A serious cybersecurity flaw in Cisco Webex Chat has been discovered, allowing unauthorized attackers to access the chat histories of organizations using the platform.
Identified in July 2024, the flaw exposed sensitive communications from potentially thousands of organizations, including IT help desks and customer service operations.
By F2
/ Tuesday , June 24 2025
The U.S. House of Representatives has banned congressional staff from using WhatsApp on government devices due to security concerns, as...
Read More
By F2
/ Tuesday , June 24 2025
Kaspersky found a new mobile malware dubbed SparkKitty in Google Play and Apple App Store apps, targeting Android and iOS....
Read More
By F2
/ Tuesday , June 24 2025
OWASP has released its AI Testing Guide, a framework to help organizations find and fix vulnerabilities specific to AI systems....
Read More
By F2
/ Tuesday , June 24 2025
In a major milestone for the country’s digital infrastructure, Axentec PLC has officially launched Axentec Cloud, Bangladesh’s first Tier-4 cloud...
Read More
By infosecbulletin
/ Monday , June 23 2025
A hacking group reportedly linked to Russian government has been discovered using a new phishing method that bypasses two-factor authentication...
Read More
By infosecbulletin
/ Wednesday , June 18 2025
Russian cybersecurity experts discovered the first local data theft attacks using a modified version of legitimate near field communication (NFC)...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
Cybersecurity researcher Jeremiah Fowler discovered an unsecured database with 170,360 records belonging to a real estate company. It contained personal...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
GreyNoise found attempts to exploit CVE-2023-28771, a vulnerability in Zyxel's IKE affecting UDP port 500. The attack centers around CVE-2023-28771,...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently included two high-risk vulnerabilities in its Known Exploited Vulnerabilities (KEV)...
Read More
By infosecbulletin
/ Monday , June 16 2025
SafetyDetectives’ Cybersecurity Team discovered a public post on a clear web forum in which a threat actor claimed to have...
Read More
Proof-of-Concept and Real-World Impact:
Researchers developed a proof-of-concept script showing how attackers can exploit a vulnerability using only minimal information, like the app UUID in the widget’s JavaScript or the domain hosting the chat, according to the Ophion Security blog.
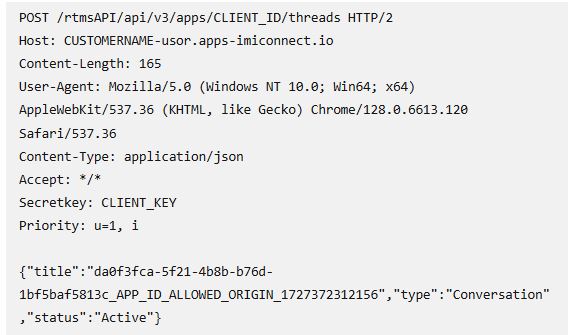
Organizations using Cisco Webex Chat should promptly audit their systems to ensure they have the latest patched version of the software.
#
VMware issued a critical security advisory, VMSA-2025-0003, for vulnerabilities in VMware Aria Operations for Logs, VMware Aria Operations, and VMware Cloud Foundation.
The vulnerabilities CVE-2025-22218 to CVE-2025-22222 allow admin-level actions, posing a serious risk to affected systems.
VMware has released patches to address vulnerabilities rated with CVSSv3 scores between 5.2 and 8.5, urging customers to update promptly.
Affected Products
The vulnerabilities impact the following VMware products:
VMware Aria Operations for Logs (version 8.x)
VMware Aria Operations (version 8.x)
VMware Cloud Foundation (versions 4.x and 5.x)
VMware advises customers to promptly apply the patches from version 8.18.3 of VMware Aria Operations for Logs and VMware Aria Operations to fix vulnerabilities.

 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














