The newly released Kali Linux 2023.3 is here, bringing along with it an impressive array of nine brand new tools and internal enhancements. It’s time to download and discover all the exciting features this latest version has to offer. Kali Linux stands as an exceptional Linux distribution designed specifically for …
Read More »CISA Releases Four Industrial Control Systems Advisories
CISA released four Industrial Control Systems (ICS) advisories . These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. ICSA-23-234-01 Hitachi Energy AFF66x ICSA-23-234-02 Trane Thermostats ICSA-23-234-03 Rockwell Automation ThinManager ThinServer ICSA-23-138-02 Mitsubishi Electric MELSEC WS Series (Update A) CISA encourages users and administrators to review the newly released ICS …
Read More »G20 digital ministers sign up for Digital Public Infrastructure push
The G20 ministers for the digital economy met in India and proposed a Framework for Systems of Digital Public Infrastructure (DPI). The Framework comprises three elements: Interoperable and reusable digital systems and applications, such as software codes, protocols, and standards, have revolutionized technology by offering versatility and adaptability across various …
Read More »TeamTNT Using NVIDIA Drivers to Mine Cryptocurrency
Kubernetes deployments have been targeted by attackers as a means to compromise the cloud environment to control workloads and harness the power of the cloud to conduct unauthorized tasks. Earlier research has highlighted how the TeamTNT threat group conducts attacks against large-scale Kubernetes deployments. ALSO READ: 2023 Threat Report: Social …
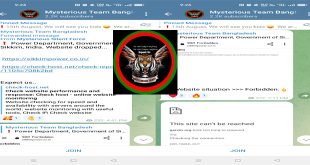
Read More »Indian two sites dropped, claimed “mysterious team Bangladesh”
Mysterious team Bangladesh claim the responsibility of down the website of power department, Government of Sikkim, India and Indian Gujarat Electricity regulatory commission website. They share screen shot on their telegram channel. ALSO READ: India published Information Security Practices for Government Entities Coming 15 August, there is a threat of …
Read More »India published Information Security Practices for Government Entities
India published Information Security Practices for Government Entities. The purpose of these guidelines is to establish a prioritized baseline of cyber security measures and controls within Central government organizations and their associated organizations. These guidelines relating to information security practices, procedures, prevention and response are issued by the Indian Computer …
Read More »2023 Threat Report: Social Engineering and Web Attacks waves
The overall cyber-threat risks have significantly increased during the second quarter of 2023. The number of unique web attacks being blocked has increased by 24%, resulting in over 700 million unique attacks being blocked every month. Social engineering and web-related threats have become increasingly prevalent among the various cyber risks. …
Read More »UK electoral Commission hack exposed data of 40 million voters
The UK’s Electoral Commission was targeted by a “sophisticated cyber-attack”, which led to the personal information of many British voters being exposed. In October 2022, the Commission made a shocking discovery – an attack had been detected on its systems after detecting suspicious activity. Attackers accessed the servers of the …
Read More »Two-Thirds of UK Sites Vulnerable to Bad Bots: DataDome
DataDome reveals that a staggering 66% of UK websites are unable to block simple bot attacks. As a result, these businesses are left vulnerable to fraud, account breaches, and countless other risks. The security vendor used its BotTester tool to test more than 2400 of the biggest sites in the …
Read More »Google asks employees to sleep at office campus for $99/night
As the Covid-19 pandemic subsides, offices are finding new ways to motivate employees to return to work. Google is also making efforts to ensure a smooth transition when returning to the campus. The tech giant is offering a discounted hotel stay for $99 per night at a new campus in …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind