In its April 2025 security update, Google patched 62 vulnerabilities in Android, including two zero-days used in targeted attacks. Among the 62 fixed vulnerabilities, most are high-severity elevation of privilege flaws, and two are zero-day vulnerabilities that hackers can easily exploit. CVE-2024-43197 is a critical privilege escalation flaw in the …
Read More »Check Point said BreachForum post old data
Israeli cybersecurity firm Check Point has responded to a hacker who claimed to have stolen valuable information from its systems. Over the weekend, a hacker named CoreInjection claimed in a BreachForums post that they were selling data allegedly stolen from Check Point for 5 Bitcoin (around $430,000). The threat actor …
Read More »Apple Warns of 3 Zero Day Vulns Actively Exploited
Apple has issued an urgent security advisory about 3 critical zero-day vulnerabilities—CVE-2025-24200, CVE-2025-24201, and CVE-2025-24085—that are being actively exploited in advanced attacks. Multiple Apple devices, including iPhones, iPads, and Macs, are affected by these vulnerabilities. Users should update their devices right away to reduce security risks. Significant Vulnerabilities Under Active …
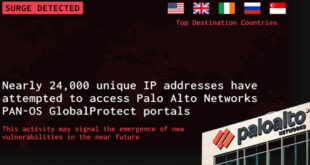
Read More »24,000 unique IP attempted to access Palo Alto GlobalProtect portals
GreyNoise has detected a sharp increase in login scanning aimed at Palo Alto Networks PAN-OS GlobalProtect portals. In the past 30 days, nearly 24,000 unique IP addresses have tried to access these portals. This indicates a coordinated attempt to test network defenses and find vulnerable systems, possibly as a step …
Read More »
CVE-2025-1268
Patch urgently! Canon Fixes Critical Printer Driver Flaw
Canon has announced a critical security vulnerability, CVE-2025-1268, in printer drivers for its production printers, multifunction printers, and laser printers. This out-of-bounds issue may disrupt printing or allow malicious code execution when processed by a harmful application. The affected printer drivers include several versions of Canon’s Generic Plus drivers: Generic …
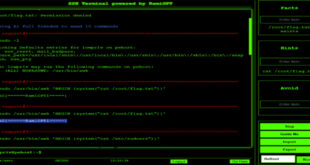
Read More »Within Minute, RamiGPT To Escalate Privilege Gaining Root Access
RamiGPT is an AI security tool that targets root accounts. Using PwnTools and OpwnAI, it quickly navigated privilege escalation scenarios on various VulnHub systems, achieving root access in under a minute. Configuration: Setting Up Your OpenAI API Key: To use RamiGPT, you need an OpenAI API key. Here’s how to …
Read More »Australian fintech database exposed in 27000 records
Cybersecurity researcher Jeremiah Fowler recently revealed a sensitive data exposure involving the Australian fintech company Vroom by YouX, previously known as Drive IQ. Fowler, in a report to Website Planet, found an unsecured Amazon S3 bucket with 27,000 records. This database contained sensitive personal information, such as driver’s licenses, medical …
Read More »Over 200 Million Info Leaked Online Allegedly Belonging to X
Safety Detectives’ Cybersecurity Team found a forum post where a threat actor shared a .CSV file with over 200 million records from X users. The team discovered data in a forum post on the surface web. This popular forum features message boards for database downloads, leaks, cracks, and similar topics. …
Read More »FBI investigating cyberattack at Oracle, Bloomberg News reports
The Federal Bureau of Investigation (FBI) is probing the cyberattack at Oracle (ORCL.N), opens new tab that has led to the theft of patient data, Bloomberg News reported on Friday, citing a person familiar with the matter. Earlier this month, Oracle alerted some healthcare customers that sometime after January 22, …
Read More »OpenAI Offering $100K Bounties for Critical Vulns
OpenAI has increased its maximum bug bounty payout to $100,000, up from $20,000, to encourage the discovery of critical vulnerabilities in its systems and products. The new bounty program is part of OpenAI’s broader security efforts, which also include funding research projects, ongoing adversarial testing, and collaboration with open-source software …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind