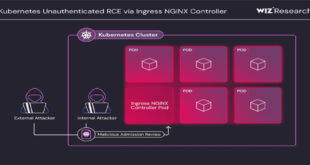
Kubernetes users of the Ingress NGINX Controller are advised to fix four newly found remote code execution ( RCE) vulnerabilities, which have a CVSS score of 9.8. Wiz Security named four vulnerabilities “IngressNightmare” that affect the admission controller of the popular open-source software used for directing external traffic to Kubernetes …
Read More »IngressNightmare
(CVE-2025-29927)
Urgently Patch Your Next.js for Authorization Bypass
Next.js, a widely used React framework for building full-stack web applications, has fixed a serious security vulnerability. Used by many large companies, Next.js facilitates rapid development with advanced React features and Rust-based JavaScript tools. A recent security advisory has highlighted a critical authorization bypass issue that requires urgent action from …
Read More »Oracle refutes breach after hacker claims 6 million data theft
A hacker known as “rose87168” claims to have stolen six million records from Oracle Cloud servers. The stolen data includes Java Key Store (JKS) files, encrypted Single Sign-On (SSO) passwords, hashed LDAP passwords, key files, and Enterprise Manager Java Platform Security (JPS) keys. Stolen Data on Dark Web Forums: Stolen …
Read More »Russian zero-day seller to offer up to $4 million for Telegram exploits
Operation Zero, a Russian zero-day broker, is offering up to $4 million for Telegram exploits. They seek $500K for one-click RCE, $1.5M for zero-click RCE, and $4M for a full-chain exploit that can fully compromise a device. The firm only sells exploits to the Russian government and local companies. We …
Read More »Cybercriminals Exploit Checkpoint’s Driver in a BYOVD Attack
Threat actors are exploiting a component of CheckPoint’s ZoneAlarm antivirus to bypass Windows security measures. Nima Bagheri, a security researcher in Austin and founder of Venak Security, announced a new Bring Your Own Vulnerable Driver (BYOVD) attack in a report on March 20. Threat actors exploited vulnerabilities in vsdatant.sys, a …
Read More »IBM and Veeam Release Patches in AIX System and Backup
IBM has resolved two critical vulnerabilities in its AIX operating system that could allow command execution. The list of shortcomings, which impact AIX versions 7.2 and 7.3, is below: CVE-2024-56346 (CVSS score: 10.0) – A vulnerability that allows a remote attacker to run any commands through the AIX nimesis NIM …
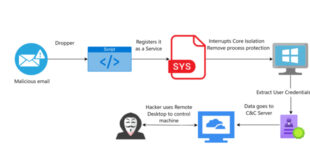
Read More »WhatsApp patched zero-click flaw exploited in spyware attacks
WhatsApp has patched a zero-click, zero-day vulnerability used to install Paragon’s Graphite spyware following reports from security researchers at the University of Toronto’s Citizen Lab. The company addressed the attack vector late last year “without the need for a client-side fix” and decided not to assign a CVE-ID after “reviewing …
Read More »
CVE-2025-24472
CISA Warns of Fortinet FortiOS Auth Bypass Vuln Exploited in Wild
CISA has issued a critical alert about a critical vulnerability in Fortinet’s FortiOS and FortiProxy systems. CVE-2025-24472, an authentication bypass vulnerability, has been added to CISA’s Known Exploited Vulnerabilities catalog. Fortinet FortiOS Authentication Bypass Vulnerability: Fortinet FortiOS and FortiProxy contain an authentication bypass vulnerability that allows a remote attacker to …
Read More »11 state hackers exploit new Windows zero-day since 2017
11 nation-state groups from North Korea, China, and Russia are exploiting a vulnerability in a common feature of Microsoft Windows. Researchers at the Zero Day Initiative (ZDI) have found several campaigns exploiting the bug in Windows shortcut (.lnk) files, dating back to 2017. Microsoft hasn’t assigned a CVE number, but …
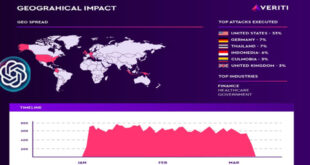
Read More »Hackers Exploit ChatGPT with CVE-2024-27564
Attackers are actively targeting OpenAI, exploiting CVE-2024-27564, a Server-Side Request Forgery (SSRF) vulnerability in OpenAI’s ChatGPT infrastructure. Veriti’s latest research reveals that this vulnerability, despite being classified as medium severity, has already been weaponized in real world attacks. Research uncovers: Active exploitation in the wild, with over 10,479 attack attempts …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind