SafeBreach Labs revealed a zero-click vulnerability in the Windows Lightweight Directory Access Protocol (LDAP) service, dubbed “LDAP Nightmare”. This critical vulnerability, tracked as CVE-2024-49112, has been assigned a CVSS score of 9.8, highlighting its severe implications for enterprise networks. SafeBreach researchers demonstrated how the exploit could crash unpatched Windows Servers, …
Read More »CVE-2024-49112
Financial Threat Assessment 2024
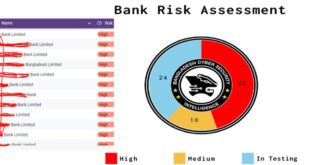
BCSI marks Bangladeshi 28 banks high, 10 medium for cyber attack
Bangladesh Cyber Security Intelligence (BCSI) has published Financial Threat Assessment report for 2024. In an era where financial institutions and Critical Information Infrastructure (CII) are essential to both economic and national stability, the growing frequency and complexity of cyber threats have underscored a pressing truth: Bangladesh’s national security is under …
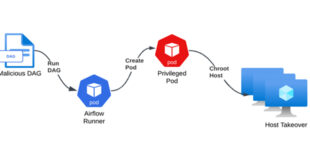
Read More »Misconfigured Kubernetes RBAC in Azure Airflow Could Expose Entire Cluster
Cybersecurity researchers have uncovered three security weaknesses in Microsoft’s Azure Data Factory Apache Airflow integration that, if successfully exploited, could have allowed an attacker to gain the ability to conduct various covert actions, including data exfiltration and malware deployment. “Exploiting these flaws could allow attackers to gain persistent access as …
Read More »US Treasury says it was hacked by China via third party: Beijing denies
The US Treasury Department said on Monday that Chinese-linked hackers were able to gain access to ‘unclassified documents’ after compromising the agency’s networks earlier this month. According to a US Treasury letter addressed to US Senators Sherrod Brown (D-OH) and Tim Scott (R-SC) on Monday – the Chinese hackers gained …
Read More »PoC Exploited Released for Oracle Weblogic Server Vul
Security researchers have warned that a Proof-of-Concept (PoC) exploit has been publicly released for a critical vulnerability affecting Oracle WebLogic Server. The flaw tracked as CVE-2024-21182, poses a significant risk to organizations using the server, as it allows an unauthenticated attacker with network access to compromise the targeted system. The …
Read More »Microsoft warn dev urgently to update .NET installer link
Microsoft is forcing .NET developers to quickly update their apps and developer pipelines so they do not use ‘azureedge.net’ domains to install .NET components, as the domain will soon be unavailable due to the bankruptcy and imminent shutdown of CDN provider Edgio. Specifically, the domains “dotnetcli.azureedge.net” and “dotnetbuilds.azureedge.net” will be …
Read More »Look back; The Worst Hacks of 2024
In 2024, digital security experienced major breaches as cybercriminals and state-backed groups exploited vulnerabilities for large-scale attacks. These incidents were efficient for attackers but damaging to affected organizations and individuals, threatening their privacy and security. With rising global tensions, 2025 is anticipated to present more cybersecurity challenges. Infosecbulletin highlights the …
Read More »HIPAA to be updated with new cybersecurity regulations, White House
Proposed new cybersecurity rules for healthcare institutions will focus on how they protect user data under HIPAA, as stated by a White House official. Anne Neuberger, deputy national security adviser for cyber and emerging technology, told “The security rule [under HIPAA] was first published in 2003 and it was last …
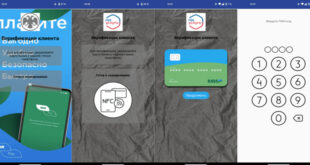
Read More »New NGate Trojan Drains Bank Accounts via ATMs
Malware analysts at Doctor Web have identified new versions of the NGate banking trojan. This malware steals data from the device’s NFC chip, enabling attackers to withdraw money from victims’ accounts at ATMs without their knowledge. The NGate banker was first noticed by antivirus vendors in autumn 2023 due to …
Read More »CPE Seminar Held at ISACA Dhaka Chapter Office Premises
ISACA Dhaka chapter arranged a Continuing Professional Education (CPE) seminar for the community as its calendar work to develop the professionals. On 28 December, Saturday at ISACA Dhaka office with the participation over 50 participants the seminar draw the attention with the two leading topic on “Leadership & Communication is …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind