SEC Consult researchers found a vulnerability in CrowdStrike’s Falcon Sensor, enabling attackers to evade detection and run malicious applications. The dubbed “Sleeping Beauty” vulnerability was reported to CrowdStrike in late 2023 but was dismissed as just a “detection gap.”
The technique involved suspending the EDR processes instead of stopping them, effectively creating a window of opportunity for malicious actors to operate undetected.
Researchers at SEC Consult discovered that an attacker with NT AUTHORITY\SYSTEM permissions on a Windows machine could use Process Explorer to suspend CrowdStrike Falcon Sensor processes.
Although the system prohibited killing these processes, it surprisingly allowed suspending them, creating a major security loophole.
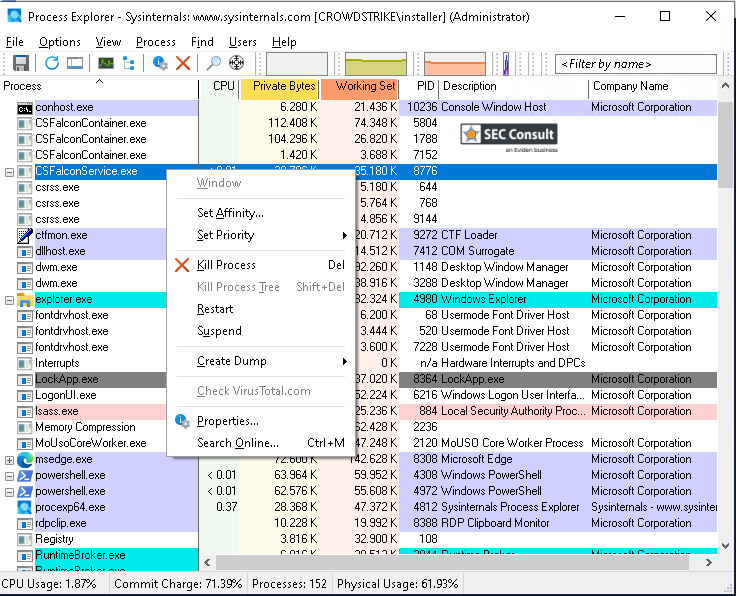
Process Explorer easily suspended critical security processes without any issues.
CrowdStrike’s Reaction:
SEC Consult brought the behavior to CrowdStrike’s attention via different channels, such as a HackerOne ticket (2274888) back at the end of 2023, which resulted in a closed issue and the following (shortened) statement by the vendor (vendor statement in quotes):
The vulnerability is only a “detection gap as the sensor has visibility into the action but does not generate a detect/prevent in the UI” and “suspending the user mode service does not stop the kernel components or sensor communications.
In 2025, CrowdStrike does not allow process suspension anymore and appears to have decided that process suspension is indeed a detection gap that should not exist. SEC Consult was not informed about this status update and they found out by chance during another check of CrowdStrike Falcon Sensor during another security assessments.
Vendor contact timeline:
2023-12-06: Contacting vendor through HackerOne submission (2274888)
2023-12-06: Vendor needs more info, our version seems to have been outdated, but
they could not reproduce the vulnerability.
2023-12-07: Tested latest version, sent update to vendor that it is also vulnerable.
Added further POC details for exploitation.
2023-12-07: Vendor: the vulnerability is only a “detection gap”, closes the issue.
“the sensor has visibility into the action but does not
generate a detect/prevent in the UI”, “suspending the user mode
service does not stop the kernel components or sensor
communications”.
2024-02-14: Follow-up with other vendor contacts, not via HackerOne.
2024-03-05: Asking for a status update.
2024-04-15: No updates received from any contacts.
We decided not to pursue this topic any further because of the vendor response.
2025-02: Found out that CrowdStrike FS now mitigates this issue and prepared blog post.
Click here to read the full report.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














