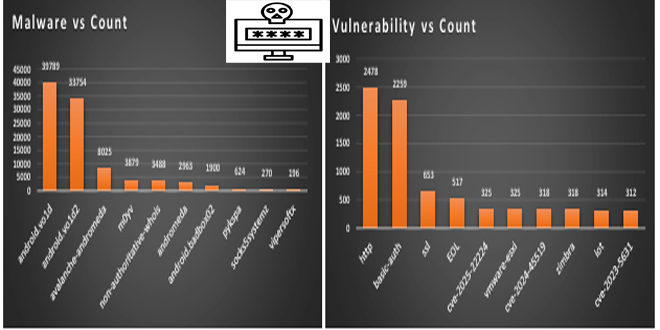
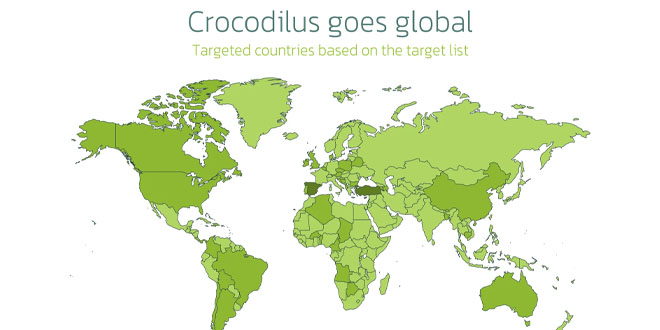
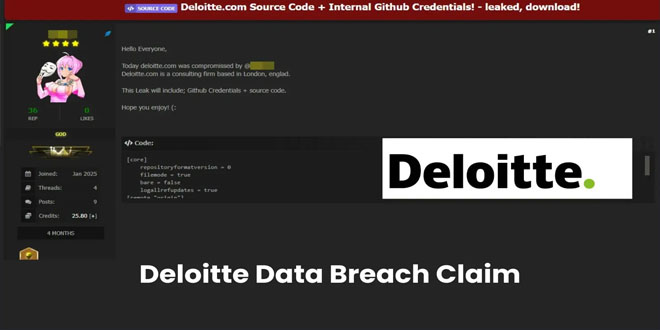
Cisco warns that some Unified Communications Manager and Contact Center Solutions products have a critical remote code execution security vulnerability.
Cisco’s Unified Communications and Contact Center Solutions offer voice, video, and messaging services, as well as customer engagement and management.
The company issued a security bulletin about a vulnerability (CVE-2024-20253) that could let an unauthorized remote attacker run code on a device.
Researcher Julien Egloff from Synacktiv discovered a vulnerability with a 9.9 base score out of 10. The vulnerability is due to incorrect handling of user-input data stored in memory.
Attackers can exploit this vulnerability by sending a carefully designed message to a specific port. This can allow them to execute any command using the web services user’s privileges and gain root access.
CVE-2024-20253 impacts the following Cisco products in their default configurations:
Packaged Contact Center Enterprise (PCCE) versions 12.0 and earlier, 12.5(1) and 12.5(2)
Unified Communications Manager (Unified CM) versions 11.5, 12.5(1), and 14. (same for Unified CM SME)
Unified Communications Manager IM & Presence Service (Unified CM IM&P) versions 11.5(1), 12.5(1), and 14.
Unified Contact Center Enterprise (UCCE) versions 12.0 and earlier, 12.5(1), and 12.5(2).
Unified Contact Center Express (UCCX) versions 12.0 and earlier and 12.5(1).
Unity Connection versions 11.5(1), 12.5(1), and 14.
Virtualized Voice Browser (VVB) versions 12.0 and earlier, 12.5(1), and 12.5(2).
The vendor says there’s no other solution and advises applying the security updates. The updates fix the critical remote code execution (RCE) flaw.
PCCE: 12.5(1) and 12.5(2) apply patch ucos.v1_java_deserial-CSCwd64245.cop.sgn.
Unified CM and Unified CME: 12.5(1)SU8 or ciscocm.v1_java_deserial-CSCwd64245.cop.sha512. 14SU3 or ciscocm.v1_java_deserial-CSCwd64245.cop.sha512.
Unified CM IM&P: 12.5(1)SU8 or ciscocm.cup-CSCwd64276_JavaDeserialization.cop.sha512. 14SU3 or ciscocm.cup-CSCwd64276_JavaDeserialization.cop.sha512.
UCCE: Apply patch ucos.v1_java_deserial-CSCwd64245.cop.sgn for 12.5(1) and 12.5(2).
UCCX: Apply patch ucos.v1_java_deserial-CSCwd64245.cop.sgn for 12.5(1).
VVB: Apply patch ucos.v1_java_deserial-CSCwd64245.cop.sgn for 12.5(1) and 12.5(2).
Cisco recommends using access control lists (ACLs) as a mitigation strategy when applying updates is not immediately feasible.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind