Splunk has released a security advisory about critical vulnerabilities in Splunk Enterprise and Splunk Cloud Platform. These issues could lead to remote code execution and unauthorized access to sensitive information. CVE-2025-20229: Remote Code Execution via Unauthorized File Upload (CVSS 8.0): CVE-2025-20229 highlights that low-privileged users can pose significant risks by …
Read More »CIRT alert Situational Awareness for Eid Holidays
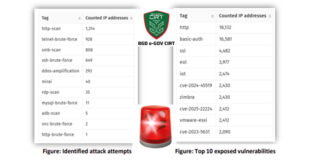
As the Eid holidays near, cybercriminals may try to take advantage of weakened security during this time. The CTI unit of BGD e-GOV CIRT has identified several web-based attacks, especially during non-office hours and holidays. Common attack methods include SSH brute force, SQL injection, PHP CGI-bin exploits, and directory traversal …
Read More »Cyberattack on Malaysian airports: PM rejected $10 million ransom
Operations at Kuala Lumpur International Airport (KLIA) were unaffected by a cyber attack in which hackers demanded US$10 million (S$13.4 million). On March 25, the National Cyber Security Agency (Nacsa) and Malaysia Airports Holdings Berhad (MAHB) announced a cyber-security threat targeting some computer systems at KLIA on March 23. “A …
Read More »Micropatches released for Windows zero-day leaking NTLM hashes
Unofficial patches are available for a new Windows zero-day vulnerability that allows remote attackers to steal NTLM credentials by deceiving targets into opening malicious files in Windows Explorer. NTLM has been widely exploited in NTLM relay attacks (where threat actors force vulnerable network devices to authenticate to attacker-controlled servers) and …
Read More »VMware Patches Authentication Bypass Flaw in Windows Tool
On Tuesday, VMware issued an urgent fix for a security flaw in its VMware Tools for Windows. CVE-2025-22230 allows a malicious user with basic access on a Windows guest virtual machine to execute high-privilege tasks within that VM. VMware’s important bulletin states that an authentication bypass bug, due to improper …
Read More »
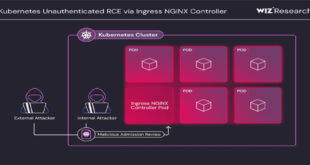
IngressNightmare
Over 40% of cloud environments are vulnerable to RCE
Kubernetes users of the Ingress NGINX Controller are advised to fix four newly found remote code execution ( RCE) vulnerabilities, which have a CVSS score of 9.8. Wiz Security named four vulnerabilities “IngressNightmare” that affect the admission controller of the popular open-source software used for directing external traffic to Kubernetes …
Read More »
(CVE-2025-29927)
Urgently Patch Your Next.js for Authorization Bypass
Next.js, a widely used React framework for building full-stack web applications, has fixed a serious security vulnerability. Used by many large companies, Next.js facilitates rapid development with advanced React features and Rust-based JavaScript tools. A recent security advisory has highlighted a critical authorization bypass issue that requires urgent action from …
Read More »Oracle refutes breach after hacker claims 6 million data theft
A hacker known as “rose87168” claims to have stolen six million records from Oracle Cloud servers. The stolen data includes Java Key Store (JKS) files, encrypted Single Sign-On (SSO) passwords, hashed LDAP passwords, key files, and Enterprise Manager Java Platform Security (JPS) keys. Stolen Data on Dark Web Forums: Stolen …
Read More »Russian zero-day seller to offer up to $4 million for Telegram exploits
Operation Zero, a Russian zero-day broker, is offering up to $4 million for Telegram exploits. They seek $500K for one-click RCE, $1.5M for zero-click RCE, and $4M for a full-chain exploit that can fully compromise a device. The firm only sells exploits to the Russian government and local companies. We …
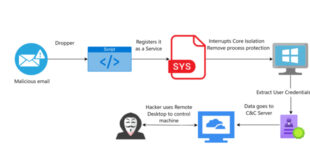
Read More »Cybercriminals Exploit Checkpoint’s Driver in a BYOVD Attack
Threat actors are exploiting a component of CheckPoint’s ZoneAlarm antivirus to bypass Windows security measures. Nima Bagheri, a security researcher in Austin and founder of Venak Security, announced a new Bring Your Own Vulnerable Driver (BYOVD) attack in a report on March 20. Threat actors exploited vulnerabilities in vsdatant.sys, a …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind