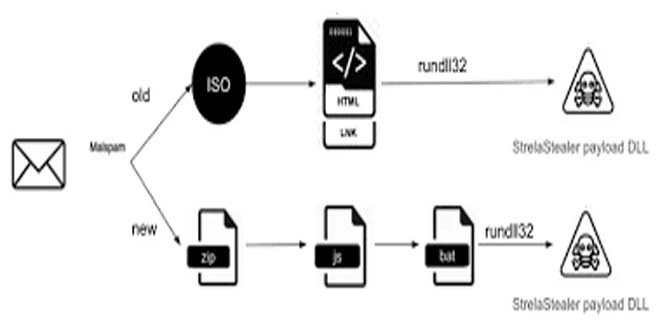
StrelaStealer malware steals email login data from popular email clients and sends it to the attacker’s server. The attacker can then use this information to launch more attacks. Since its first appearance in 2022, the threat actor has carried out many email campaigns and shows no sign of stopping.
Unit42 researchers have found a wave of big StrelaStealer campaigns affecting more than 100 organizations in the EU and U.S. These campaigns involve spam emails with attachments that activate the StrelaStealer’s DLL payload.
By infosecbulletin
/ Sunday , April 28 2024
This May, Dhaka, Bangladesh, will host Phoenix Summit 2024, a landmark event in the global cyber security arena. Set from...
Read More
By infosecbulletin
/ Saturday , April 27 2024
The worm was first discovered in a 2023 post by security firm Sophos. It became active in 2019 when a...
Read More
By infosecbulletin
/ Friday , April 26 2024
Palo Alto Networks has given urgent advice to the remediation of a critical vulnerability, known as CVE-2024-3400, which attackers have...
Read More
By infosecbulletin
/ Friday , April 26 2024
Organizations across all sectors and of all sizes are too frequently impacted by damaging ransomware incidents. Many of these incidents...
Read More
By infosecbulletin
/ Friday , April 26 2024
According to the report by several Indian media, social media platform Meta will withdraw its entire service from India if...
Read More
By infosecbulletin
/ Friday , April 26 2024
Someone is pretending to be Rajshahi University Vice-Chancellor, Professor Dr. Golam Sabbir Sattar, by creating a fake email account and...
Read More
By infosecbulletin
/ Friday , April 26 2024
Platform BreachForum, bad actor perell, same person who claimed to expose the data of "Bharat Sanchar Nigam Limited" BSNL for...
Read More
By infosecbulletin
/ Thursday , April 25 2024
“Our customers are our utmost priority and we are wholeheartedly dedicated to safe guarding their interests. It has come to...
Read More
By infosecbulletin
/ Thursday , April 25 2024
CISA issued eight advisories about Industrial Control Systems (ICS) on April 25, 2024. The advisories share important information about security...
Read More
By infosecbulletin
/ Thursday , April 25 2024
Google fixed a serious Chrome bug known as CVE-2024-4058 in the ANGLE graphics layer engine along with four vulnerabilities in...
Read More
Attackers change email attachment file formats to evade detection. This prevents detection from previously generated signatures or patterns. The malware author frequently updates the DLL payload with improved obfuscation and anti-analysis techniques. This makes analysis more difficult for analysts and security products.
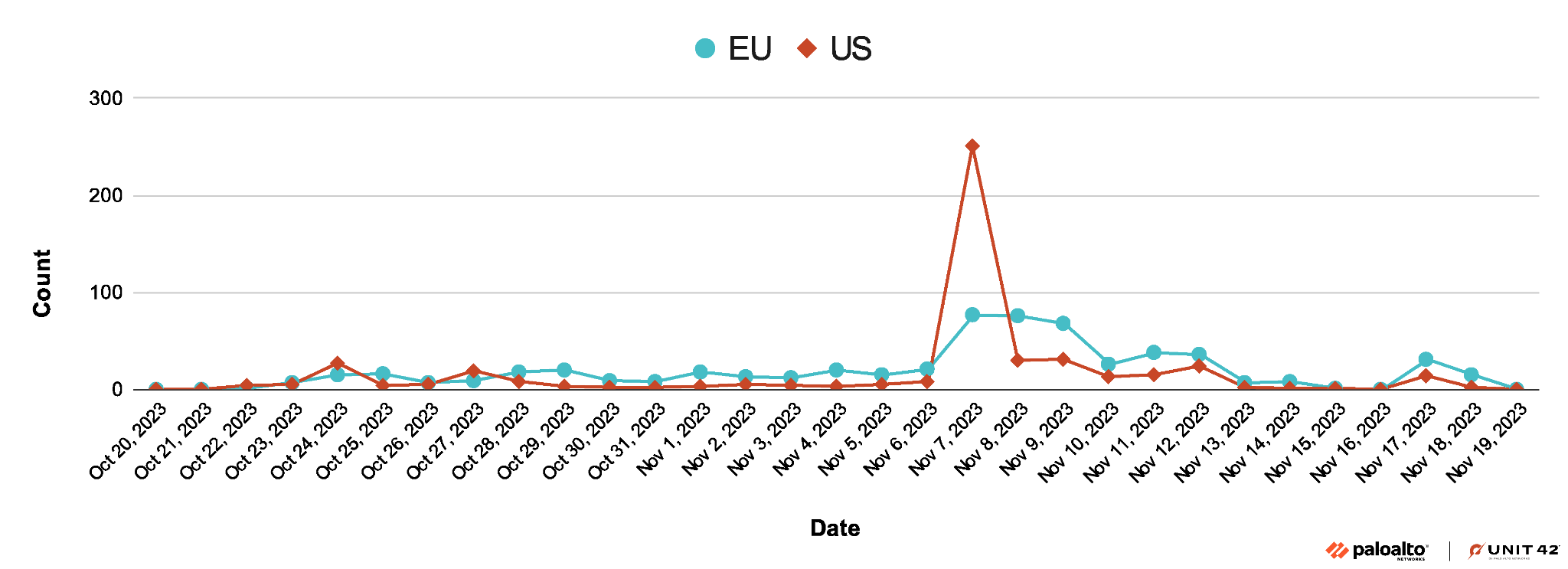
Last Large-Scale Campaign of 2023:
StrelaStealer has been causing multiple large-scale campaigns. The most recent campaign in November 2023 targeted organizations in the U.S. and EU. Figure 1 shows the timeline of this campaign.
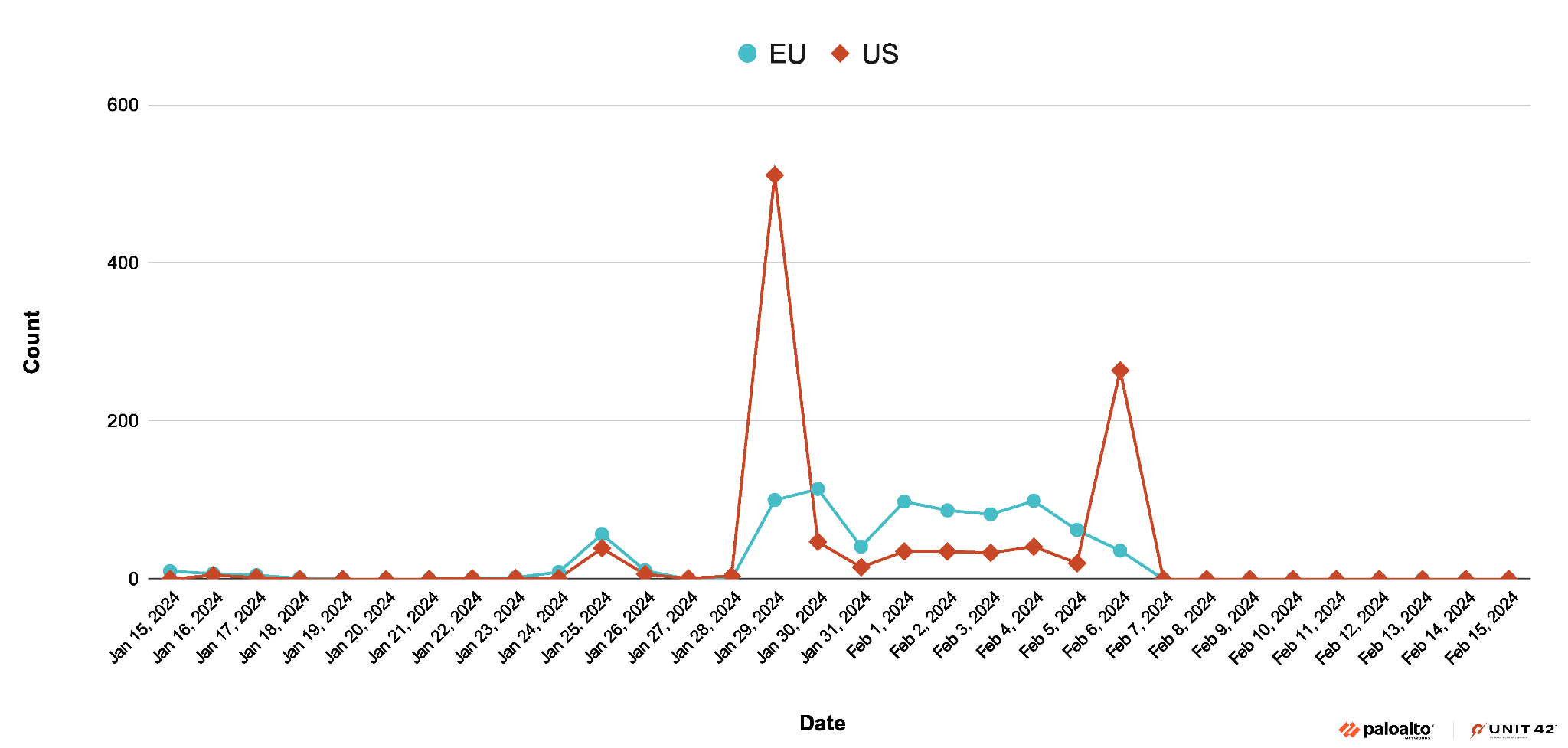
Recent Large-Scale Campaign in 2024
In January 2024, the StrelaStealer threat actors started a big campaign targeting organizations in the same areas as before. The campaign peaked on Jan. 29, 2024.
The language of the StrelaStealer spam email seen during this campaign is localized and the subject line has the pattern of Factura/Rechnung/invoice####. Figure 3, below, is a sample email in German.
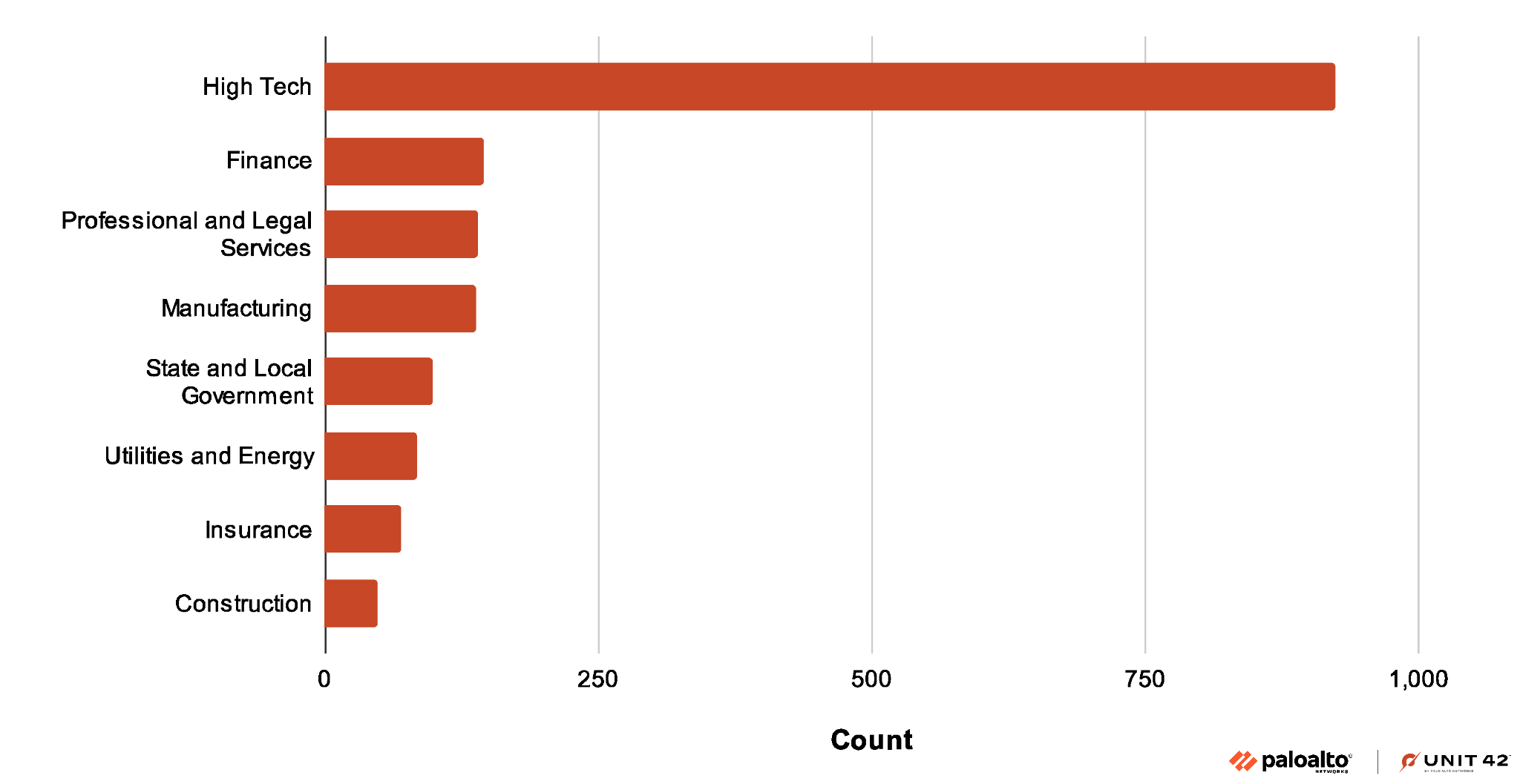
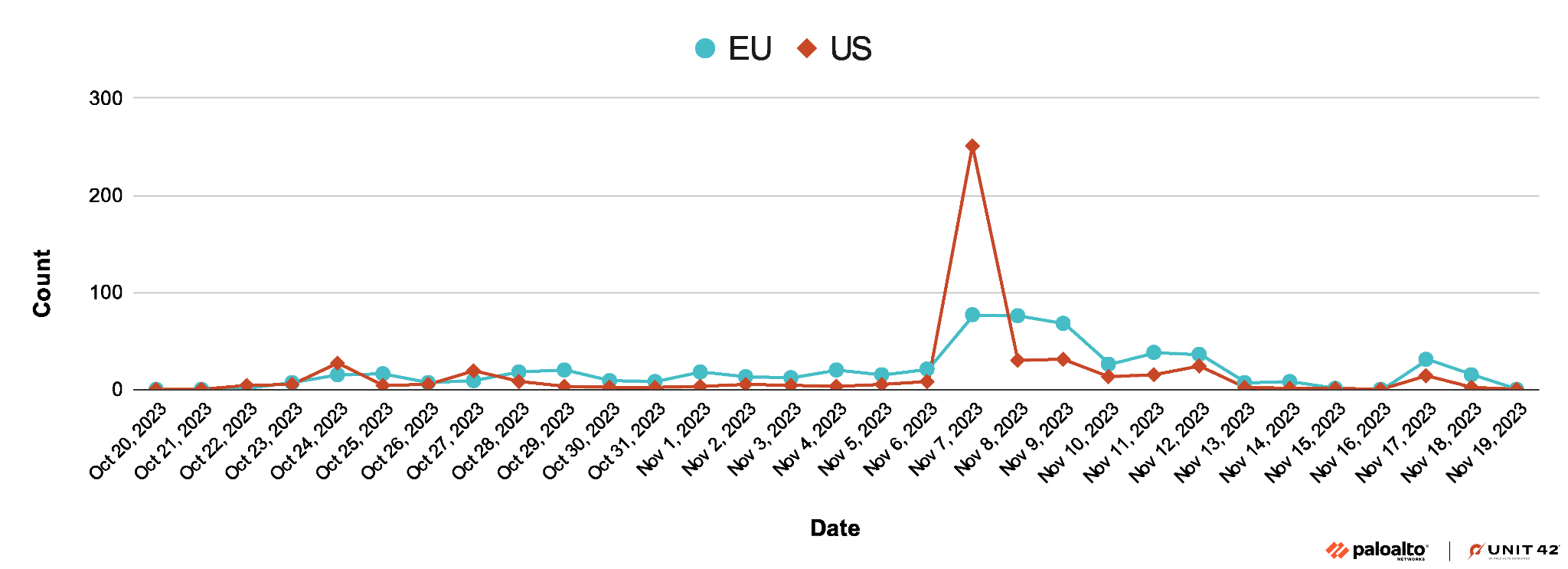 Figure 4 shows that while this recent campaign seems to target organizations in many industries, organizations in the high tech industry have been the largest target.
Figure 4 shows that while this recent campaign seems to target organizations in many industries, organizations in the high tech industry have been the largest target.
For the technical analysis click here.


 Figure 4 shows that while this recent campaign seems to target organizations in many industries, organizations in the high tech industry have been the largest target.
Figure 4 shows that while this recent campaign seems to target organizations in many industries, organizations in the high tech industry have been the largest target.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind