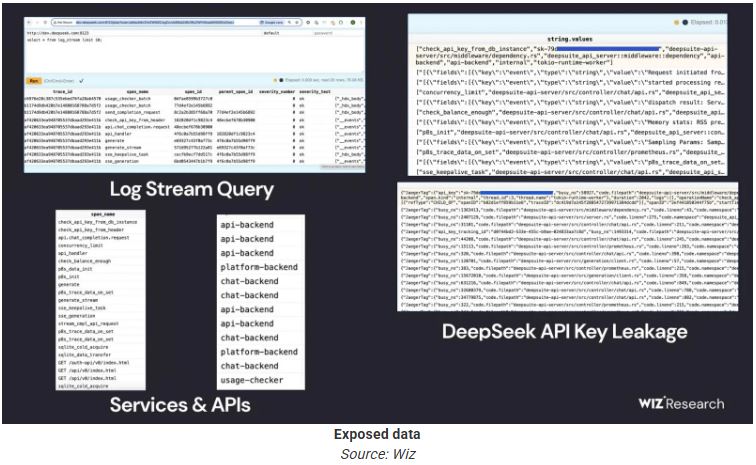
The databases contained a ‘log_stream’ table that stored sensitive internal logs dating from January 6, 2025, containing:
user queries to DeepSeek’s chatbot,
keys used by backend systems to authenticate API calls,
internal infrastructure and services information,
and various operational metadata.
“This level of access posed a critical risk to DeepSeek’s own security and for its end-users,” comments Wiz.
“Not only an attacker could retrieve sensitive logs and actual plaintext chat messages, but they could also potentially exfiltrate plaintext passwords and local files along propriety information directly from the server using queries like: SELECT * FROM file(‘filename’) depending on their ClickHouse configuration.”
Italy Ban DeepSeek:
Italy’s data protection authority has banned the Chinese AI firm DeepSeek from operating in the country due to concerns about its handling of users’ personal data. The Garante recently questioned DeepSeek about its data handling practices and the source of its training data.
It sought to understand what personal data is collected by its website and mobile app, the sources of that data, the purposes for collection, the legal basis, and whether the data is stored in China.
In a statement issued January 30, 2025, the Garante said it arrived at the decision after DeepSeek provided information that it said was “completely insufficient.”
The companies behind the service, Hangzhou DeepSeek Artificial Intelligence and Beijing DeepSeek Artificial Intelligence, have claimed they do not operate in Italy and that European laws do not apply to them, it added. The watchdog is immediately blocking access to DeepSeek and launching an investigation.
Earlier this week, the Chinese platform faced ongoing cyberattacks that it couldn’t stop, leading to a suspension of new user registrations for almost 24 hours.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














