“Sarcoma” ransomware group attacked a well known Bangladeshi insurance company named “Popular life insurance company ltd”. The threat actor keeps an option to release the full data if their demand doesn’t meet up within 5 days.

According to the threat actor, approximately 36 GB of data, including attachments and SQL files, has been stolen. It is not clear that what types of data have actually been lost. But the data may include Personally Identifiable Information (PII).

“The Sarcoma Group is a relatively new ransomware group that emerged in October 2024,” said Tenable Senior Staff Researcher Satnam Narang. “As of the end of October 2024, the group has listed 38 companies on their data leak site, a place where ransomware groups post information on their alleged victims, teasing some of the stolen information, the amount of data stolen as well as a countdown for when the information will be published if a ransom is not paid. Four of the 38 alleged victims are located in Australia with over 700GB of stolen data from these organizations. So far, only one affected entity has had their data published by the group, while the timer has been paused for another.
Sarcoma ransomware uses aggressive tactics and a double extortion model: it encrypts victims’ data and threatens to leak it online if the ransom isn’t paid. Its origins are unclear, but security experts think it may be connected to an Eastern European cybercriminal group known for sophisticated malware. This makes Sarcoma a significant threat.
A Global Reach with Focused Targets:
Sarcoma ransomware has affected victims worldwide, impacting various industries. Here are some examples of its operations and resulting consequences:
Healthcare Organisations: They are often targeted because they hold important patient information and can affect essential services.
Manufacturing Disruptions: Manufacturing companies around the world are facing data breaches, operational issues, and possible production delays.
Financial Institutions: The financial sector has been targeted, with banks and credit unions at risk of data breaches and financial losses.
Kill Chain:
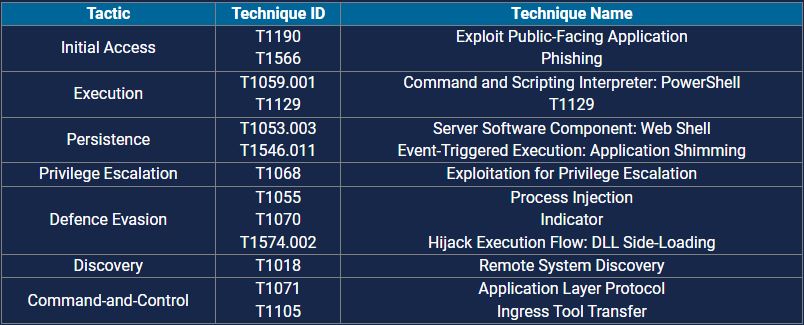
The attack reveals a concerning trend: cybercriminals are becoming more sophisticated in their tactics. For companies like Popular Life Insurance Co. Ltd., this emphasizes the need for strong cybersecurity measures. The negligence in safeguarding sensitive data has not only compromised organizational information but also potentially exposed individuals’ PII, reports BCSI.
Groups like Sarcoma represent an evolving threat, putting all organizations at risk. Their increasing reputation and sophisticated tactics require urgent action to enhance defenses. Ignoring these vulnerabilities could result in more breaches, financial losses, and a decline in public trust.
Here are some crucial steps organizations can take to mitigate the risk of Sarcoma ransomware and similar threats like Supply Chain Visibility, Third-Party Risk Management, Regular Backups, Patch Management, Endpoint Security Solutions, Network Segmentation and Incident Response Planning and so on.
Recently, Bangladesh has experienced cyber attack on NBR, DESKO, Titas, Globe pharmaceuticals, Confidence group, Road Transport and Highways Division (RTHD), TranscomBD, and so on including Lumma C2 malware attack Bangladeshi several websites.
Antivirus manufacturer Kaspersky inform that it has detected over 34,000 ransomware attacks targeting various organizations in Bangladesh from January to December 2023 in a press release.
(Media Disclaimer: This report is based on research conducted internally and externally using different ways. The information provided is for reference only, and users are responsible for relying on it. Infosecbulletin is not liable for the accuracy or consequences of using this information by any means)
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














