Cisco plans to release a patch for two zero-day flaws in its IOS XE devices on October 22. The first Cisco zero-day bug, which is named CVE-2023-20198, was reported on Oct. 16. By the time it was found, it had already been used by attackers to compromise over 10,000 Cisco devices. Cisco believes that all cyberattacks on its IOS XE devices are being perpetrated by the same threat actor.
Cisco recently updated its threat advisory on Oct. 20. They identified a new flaw, referred to as CVE-2023-20273, which was previously unknown. The flaw has a CVSS score of 7.2, which is slightly less severe. Both bugs are part of the same exploit chain.
By infosecbulletin
/ Friday , May 9 2025
YouTube has restricted access to at least four Bangladeshi television channels in India following a takedown request from the Indian...
Read More
By infosecbulletin
/ Friday , May 9 2025
Microsoft has fixed critical vulnerabilities in its core cloud services, including Azure Automation, Azure Storage, Azure DevOps, and Microsoft Power...
Read More
By infosecbulletin
/ Thursday , May 8 2025
The cyber threat landscape is rapidly changing, with a notable increase in ransomware activity in April 2025, driven by the...
Read More
By infosecbulletin
/ Thursday , May 8 2025
SonicWall has released patches for three security flaws in SMA 100 Secure Mobile Access appliances that could allow remote code...
Read More
By infosecbulletin
/ Thursday , May 8 2025
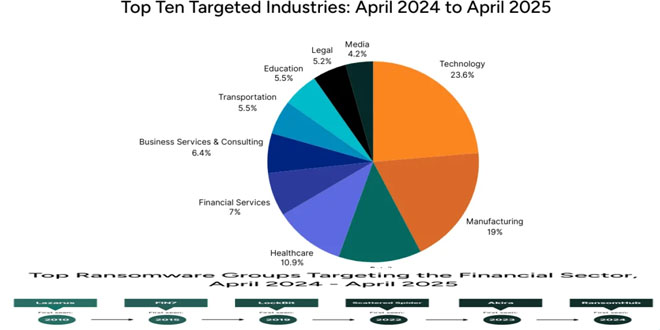
From April 2024 to April 2025, Flashpoint analysts noted that the financial sector was a major target for threat actors,...
Read More
By infosecbulletin
/ Thursday , May 8 2025
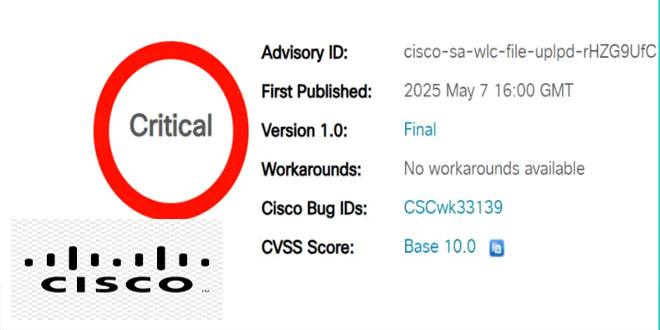
Cisco has issued a security advisory for a critical vulnerability in its IOS XE Software for Wireless LAN Controllers (WLCs)....
Read More
By infosecbulletin
/ Wednesday , May 7 2025
Attackers linked to the Play ransomware operation deployed a zero-day privilege escalation exploit during an attempted attack against an organization...
Read More
By infosecbulletin
/ Wednesday , May 7 2025
Hackers are exploiting an unauthenticated remote code execution vulnerability in the Samsung MagicINFO 9 Server to take control of devices...
Read More
By infosecbulletin
/ Tuesday , May 6 2025
CISA added the Langflow vulnerability, CVE-2025-3248 (CVSS score 9.8), to its Known Exploited Vulnerabilities catalog. Langflow is a popular tool...
Read More
By infosecbulletin
/ Tuesday , May 6 2025
Google has released its monthly Android security updates, addressing 46 vulnerabilities, including one that has been actively exploited. CVE-2025-27363 (CVSS...
Read More
Attackers used the first bug to gain initial access, and the second bug to escalate privileges after authentication, as stated in an email from Cisco announcing the upcoming patch release.
Cisco has clarified that they made a mistake in their earlier report about the bug. Initially, they thought the threat actor had combined a new zero-day with a patched vulnerability from 2021, which could have allowed the attacker to bypass the patch.
However, Cisco has now dismissed this theory. They stated this in a company statement. “The CVE-2021-1435 that had previously been mentioned is no longer assessed to be associated with this activity,” it said.
ALSO READ:
Chinese scammers exploit India’s digital payment ecosystem
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind