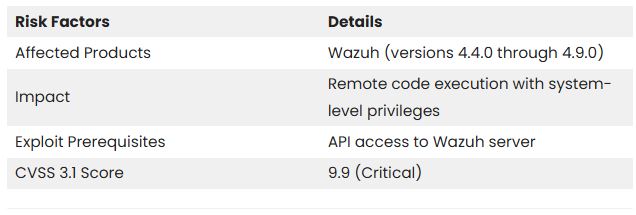
Cybersecurity researchers unveil a critical remote code execution vulnerability (CVE-2025-24016) in Wazuh, a popular open-source SIEM platform.
The vulnerability has a CVSS score of 9.9 affects Wazuh versions 4.4.0 to 4.9.0, enabling attackers with API access to run arbitrary Python code on the servers.
By infosecbulletin
/ Wednesday , June 18 2025
Russian cybersecurity experts discovered the first local data theft attacks using a modified version of legitimate near field communication (NFC)...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
Cybersecurity researcher Jeremiah Fowler discovered an unsecured database with 170,360 records belonging to a real estate company. It contained personal...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
GreyNoise found attempts to exploit CVE-2023-28771, a vulnerability in Zyxel's IKE affecting UDP port 500. The attack centers around CVE-2023-28771,...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently included two high-risk vulnerabilities in its Known Exploited Vulnerabilities (KEV)...
Read More
By infosecbulletin
/ Monday , June 16 2025
SafetyDetectives’ Cybersecurity Team discovered a public post on a clear web forum in which a threat actor claimed to have...
Read More
By infosecbulletin
/ Sunday , June 15 2025
WestJet, Canada's second-largest airline, is looking into a cyberattack that has affected some internal systems during its response to the...
Read More
By infosecbulletin
/ Saturday , June 14 2025
Resecurity found 7.4 million records of Paraguayan citizens' personal information leaked on the dark web today. Last week, cybercriminals attempted...
Read More
By infosecbulletin
/ Friday , June 13 2025
HashiCorp has revealed a critical vulnerability in its Nomad tool that may let attackers gain higher privileges by misusing the...
Read More
By infosecbulletin
/ Friday , June 13 2025
SoftBank has disclosed that personal information of more than 137,000 mobile subscribers—covering names, addresses, and phone numbers—might have been leaked...
Read More
By infosecbulletin
/ Friday , June 13 2025
Serious security vulnerabilities in Trend Micro Apex One could allow attackers to inject malicious code and elevate their privileges within...
Read More
The flaw is due to unsafe deserialization in the DistributedAPI (DAPI) component, where parameters are serialized as JSON and then deserialized using the as_wazuh_object function in framework/wazuh/core/cluster/common.py.
This function has a serious security flaw that allows arbitrary code execution when handling malicious JSON payloads.
Attackers can exploit this vulnerability by using a malicious JSON payload with the unhandled_exc key. This can execute arbitrary system commands.
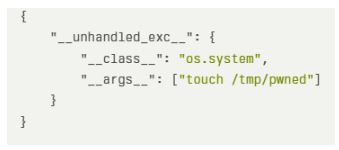
The vulnerable as_wazuh_object function would execute the command “touch /tmp/pwned” on the server when processed by this payload.
The summary of the vulnerability is given below:
Mitigations:
Wazuh fixed this vulnerability in version 4.9.1 by replacing the unsafe eval() function with the safer ast.literal_eval(), which evaluates strings with Python literals without running arbitrary code.
Security experts recommend that organizations with affected Wazuh versions update right away.
“This is a critical vulnerability that should be addressed with the highest priority,” warns the Centre for Cybersecurity Belgium.
Experts suggest organizations that can’t update immediately should use network segmentation, limit API access, monitor API traffic for suspicious activity, and employ Web Application Firewalls (WAFs) to block malicious requests.


 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind