APT17 has recently been seen attacking Italian companies and government organizations. They are using a modified version of a well-known malware called 9002 RAT.
Two targeted attacks occurred on June 24 and July 2, 2024, according to an analysis by Italian cybersecurity company TG Soft published last week.
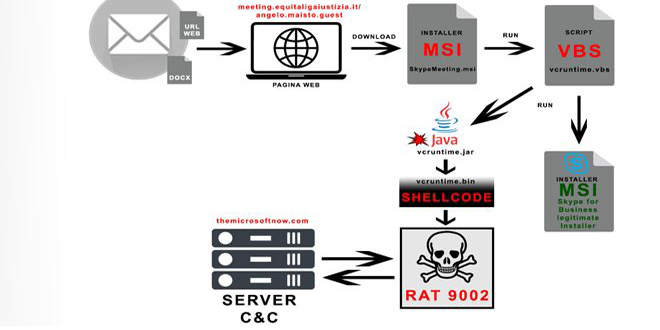
“The first campaign on June 24, 2024 used an Office document, while the second campaign contained a link,” the company noted. “Both campaigns invited the victim to install a Skype for Business package from a link of an Italian government-like domain to convey a variant of 9002 RAT.”
APT17, also known as DeputyDog and Ephemeral Hydra, was first identified by Mandiant (now owned by Google) in 2013. It was discovered that they used zero-day vulnerabilities in Microsoft’s Internet Explorer to carry out cyber espionage operations and target specific organizations.
It is also known as Aurora Panda, Bronze Keystone, Dogfish, Elderwood, Helium, Hidden Lynx, and TEMP.Avengers. It has some similar tools to another threat actor called Webworm.
The RAT known as 9002, also referred to as Hydraq and McRAT, became famous as the preferred cyber weapon during Operation Aurora in 2009The RAT known as 9002, also known as Hydraq and McRAT, gained fame as the preferred cyber weapon in Operation Aurora, which targeted Google and other major companies in 2009. It was later used in another campaign called Sunshop in 2013, where the attackers inserted harmful redirects into multiple websites.
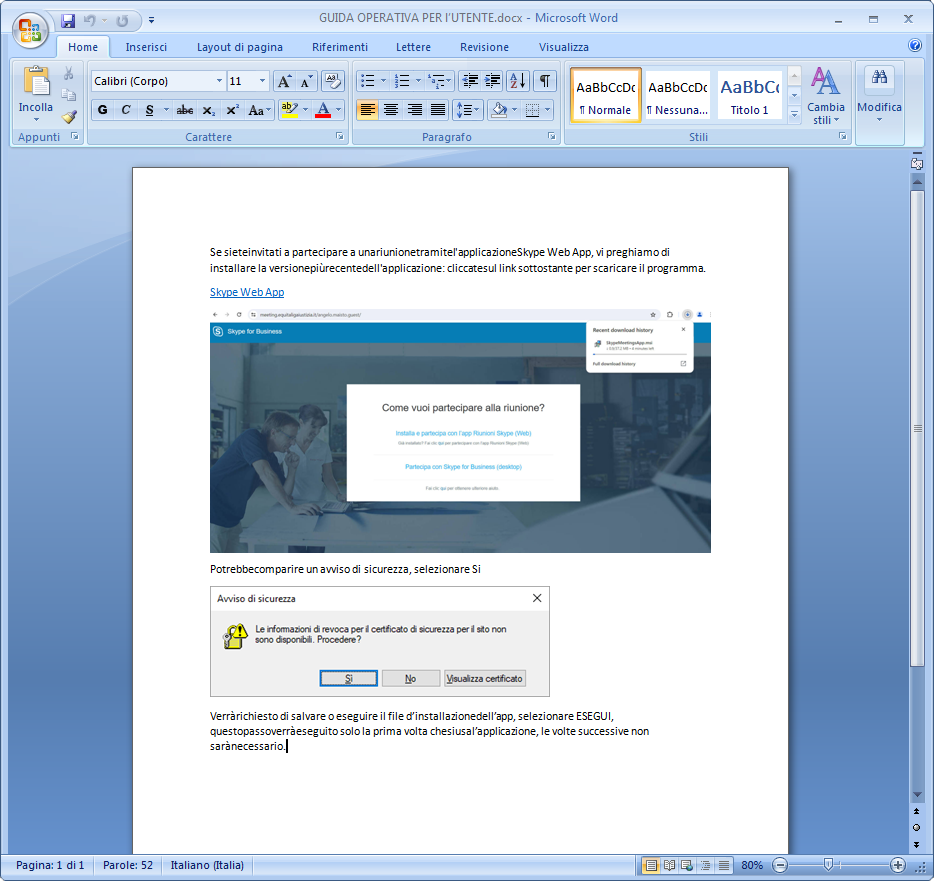
Attackers are using spear-phishing to trick people into downloading a Skype for Business installer called “SkypeMeeting.msi”.
The MSI package launches a Java archive file via a Visual Basic Script (VBS) and installs legitimate chat software on Windows. The Java application then decrypts and runs the shellcode that launches 9002 RAT.
The 9002The 9002 RAT is a Trojan that can monitor network traffic, take screenshots, explore files, control processes, and execute remote commands.rver to facilitate network discovery, among others.
“The malware appears to be constantly updated with diskless variants as well,” TG Soft said. “It is composed of various modules that are activated as needed by the cyber actor so as to reduce the possibility of interception.”
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind