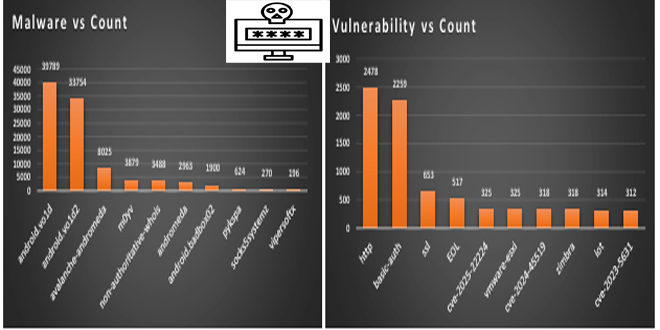
In early 2021, a hacker infiltrated OpenAI’s internal messaging systems and obtained information about the design of the company’s AI technologies.
The hacker stole information from an online forum where OpenAI employees discussed their latest technologies. However, the hacker was unable to access the systems where the company stores and develops its artificial intelligence.
OpenAI executives told employees about the incident in a meeting in April 2023 in San Francisco. They also informed the company’s board of directors.
But the executives decided not to share the news publicly because no information about customers or partners had been stolen. The executives did not consider the incident a threat to national security because they believed the hacker was a private individual with no known ties to a foreign government. The company did not inform the F.B.I. or anyone else in law enforcement.
For some OpenAI employees, the news raised fears that foreign adversaries such as China could steal A.I. technology that — while now mostly a work and research tool — could eventually endanger U.S. national security. It also led to questions about how seriously OpenAI was treating security, and exposed fractures inside the company about the risks of artificial intelligence.
Leopold Aschenbrenner, a program manager at OpenAI, sent a memo to the company’s board of directors. He expressed concern about the breach and argued that more should be done to protect OpenAI’s secrets from foreign adversaries, especially the Chinese government.
Leopold Aschenbrenner, a former OpenAI researcher, alluded to the security breach on a podcast last month and reiterated his worries.
Mr. Aschenbrenner claimed that he was fired by OpenAI in the spring for leaking information and believed that his dismissal was politically motivated. He mentioned this breach in a recent podcast, but there hasn’t been any previous reporting on the incident. He expressed concerns about OpenAI’s security, suggesting that it may not be able to prevent the theft of important secrets if foreign actors were to infiltrate the company.
“We appreciate the concerns Leopold raised while at OpenAI, and this did not lead to his separation,” an OpenAI spokeswoman, Liz Bourgeois, said. Referring to the company’s efforts to build artificial general intelligence, a machine that can do anything the human brain can do, she added, “While we share his commitment to building safe A.G.I., we disagree with many of the claims he has since made about our work. This includes his characterizations of our security, notably this incident, which we addressed and shared with our board before he joined the company.”
It is reasonable to fear that a hack of an American technology company may be connected to China. Brad Smith, the president of Microsoft, recently testified about how Chinese hackers used the company’s systems to launch an extensive attack on federal government networks.
OpenAI cannot stop people from working at the company based on their nationality, as per federal and California law. Experts suggest that excluding foreign talent from U.S. projects could greatly hinder the advancement of A.I. in the country. Click here to read the full report.
Source: New Your Times
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind