The U.S. Cybersecurity and Infrastructure Security Agency (CISA) released 6 advisories for Industrial Control Systems (ICS), highlighting vulnerabilities in various critical systems. These advisories are intended to alert organizations to potential risks that could result in unauthorized access, system breaches, or exposure of sensitive data if not properly addressed. The …
Read More »Account Credentials for Security Vendors Found on Dark Web: Cyble Report
# “While many leaked security credentials belong to customers, some exposed sensitive accounts suggest that security vendors too have been hit by infostealers.” # A Cyble report reveals that account credentials from multiple cybersecurity vendors are being sold on dark web marketplaces. While most of the exposed credentials belong to …
Read More »Four Critical Ivanti CSA Vulnerabilities Exploited: CISA , FBI warns
The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) have released a joint Cybersecurity Advisory to highlight the active exploitation of severe vulnerabilities in Ivanti Cloud Service Appliances (CSA). The vulnerabilities—CVE-2024-8963, CVE-2024-9379, CVE-2024-8190, and CVE-2024-9380—were targeted by threat actors in September 2024, leading to compromises …
Read More »GitLab Releases Patch (CVE-2025-0314) for XSS Exploit
GitLab has released update for high severity cross-site scripting (XSS) flaw. Versions 17.8.1, 17.7.3, and 17.6.4 for both Community Edition (CE) and Enterprise Edition (EE) have been released to address these issues. The CVE-2025-0314 allows attackers to inject malicious scripts into GitLab instances via “improper rendering of certain file types” …
Read More »
CVE-2025-20156
Cisco Fixes Meeting Management Allowing Privilege Escalation
Cisco has released a security advisory concerning a critical privilege escalation vulnerability (CVE-2025-20156) in its Meeting Management software. With a daunting CVSS score of 9.9, this vulnerability poses a significant risk, as it could enable remote, authenticated attackers with minimal privileges to elevate their access to administrator status on compromised …
Read More »Delay patching leaves about 50,000 Fortinet firewalls to zero-day attack
Fortinet customers must apply the latest updates, as almost 50,000 management interfaces remain vulnerable to the latest zero-day exploit. The Shadowserver Foundation reports that 48,457 Fortinet devices remain publicly exposed and unpatched for CVE-2024-55591, despite urgent warnings in the last week. The situation hasn’t improved. Shadowserver started tracking exposed devices …
Read More »Daily Security Update Dated: 21.01.2025
Every day a lot of cyberattack happen around the world including ransomware, Malware attack, data breaches, website defacement and so on. Its our daily security digest to cover the latest happenings in the world. Spend a bit time to read out todays update: MITRE Launches D3FEND 1.0 – A Milestone …
Read More »126 Linux kernel Vulns Allow Attackers Exploit 78 Linux Sub-Systems
Ubuntu 22.04 LTS users are advised to update their systems right away due to a crucial security patch from Canonical that fixes critical vulnerabilities in the Linux kernel for Xilinx ZynqMP processors. The Linux kernel for Xilinx Zynq UltraScale+ MPSoC is customized to support the features and hardware of these …
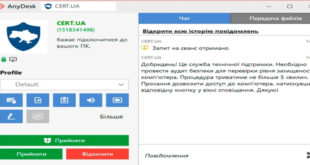
Read More »CERT-UA alerts about “security audit” requests through AnyDesk
Attackers are pretending to be Ukraine’s Computer Emergency Response Team (CERT-UA) using AnyDesk to access target computers. “Unidentified individuals are sending connection requests via AnyDesk under the pretext of conducting a ‘security audit to verify the level of protection,’ using the name ‘CERT.UA,’ the CERT-UA logo, and the AnyDesk ID …
Read More »Oracle Critical Pre-Release update addressed 320 flaw
Oracle Critical Patch Update Pre-Release Announcement shares details about the upcoming update scheduled for January 21, 2025. Note that this information may change before the official advisory is released. A Critical Patch Update contains patches for various security vulnerabilities. This update includes 320 new patches, some of which affect multiple …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind