Microsoft has released patches for two critical security flaws in Azure AI Face Service and Microsoft Account that could allow an attacker to escalate their privileges. The flaws are listed below: CVE-2025-21396 (CVSS score: 7.5) – Microsoft Account Elevation of Privilege Vulnerability CVE-2025-21415 (CVSS score: 9.9) – Azure AI Face …
Read More »CVE-2025-21415
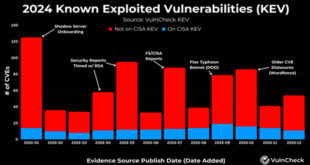
768 Exploited CVEs in 2024, a 20% Increase from 639 in 2023
In 2024, 768 vulnerabilities with CVE identifiers were reported as exploited in the wild, a 20% increase from 639 in 2023. VulnCheck called 2024 “a strong year for threat actors exploiting vulnerabilities,” noting that 23.6% of known exploited vulnerabilities (KEVs) were weaponized by or on the day their CVEs were …
Read More ».Gov Domains Weaponized in Phishing Surge
A recent report from Cofense Intelligence highlights a concerning trend: threat actors are increasingly misusing .gov top-level domains (TLDs) to execute phishing campaigns. Between November 2022 and November 2024, attackers have leveraged vulnerabilities in government websites from various countries to host malicious content, act as command-and-control (C2) servers, and funnel …
Read More »Vulnarabilitties found in Cisco webex and VMware Aria operation
A serious cybersecurity flaw in Cisco Webex Chat has been discovered, allowing unauthorized attackers to access the chat histories of organizations using the platform. Identified in July 2024, the flaw exposed sensitive communications from potentially thousands of organizations, including IT help desks and customer service operations. Proof-of-Concept and Real-World Impact: …
Read More »
CVE-2024-40891
Zyxel CPE Zero-Day Exploited in the Wild
Security researchers have alerted about ongoing exploitation attempts of a newly found zero-day command injection vulnerability in Zyxel CPE Series devices, known as CVE-2024-40891. The critical, unpatched vulnerability has left more than 1,500 devices worldwide at risk, according to Censys. About the Vulnerability – CVE-2024-40891: CVE-2024-40891 is a vulnerability that lets …
Read More »GitHub Desktop Vuln Credential Leaks via Malicious Remote URLs
Multiple security vulnerabilities have been found in GitHub Desktop and other Git projects. If exploited, these could allow attackers to access a user’s Git credentials without permission. “Git implements a protocol called Git Credential Protocol to retrieve credentials from the credential helper,” GMO Flatt Security researcher Ry0taK, who discovered the …
Read More »Four Critical Ivanti CSA Vulnerabilities Exploited: CISA , FBI warns
The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) have released a joint Cybersecurity Advisory to highlight the active exploitation of severe vulnerabilities in Ivanti Cloud Service Appliances (CSA). The vulnerabilities—CVE-2024-8963, CVE-2024-9379, CVE-2024-8190, and CVE-2024-9380—were targeted by threat actors in September 2024, leading to compromises …
Read More »GitLab Releases Patch (CVE-2025-0314) for XSS Exploit
GitLab has released update for high severity cross-site scripting (XSS) flaw. Versions 17.8.1, 17.7.3, and 17.6.4 for both Community Edition (CE) and Enterprise Edition (EE) have been released to address these issues. The CVE-2025-0314 allows attackers to inject malicious scripts into GitLab instances via “improper rendering of certain file types” …
Read More »Delay patching leaves about 50,000 Fortinet firewalls to zero-day attack
Fortinet customers must apply the latest updates, as almost 50,000 management interfaces remain vulnerable to the latest zero-day exploit. The Shadowserver Foundation reports that 48,457 Fortinet devices remain publicly exposed and unpatched for CVE-2024-55591, despite urgent warnings in the last week. The situation hasn’t improved. Shadowserver started tracking exposed devices …
Read More »Multiple Azure DevOps Vulns Allow To Inject CRLF Queries & Rebind DNS
Security researchers have found several vulnerabilities in Azure DevOps that could enable attackers to inject CRLF queries and carry out DNS rebinding attacks. Binary Security found serious security risks in a widely used development platform during a client engagement. The first vulnerability in Azure DevOps’ ‘endpointproxy’ feature enables Server-Side Request …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind