Researchers found criminal SMS phishing scam campaigns that exploit cloud storage services like Amazon S3, Google Cloud Storage, Backblaze B2, and IBM Cloud Object Storage.
These campaigns, run by unknown threat actors, aim to send SMS messages to redirect users to malicious websites in order to steal their information. According to a technical write-up published by ENEA bad actors are doing this for two primary goals.
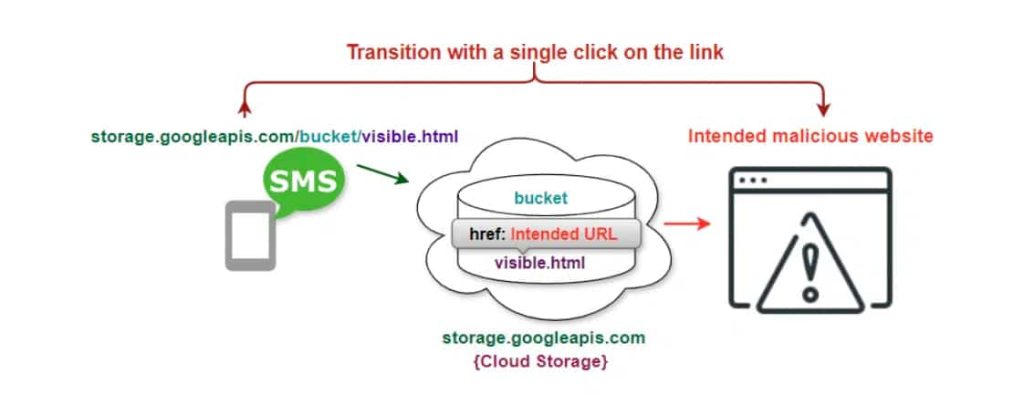
Firstly, They want to send scam text messages to mobile phones without being detected by network firewalls. Secondly, they try to convince users that the messages or links they receive are trustworthy.
By leveraging cloud storage platforms to host static websites with embedded spam URLs, attackers make their messages appear legitimate and avoid common security measures.
Cloud storage services let organizations store and manage files and host static websites by storing website assets in a storage bucket. However, cybercriminals have taken advantage of this by inserting spam URLs in static websites stored on these platforms.
They send web links through text messages to cloud storage sites. This can bypass firewall restrictions as the cloud domains are well-known. When users click on these links, they are taken to harmful sites without realizing it.
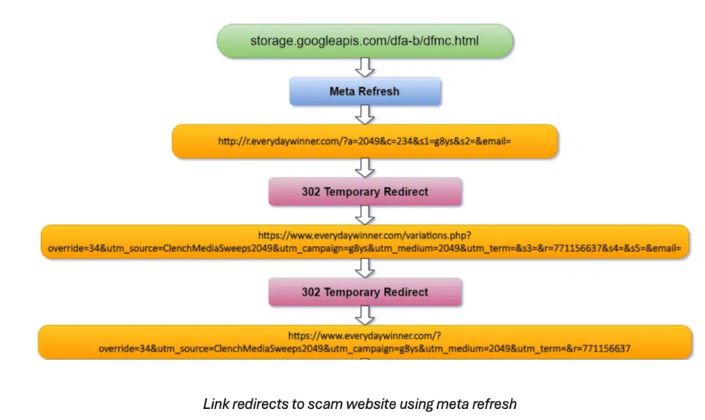
Attackers used the Google Cloud Storage domain “storage.googleapis.com” to create URLs leading to spam sites. A static webpage hosted in a Google Cloud bucket redirects users to scam sites using HTML meta refresh techniques. This allows cybercriminals to trick users into visiting fraudulent websites that imitate legitimate offers, like gift card promotions, in order to steal personal and financial information.
Enea has noticed similar tactics with other cloud storage services such as Amazon Web Services (AWS) and IBM Cloud. URLs sent in SMS messages lead to spam websites.
To protect against these threats, Enea suggests monitoring traffic behavior, checking URLs, and being cautious of unexpected messages with links.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind