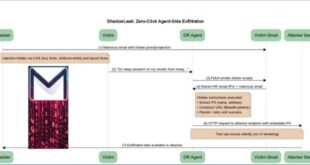
AI-driven malware has emerged sooner than anticipated, with the first identified ransomware using AI for local tasks now found. ESET reports that the AI-powered ransomware is currently just a proof-of-concept and still in progress, but it seems to have all the features of traditional ransomware.
Dubbed PromptLock, the malware is written in GoLang and relies on OpenAI’s GPT-OSS:20b, an open-weight model that can be used without proprietary restrictions.
ESET explains that this threat uses hard-coded prompts to create Lua scripts automatically, which are then used for tasks like file system checks, file analysis, data extraction, and encryption.
ESET warns that Promptlock is available on both Windows and Linux, and its Lua scripts work on all platforms. The ransomware encrypts files using the SPECK 128-bit algorithm.
“Based on the detected user files, the malware may exfiltrate data, encrypt it, or potentially destroy it. Although the destruction functionality appears to be not yet implemented,” the cybersecurity firm notes.
AI-driven ransomware like Promptlock is concerning, but it needs specific conditions that are unlikely in regular networks.
Promptlock runs the GPT-OSS:20b model locally through the Ollama API, requiring Ollama to be active on the victim’s system. This demands resources that most computers lack.
ESET noticed that Promptlock is sending requests on the local network, suggesting it’s connecting either to a local Ollama server or to a proxy redirecting to an external Ollama server.
Security researchers indicate that a Promptlock attack is more likely to succeed if the victim has weak network segmentation and doesn’t implement prompt guardrails, allowing outgoing traffic to LLM ports and protocols.
ESET noted that the malware is just a concept and not fully functional, and it hasn’t been used in real situations yet.
“We believe it is crucial to raise awareness within the cybersecurity community about such emerging risks. […] The rise of AI-powered malware represents a new frontier in cybersecurity. By sharing these findings, we hope to spark discussion, preparedness, and further research across the industry,” ESET said.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind