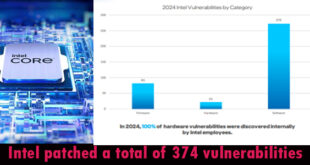
In 2024, Intel addressed a remarkable 374 vulnerabilities across its software, firmware, and hardware products, distributing bug bounty rewards for approximately half of these issues. Intel’s latest product security report reveals that the highest number of resolved bugs last year (272) were in utilities (146), drivers (68), applications (35), SDKs …
Read More »
CVE-2025-24016
Critical RCE Vulnerability Discovered in Wazuh Server
Wazuh, a top provider of open-source security solutions, has released a critical security advisory for a remote code execution vulnerability (RCE) (CVE-2025-24016) with a CVSS score of 9.9. This flaw could enable attackers to take full control of affected Wazuh servers. Wazuh is a popular platform for threat prevention, detection, …
Read More »Microsoft 2025 February Patch Tuesday fixes 2 zero-days, 55 flaws
Microsoft’s February 2025 Patch Tuesday includes security updates for 55 vulnerabilities, including four zero-days, two of which are currently being exploited. This Patch Tuesday addresses three critical remote code execution vulnerabilities. The number of bugs in each vulnerability category is listed below: 19 Elevation of Privilege Vulnerabilities 2 Security Feature …
Read More »
Patch Now
SonicWall firewall vuln allows hackers to hijack VPN sessions
Bishop Fox security researchers have released detailed information on the CVE-2024-53704 vulnerability, which lets attackers bypass authentication in some versions of the SonicOS SSLVPN application. On January 7, the vendor warned about the risk of exploitation of a flaw and advised administrators to upgrade their SonicOS firewalls’ firmware to fix …
Read More »SAP Security Patch February 2025: Multi Vulns Addressed
SAP has issued new security patches for 19 vulnerabilities and updated 2 previous Security Notes. This Patch Day features fixes for various issues, including a high-risk authorization flaw in SAP BusinessObjects Business Intelligence. The critical vulnerability (CVE-2025-0064, CVSS 8.7) enables an attacker with admin rights to impersonate any user in …
Read More »
TRACKING RANSOMWARE
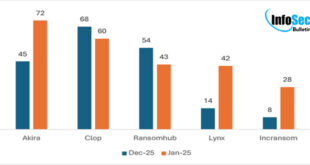
Akira Topped January 2025 as the Most Active Ransomware Threat
In January 2025, there were 510 global ransomware incidents, with Akira as the leading group and new ones like MORPHEUS and Gd Lockersec appearing. The Manufacturing sector was the main target, followed by Finance and IT, with the USA being the most affected region. This report highlights key ransomware trends, …
Read More »FinStealer Malware Targets Indian Bank’s Mobile Users, Stealing Credentials
CYFIRMA analysis reveals a sophisticated malware campaign that exploits a major Indian bank’s brand through fake mobile apps. These apps, distributed via phishing links and social engineering, closely resemble the real bank apps, deceiving users into sharing their credentials and personal information. The malware uses advanced techniques, such as encrypted …
Read More »
CVE-2024-52875
Over 12,000 Firewall Vulnerable to 1-Click RCE Exploit
Over 1,200 firewall instances are vulnerable to a critical remote code execution issue, known as CVE-2024-52875. The vulnerability is found in several unauthenticated web interface paths, including /nonauth/addCertException.cs, /nonauth/guestConfirm.cs, and /nonauth/expiration.cs. These pages do not adequately sanitize user input from the dest GET parameter, allowing attackers to inject line feed …
Read More »
CVE-2025-24200
Apple releases update of zero-day vuln exploited in the Wild
Apple has issued emergency security updates to fix a zero-day vulnerability, CVE-2025-24200, which is being exploited in targeted attacks on iPhone and iPad users. The vulnerability lets attackers turn off USB Restricted Mode on a locked device, risking unauthorized access to sensitive data. Apple is aware that this issue may …
Read More »Zimbra Releases Updates for SQL Injection, XSS, and SSRF Vulns
Zimbra has released updates for its Collaboration software to fix critical security flaws that could lead to information disclosure if exploited. CVE-2025-25064 is a critical vulnerability with a CVSS score of 9.8. It is an SQL injection issue in the ZimbraSync Service SOAP endpoint, affecting versions before 10.0.12 and 10.1.4. …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind