A recent Aqua Security report highlights major security risks in Kubernetes policy enforcement, especially with Open Policy Agent (OPA) Gatekeeper. Although OPA Gatekeeper is commonly used for security policies in Kubernetes, researchers found methods to bypass its controls due to frequent misconfigurations and weak policies.

According to the report, “Implementing Kubernetes securely can be a daunting task.” OPA Gatekeeper is an essential tool that provides out-of-the-box security policies for Kubernetes, but Aqua Security’s research highlights critical flaws that may allow attackers to evade restrictions. The report warns that “seemingly secure rules, such as those used in OPA Gatekeeper, can be bypassed if not carefully configured.”
A key vulnerability identified is the ability to bypass the k8sallowedrepos policy, which limits access to certain container image repositories. Researchers found that misconfigurations, like missing trailing slashes in policies, can allow unauthorized image pulls. “We found a way to bypass the k8sallowedrepos policy. If the user omits placing / at the end of the constraint repos value, this enables attackers to completely bypass the policy,” the report states.
Two major attack scenarios were demonstrated in the report:
Domain Bypass:

If an organization restricts images to my-ecr.azurecr.io, attackers can exploit the absence of a trailing slash by using a subdomain like my-ecr.azurecr.io.attacker.com. Kubernetes may mistakenly accept this as a valid source, circumventing security measures.
Docker Hub Namespace Bypass:
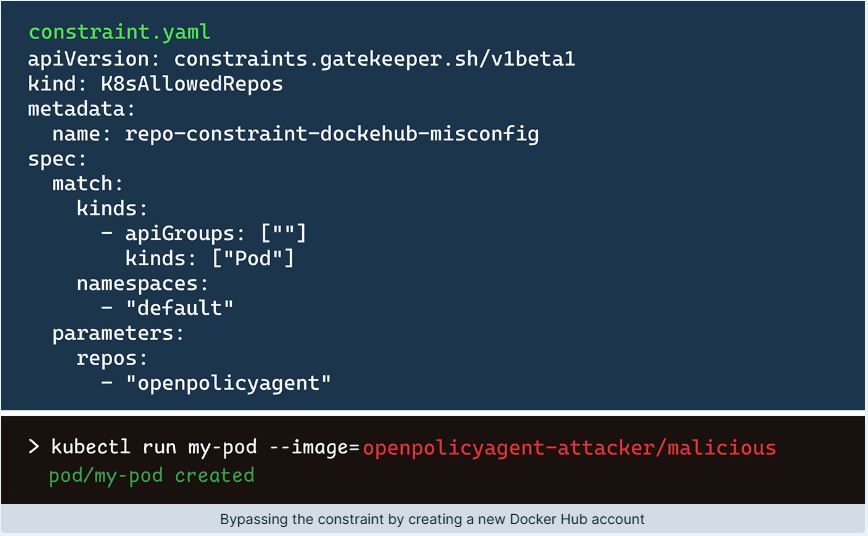
The report explains that attackers can create misleading repositories on Docker Hub, like “openpolicyagent-attacker,” to exploit poorly configured policies. It highlights a method called “namespace bypass,” allowing attackers to use repository names that match permitted values.
A major concern is the Rego policy logic in OPA Gatekeeper. The report notes that functions like any_prefix_match() can be misused to match unintended values, enabling attackers to deploy malicious containers. Using functions such as endswith(), startswith(), and any_prefix_match() on domains, repositories, or namespaces poses risks.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














