A major security issue happened at Elon Musk’s AI company, xAI, when a developer accidentally posted a private API key on GitHub, making it publicly accessible for nearly two months.
Exposed credentials allowed unauthorized access to private large language models (LLMs) fine-tuned for SpaceX, Tesla, and Twitter/X, revealing serious security vulnerabilities at major tech companies.
Philippe Caturegli, Chief Hacking Officer at Seralys, discovered the security incident and shared the leak on LinkedIn.
GitGuardian, a company that detects exposed secrets in code repositories, investigated the issue.
Their automated scanning systems monitor GitHub for sensitive credentials and detected a compromised API key on March 2, 2025.
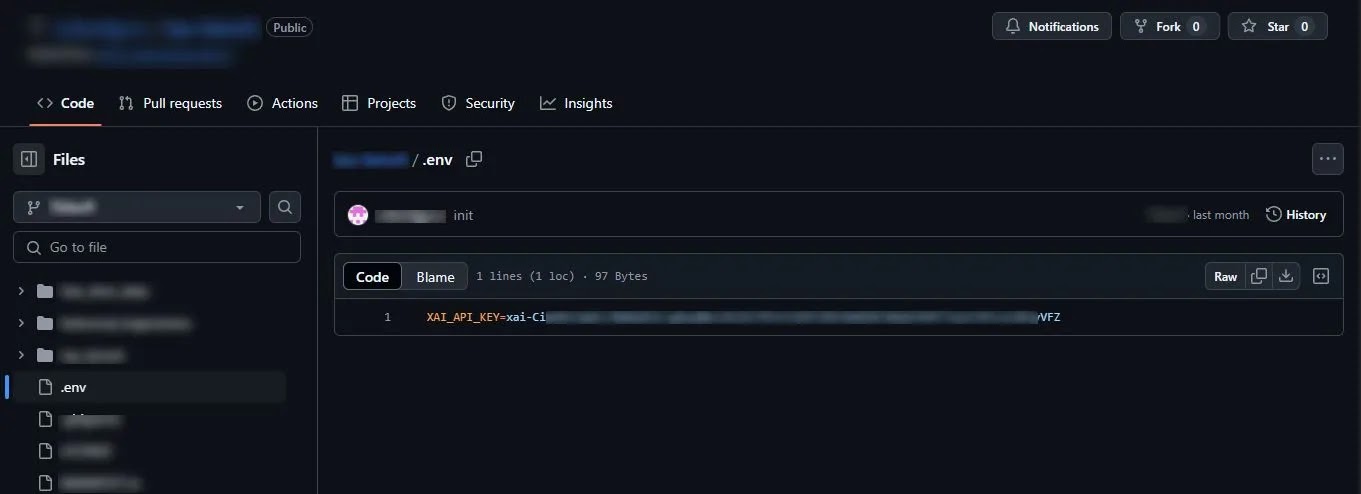
KrebsOnSecurity reports that the API key leaked by an xAI employee stayed active until April 30, despite the employee being notified right away. GitGuardian escalated the issue to xAI’s security team at that time.
According to Eric Fourrier from GitGuardian, the company found that “the key had access to at least 60 distinct data sets” including several unreleased and developmental versions of Grok models.
The leaked API credentials could have been used to query private custom-trained models including “grok-2.5V” (unreleased), “research-grok-2p5v-1018” (development), and “grok-spacex-2024-11-04” (private).
These models seem to be customized for managing internal data from Musk’s corporate network.
“The associated account not only has access to public Grok models but also to what appears to be unreleased, development, and private models,” GitGuardian noted in their communication to xAI.
The leak happened when a .env file was accidentally added to a public GitHub repository.
xAI did not provide public comment on the incident, and the repository containing the key was removed shortly after GitGuardian’s notification to the security team.
Caturegli noted that such “long-lived credential exposure highlights weak key management and insufficient internal monitoring, raising questions about safeguards around developer access and broader operational security”.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














