Ahead of the G-20 India Summit 2023, there has been a worrisome development as several hacker groups join forces under the #OPIndia banner, declaring their clear intention to carry out cyber attacks on India.
As India gears up to host global leaders at the upcoming G-20 summit, the alarming coordinated call for collective cyber attacks from groups driven by anti-India sentiments sounds a dire warning.
ALSO READ:
Hacker group again threat attack Bangladesh 19 September: CIRT Alert
Several hacker groups have chosen Indian websites as their targets for cyber attacks. Various Indian websites have already started to feel the effects of these attacks, as they are connected to the claims of the G20 cyber attack.
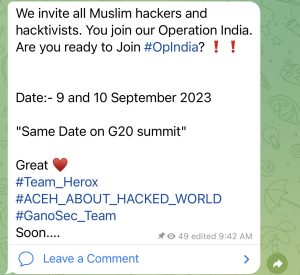
The renowned hacker collective, Jambi Cyber Team, has officially announced its upcoming operation, OpIndia, scheduled to commence on the 9th and 10th of September. Their focus will be directed towards various Indian websites.
The G20 India Summit 2023, focused on digital transformation, is scheduled to take place on September 9th and 10th, 2023. However, hackers have declared a cyber war against the nation.
OpIndia: Anticipated G20 Cyber Attacks by Hacker Collectives
G20 member countries, including the United States, the United Kingdom, Germany, and Saudi Arabia, will meet to discuss pressing global issues pertaining to peace and technological progress.
As the G20 preparations progress, hacktivists have cleverly used cybercrime forums to galvanize hackers, encouraging them to concentrate their endeavors on the digital infrastructure of India.
Here are the Twitter IDs of the hackers who have been involved in the G20 cyber attacks thus far:–
@RedNotice_id
@ganosecteam01
@Team_Herox
@Hacktivist_indo
@Dan4Indonesia
Jambi Cyber Team Cyber Attacks

As part of OpIndia and the G20 cyber attacks, Jambi Cyber Team has identified several Indian organizations’ websites as its prime targets. In their recent Twitter claim, they mentioned X and named numerous prominent hacker groups.
The confirmation of the cyber attacks on Indian websites is still pending, leaving the authenticity in question. The following Indian websites have been identified based on claims made by hacktivists on various social media platforms.
Hackers involved in the OpIndia and G20 cyber attacks have released samples of the data they obtained from various Indian websites. This involves sharing individuals’ registration details along with their photos on their respective social media platforms.
- The Unified District Information System for Education (UDISE)
- Educational Management Information System
- Sangamner College
- Shreehari
- MPSC Online
Hackers released data pertaining to several school students. In the samples, student names, parents’ names, member IDs, and other profile data from their dashboard were posted.
They have also indicated their intention to leak more data in the future, all while making derogatory comments about the state of Indian cybersecurity infrastructure.
Indonesian hackers have joined the G20 cyber attack initiative and have been actively encouraging other hackers to target Indian websites.
On Telegram, the Indonesian text regarding the G20 cyber attacks was translated as ‘time not specified,’ which has sparked speculations regarding the timing of Operation India.
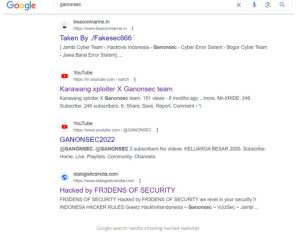
Prior to the start of the G20 Summit in 2023, Indian media the Cyber Express has uncovered multiple instances of Indian websites becoming the target of cyber-attacks. Most of the websites showing in Google search results belonging to India had their websites defaced.
The G20 cybersecurity measures must be strengthened in order to prevent security incidents. Everyone needs to prioritize cybersecurity, including governments, organizations, and individuals, due to the ongoing cyber warfare between nations.
(Media Disclaimer: This report relies on a combination of internal and external research gathered through diverse channels. It is important to note that the information presented here is intended solely for reference, and users are entirely accountable for their reliance on it. Infosecbulletin.com disclaims any responsibility for the accuracy or potential outcomes resulting from the use of this information.)
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














