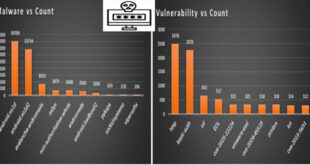
The Security Intelligence and Response Team (SIRT) at Akamai has found that multiple Mirai-based botnets are exploiting CVE-2025-24016, a critical RCE vulnerability in Wazuh servers. This flaw, which has a CVSS score of 9.9, allows remote attackers to execute arbitrary Python code through unsanitized JSON inputs in the Wazuh Distributed …
Read More »CVE-2025-24016
Fortinet flaws now exploited in Qilin ransomware attacks
The Qilin ransomware operation has recently joined attacks exploiting two Fortinet vulnerabilities that allow bypassing authentication on vulnerable devices and executing malicious code remotely. Qilin (also tracked as Phantom Mantis) surfaced in August 2022 as a Ransomware-as-a-Service (RaaS) operation under the “Agenda” name and has since claimed responsibility for over …
Read More »Critical Cisco ISE flaw impacts cloud deployments on AWS, Microsoft Azure, and OCI
Cisco fixed a critical vulnerability in the Identity Services Engine (ISE) that could let unauthorized attackers carry out harmful actions. The vulnerability, CVE-2025-20286 (CVSS score 9.9), affects Cisco ISE on AWS, Microsoft Azure, and Oracle Cloud. It allows unauthenticated remote attackers to access sensitive data, perform basic admin tasks, modify …
Read More »App builiding platform exposes over 3 million records, including PII
Cybersecurity researcher Jeremiah Fowler discovered an unprotected database with 3,637,107 records likely from a no-code app-building platform. The unprotected database, totaling 12.2 TB and containing 3,637,107 records, included internal files, images, and spreadsheets labeled “users” and “invoices.” These documents featured names, emails, physical addresses, and payment details for users and …
Read More »
ALERT
Thousands of IP addresses compromised nationwide: CIRT warn
As Bangladesh prepares for the extended Eid-ul-Adha holidays, the BGD e-GOV Computer Incident Response Team (CIRT) has issued an urgent cybersecurity alert, warning of heightened cyber threats due to reduced monitoring and operational oversight during the festive period. Current Threat Landscape: The CIRT’s Cyber Threat Intelligence Unit has detected widespread …
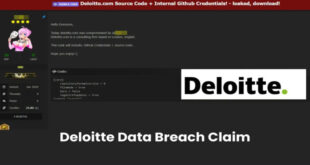
Read More »Hacker claim Leak of Deloitte Source Code & GitHub Credentials
A hacker known as “303” claim to breach the company’s systems and leaked sensitive internal data on a dark web forum. The reported breach involves GitHub credentials and source code from Deloitte’s U.S. consulting division’s internal project repositories. Medium reports, “On May 30, 2025, Deloitte, a leading global consulting firm, …
Read More »251 Amazon-Hosted IPs Used in Exploit Scan for ColdFusion, Struts, and Elasticsearch
Cybersecurity researchers recently revealed a coordinated cloud-based scanning attack that targeted 75 different exposure points earlier this month. On May 8, 2025, GreyNoise observed activity from 251 malicious IP addresses located in Japan and hosted by Amazon. “These IPs triggered 75 distinct behaviors, including CVE exploits, misconfiguration probes, and recon …
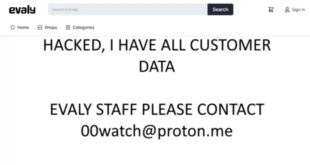
Read More »Evaly E-commerce Platform Allegedly Hacked
Evaly, a Bangladeshi e-commerce platform, is reportedly facing a major data breach that may have exposed sensitive information of around 783,611 customers and merchants. This incident is said to have occurred today, May 23, 2025. Evaly’s website currently displays a message stating, “HACKED, I HAVE ALL CUSTOMER DATA. EVALY STAFF …
Read More »184 Million Leaked Credentials Discovered in Open Database
Security researchers have discovered a database with 184 million account credentials, highlighting the need to update compromised passwords, strengthen weak ones, and enable multi-factor authentication. Although the database is not new, it shows the ongoing circulation of leaked data from major platforms like Apple, Google, Microsoft, Amazon, Facebook, Instagram, and …
Read More »Researchers found 200 billion files exposed in cloud buckets
Billions of files, including documents, source code, and backups, are leaking because of misconfigured cloud storage. Cyble, a cybersecurity company focused on dark web monitoring and threat intelligence, reports its vulnerability search tool has found over 660,000 exposed buckets and 200 billion leaking files from seven major cloud providers. Filtering …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind