Attackers linked to the Play ransomware operation deployed a zero-day privilege escalation exploit during an attempted attack against an organization in the U.S. The attack occurred prior to the disclosure and patching of a Windows elevation of privilege zero-day vulnerability (CVE-2025-29824) in the Common Log File System Driver (clfs.sys) on …
Read More »CVE-2025-29824
Hacker exploited Samsung MagicINFO 9 Server RCE flaw
Hackers are exploiting an unauthenticated remote code execution vulnerability in the Samsung MagicINFO 9 Server to take control of devices and install malware. The server allows file uploads to update display content, but hackers are using this feature to upload malicious code. The flaw identified as CVE-2024-7399 was publicly disclosed …
Read More »CISA adds Langflow flaw to its KEV catalog
CISA added the Langflow vulnerability, CVE-2025-3248 (CVSS score 9.8), to its Known Exploited Vulnerabilities catalog. Langflow is a popular tool used for building agentic AI workflows. CVE-2025-3248 is a code injection vulnerability in the /api/v1/validate/code endpoint. An unauthenticated remote attacker can exploit it by sending specially crafted HTTP requests to …
Read More »Google Fixes Android Flaw (CVE-2025-27363) Exploited by Attackers
Google has released its monthly Android security updates, addressing 46 vulnerabilities, including one that has been actively exploited. CVE-2025-27363 (CVSS score: 8.1) is a high-severity vulnerability in the System component that allows local code execution without needing extra privileges. “The most severe of these issues is a high security vulnerability …
Read More »UAP hosted “UAP Cyber Siege 2025”, A national level cybersecurity competition
The Cyber Security Club, representing the Department of Computer Science and Engineering at the University of Asia Pacific (UAP), has achieved a remarkable feat by hosting its first national-level cybersecurity competition, named “UAP Cyber Siege 2025.” This event not only draws attention to the growing importance of cybersecurity but also …
Read More »xAI Dev Leaks API Key for Private SpaceX, Tesla & Tweeter
A major security issue happened at Elon Musk’s AI company, xAI, when a developer accidentally posted a private API key on GitHub, making it publicly accessible for nearly two months. Exposed credentials allowed unauthorized access to private large language models (LLMs) fine-tuned for SpaceX, Tesla, and Twitter/X, revealing serious security …
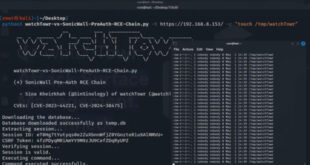
Read More »SonicWall Exploit Chain Exposes Admin Hijack Risk via 2 CVEs
A new exploit chain for SonicWall’s Secure Mobile Access (SMA) appliances has been released by watchTowr Labs. It details how two vulnerabilities, CVE-2023-44221 and CVE-2024-38475, can be combined to allow remote, unauthenticated attackers to hijack admin sessions and run arbitrary code. SonicWall identifies CVE-2024-38475 as a critical vulnerability in the …
Read More »TikTok fined €530 million for sending E.U. Data to China
Ireland’s Data Protection Commission fined TikTok €530 million ($601 million) on Friday for violating data protection laws by transferring European users’ data to China. “TikTok infringed the GDPR regarding its transfers of EEA [European Economic Area] User Data to China and its transparency requirements,” the DPC said in a statement. …
Read More »Microsoft New Accounts Go Passwordless By Default
Microsoft is focusing on eliminating password-based authentication, promoting passwordless sign-in and sign-up methods instead. For the past decade, Microsoft has allowed users to sign in using facial recognition, fingerprints, or a PIN with Windows Hello. Now, over 99% of users use this method to access their Windows devices, according to …
Read More »SonicWall Patched for SSRF Vulnerability in SMA1000 Appliances
SonicWall’s Product Security Incident Response Team (PSIRT) has released a critical update for its SMA1000 series appliances due to a Server-Side Request Forgery (SSRF) vulnerability, identified as CVE-2025-2170, with a CVSS base score of 7.2. The flaw in the SMA1000 appliances’ WorkPlace interface allows unauthenticated remote attackers to send unauthorized …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind