SonicWall has released patches for three security flaws in SMA 100 Secure Mobile Access appliances that could allow remote code execution. The vulnerabilities are listed below: CVE-2025-32819 (CVSS score: 8.8) : A vulnerability in SMA100 lets an authenticated remote attacker with SSL-VPN user access bypass checks and delete any file, …
Read More »Critical (CVSS 10) Flaw in Cisco IOS XE WLCs Allows RRA
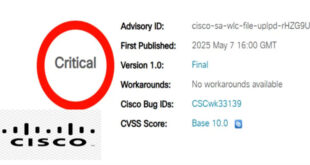
Cisco has issued a security advisory for a critical vulnerability in its IOS XE Software for Wireless LAN Controllers (WLCs). This vulnerability, known as CVE-2025-20188, has a CVSS score of 10, indicating the highest security flaw. The advisory highlights a vulnerability in the Out-of-Band Access Point (AP) Image Download feature …
Read More »
CVE-2025-29824
Play Ransomware Exploited Windows CVE-2025-29824 as Zero-Day
Attackers linked to the Play ransomware operation deployed a zero-day privilege escalation exploit during an attempted attack against an organization in the U.S. The attack occurred prior to the disclosure and patching of a Windows elevation of privilege zero-day vulnerability (CVE-2025-29824) in the Common Log File System Driver (clfs.sys) on …
Read More »Hacker exploited Samsung MagicINFO 9 Server RCE flaw
Hackers are exploiting an unauthenticated remote code execution vulnerability in the Samsung MagicINFO 9 Server to take control of devices and install malware. The server allows file uploads to update display content, but hackers are using this feature to upload malicious code. The flaw identified as CVE-2024-7399 was publicly disclosed …
Read More »CISA adds Langflow flaw to its KEV catalog
CISA added the Langflow vulnerability, CVE-2025-3248 (CVSS score 9.8), to its Known Exploited Vulnerabilities catalog. Langflow is a popular tool used for building agentic AI workflows. CVE-2025-3248 is a code injection vulnerability in the /api/v1/validate/code endpoint. An unauthenticated remote attacker can exploit it by sending specially crafted HTTP requests to …
Read More »Google Fixes Android Flaw (CVE-2025-27363) Exploited by Attackers
Google has released its monthly Android security updates, addressing 46 vulnerabilities, including one that has been actively exploited. CVE-2025-27363 (CVSS score: 8.1) is a high-severity vulnerability in the System component that allows local code execution without needing extra privileges. “The most severe of these issues is a high security vulnerability …
Read More »xAI Dev Leaks API Key for Private SpaceX, Tesla & Tweeter
A major security issue happened at Elon Musk’s AI company, xAI, when a developer accidentally posted a private API key on GitHub, making it publicly accessible for nearly two months. Exposed credentials allowed unauthorized access to private large language models (LLMs) fine-tuned for SpaceX, Tesla, and Twitter/X, revealing serious security …
Read More »SonicWall Exploit Chain Exposes Admin Hijack Risk via 2 CVEs
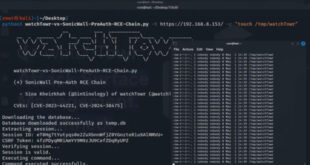
A new exploit chain for SonicWall’s Secure Mobile Access (SMA) appliances has been released by watchTowr Labs. It details how two vulnerabilities, CVE-2023-44221 and CVE-2024-38475, can be combined to allow remote, unauthenticated attackers to hijack admin sessions and run arbitrary code. SonicWall identifies CVE-2024-38475 as a critical vulnerability in the …
Read More »SonicWall Patched for SSRF Vulnerability in SMA1000 Appliances
SonicWall’s Product Security Incident Response Team (PSIRT) has released a critical update for its SMA1000 series appliances due to a Server-Side Request Forgery (SSRF) vulnerability, identified as CVE-2025-2170, with a CVSS base score of 7.2. The flaw in the SMA1000 appliances’ WorkPlace interface allows unauthenticated remote attackers to send unauthorized …
Read More »Patch Now! SonicWall Confirms Active Exploitation of SMA 100 Vulns
On April 29, 2025, SonicWall announced that two previously disclosed vulnerabilities in its SMA 100 Series appliances are being actively exploited. They urge customers to update to the latest secure firmware to avoid compromise. First identified in December 2023, CVE-2023-44221 has now been confirmed as under active exploitation. The vulnerability—assigned …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind