A coordinated phishing campaign has been uncovered targeting critical Bangladeshi infrastructure — particularly government organizations and law enforcement agencies. This attack leveraged compromised official email credentials to distribute fraudulent emails containing malicious attachments and deceptive login pages reported by BGD e-Gov CIRT.
📌 Key Attack Techniques:
Email Spoofing Using Trusted Accounts:
Attackers sent phishing emails from seemingly legitimate government or law enforcement addresses.
Malicious Links via Image Files:
Embedded phishing links within .jpeg or .png files disguised as attachments.
Password-Protected .docx Files:
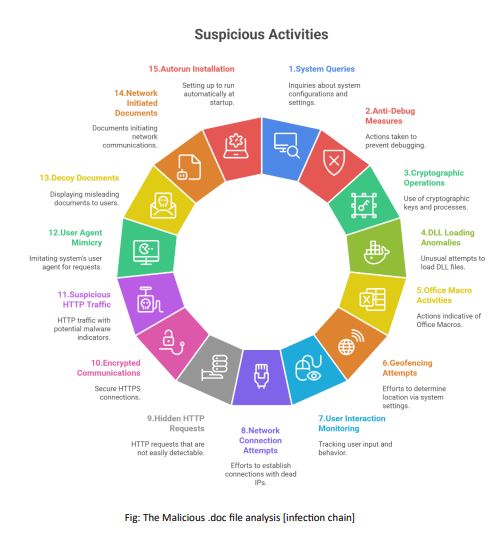
Used to bypass filters; some contained Trojan droppers initiating infection chains.

Deceptive Domains & Hosting Abuse:
Example:
https://mail-baf-mil-bd-fils-cas-visit-to-chi[.]netlify[.]app
Mimics official military/government domains
Hosted on Netlify for SSL and trusted infrastructure abuse
Backend connected to attacker infrastructure
Credential Harvesting via Fake Forms:
HTML phishing forms collected user credentials under fake fields like “pdf” and “sweet”.
Evading Detection:
Hidden JavaScript loaders to mask login forms
Developer tools and right-clicks disabled
Use of misleading file extensions such as .ttt, .url, and .html
🎯 Primary Targets:
Law Enforcement Agencies
Government Organizations
🛑 Indicators of Compromise (IOCs):

Suspicious IPs:
18.208.88[.]157
45.95.161[.]15
88.119.161[.]40
173.239.196[.]4 / .157 / .158
Malicious Files:
Password-protected .doc files (Trojan)
Fake image viewers or .pdf loaders
Deceptive Domains:
mail.mofa.govnp[.]org
mx1.nepal.govnp[.]org
nitc.govnp[.]org
✅ Recommended Actions:
DO NOT click unknown links or open unexpected attachments.
Verify senders, even if using .gov or .mil domains.
Enable MFA across all critical systems.
Implement email filtering & sandboxing.
Educate staff on phishing red flags.
Report incidents or suspicious indicators to: [email protected]
CIRT alerts CII, Energy Sectors, Banks risk for a large-scale cyberattack
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind













