Researchers at Wiz discovered a complex phishing campaign using Amazon’s Simple Email Service (SES) for large-scale attacks, showing how hacked cloud credentials can evade standard email security measures. The attack, identified in May 2025, began with stolen AWS access keys a common attack vector that Wiz observes “tens of newly …
Read More »TimeLine Layout
September, 2025
-
8 September
SafePay Ransomware
SafePay Ransomware Attacks 73 Orgs in a Single MonthThe global ransomware landscape continues to shift in 2025, with SafePay rapidly emerging as one of the most active and disruptive groups. In June, SafePay claimed responsibility for attacks on 73 victim organizations, a record-breaking monthly tally that placed it at the top of Bitdefender’s Threat Debrief rankings. The surge …
Read More » -
7 September
Bangladesh Cyber Threat Landscape- 2024
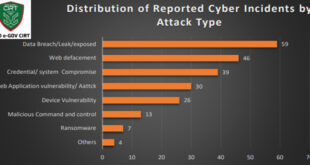
602 Vuln exploited: Afftected daily 905 IP In Bangladesh in 2024Bangladesh Cyber Threat Landscape 2024, by BGD e-GOV CIRT, reveals a sharp escalation in cyber threats across Bangladesh. The year saw a surge in ransomware, phishing, hacktivism, and data breaches, affecting both public and private sectors. Critical vulnerabilities in outdated systems, increased use of the dark web for trading stolen …
Read More » -
7 September
AI-powered malware hit 2,180 GitHub accounts in “s1ngularity” attack
Investigations into the Nx “s1ngularity” NPM supply chain attack have unveiled a massive fallout, with thousands of account tokens and repository secrets leaked. According to a post-incident evaluation by Wiz researchers, the Nx compromise has resulted in the exposure of 2,180 accounts and 7,200 repositories across three distinct phases. Wiz …
Read More » -
6 September
ISC2 Aims to Bridge DFIR Skill Gap with New Certificate
ISC2 has launched a Threat Handling Foundations Certificate to assist cybersecurity experts in enhancing Digital Forensics and Incident Response (DFIR) amid rising disruptive attacks that may cause breaches. DFIR is a complex field of incident response. This four-course program offers practical experience in building a DFIR program, digital forensics basics, …
Read More » -
4 September
Misconfig Server Exposed 378GB of Navy Federal Credit Union Files
Jeremiah Fowler, a cybersecurity researcher, found an unprotected server revealing 378 GB of Navy Federal Credit Union files, including operational Tableau data, but no customer details. The misconfigured server has been found with sensitive internal files from Navy Federal Credit Union (NFCU), the largest credit union for military members. He …
Read More » -
4 September
Mis-Issued TLS Certificate Exposes 1.1.1.1 DNS Services to Exploitation
Security researchers found that three unauthorized TLS certificates were issued in May 2025 for 1.1.1.1, the public DNS service operated by Cloudflare. Improperly issued certificates by the Fina RDC 2020 authority could let attackers intercept and decrypt DNS queries, revealing users’ browsing habits. However, if a malicious or unauthorized party …
Read More » -
4 September
Hacker accessed Brazil’s Real-Time Payment System: Attempted grabing $130M
Attackers attempted to steal $130 million from Brazil’s real-time payment system on Friday by wielding valid credentials for an IT service provider. Unauthorized funds were transferred through a breach of the IT system of Sinqia, a Brazilian subsidiary of Evertec. Some of the funds have been recovered. Sinqia, based in …
Read More » -
3 September
NVIDIA Releases Security Updates for BlueField, DOCA, Mellanox, ConnectX and NVOS
NVIDIA has issued important software updates to fix vulnerabilities in its BlueField DPUs, DOCA software, Mellanox DPDK, ConnectX network adapters, Cumulus Linux, and NVOS products. Many of these issues have high to critical severity and can lead to privilege escalation, denial of service, or information disclosure. The most severe vulnerability, …
Read More » -
3 September
Android Alert: Google Patches 120 Flaws, Two Zero-Days Under Attack
Google released security updates for September 2025, fixing 120 security flaws in Android, including two vulnerabilities actively exploited in targeted attacks. The vulnerabilities are listed below: CVE-2025-38352 (CVSS score: 7.4): A privilege escalation flaw in the Linux Kernel component CVE-2025-48543 (CVSS score: N/A): A privilege escalation flaw in the Android …
Read More »
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind