A sophisticated malware campaign is targeting military and government entities in Bangladesh. It uses social engineering to deliver malicious files disguised as official documents, aiming to infiltrate secure networks, steal credentials, and access sensitive systems.
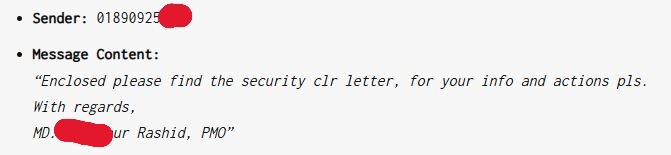
The attack starts with a WhatsApp message that forwards a file (like 508.rar) pretending to be a security clearance letter. The sender, posing as a high-ranking military officer, such as “MD. Mahbubur Rashid, PMO,” aims to create legitimacy and urgency.
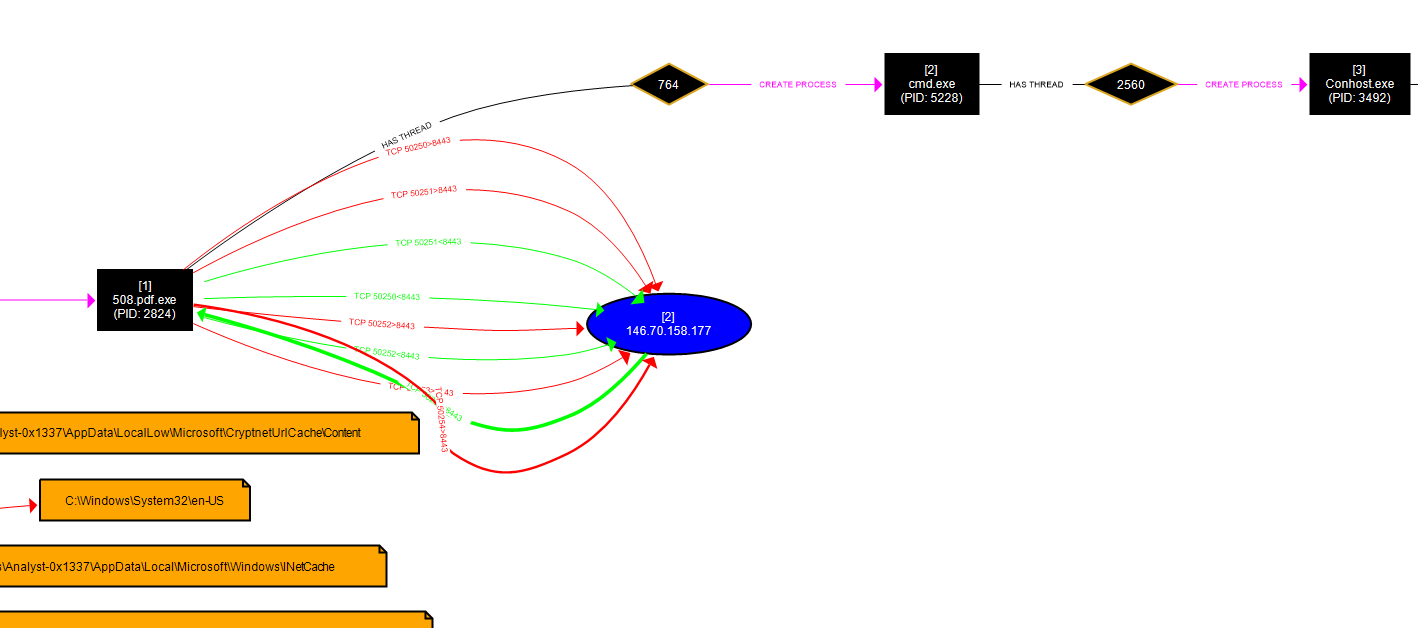
The RAR archive, once extracted, contains an executable or script that runs harmful code. Following past attack trends, this payload probably includes:
Remote Access Trojans (RATs): Providing attackers with full access to the compromised system.
Credential Harvesters: Capturing login credentials of government personnel.
Keyloggers and Screen Capture Modules: Recording keystrokes and screenshots to extract sensitive data.
Lateral Movement Tools: Enabling attackers to propagate within the targeted network.
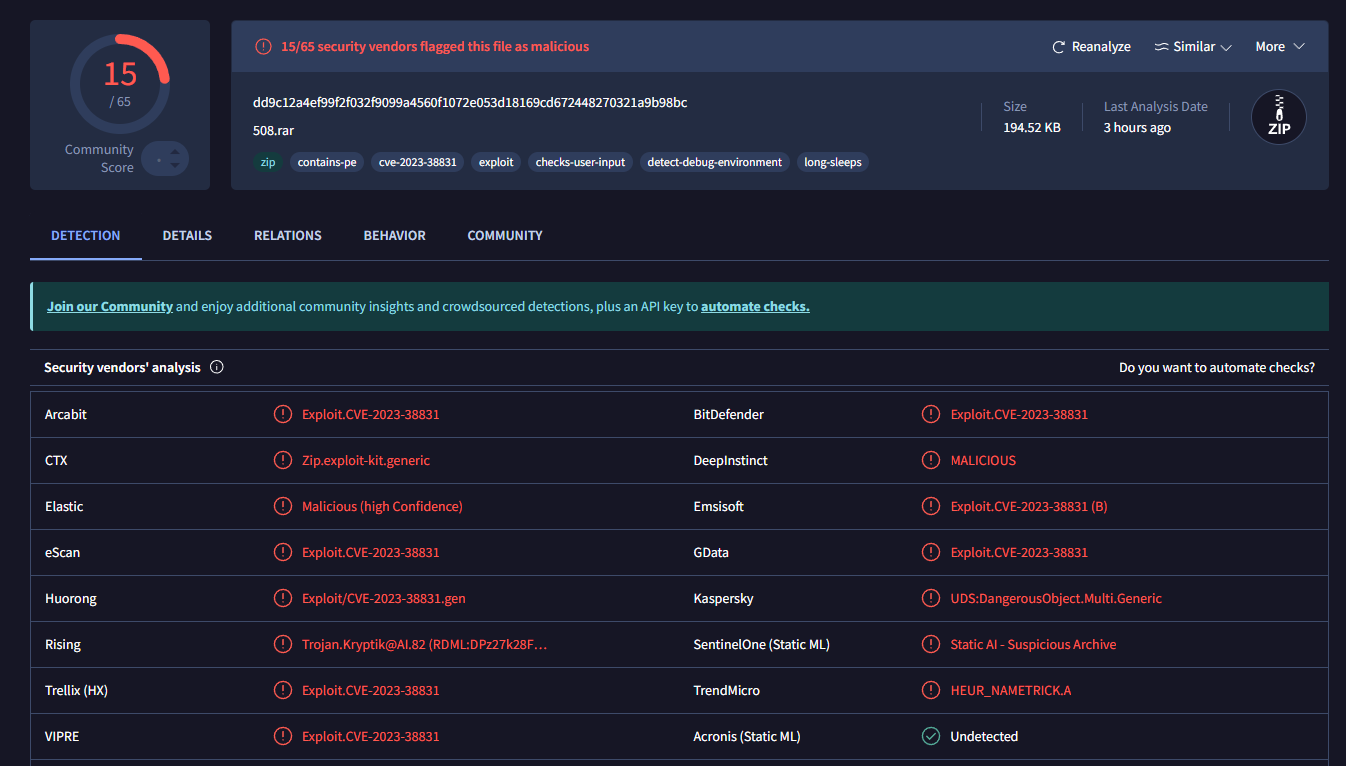
Threat Intelligence Community of Bangladesh warns that a malware campaign is exploiting the critical WinRAR vulnerability (CVE-2023-38831) in versions before 6.23. This vulnerability allows malicious files, like 508.rar, to execute arbitrary code on affected systems, which may lead to unauthorized access or malware installation.
The malware 508.pdf.exe connects to the IP address 146.70.158.177, which is operated by M247 Europe SRL, a VPN provider in Paris, France. While M247 offers various hosting and connectivity services, it has also been associated with suspicious web traffic and potential fraud.
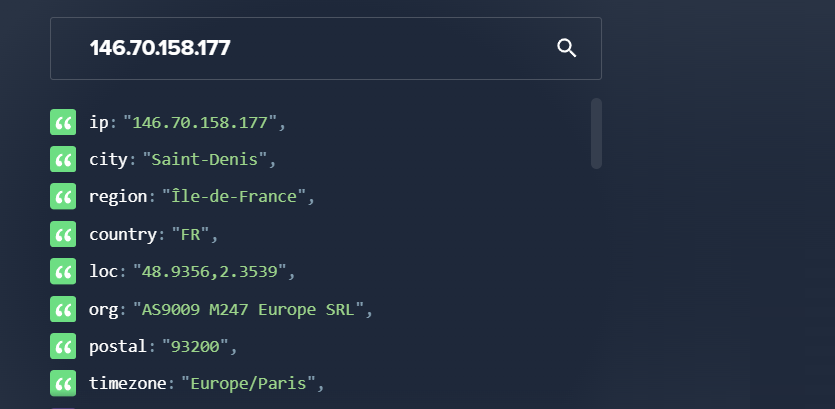
Confirmed Indicators of Compromise (IoC):
IP Address: 146.70.158.177
Remote Port: 8443 (TLS encrypted communication)
Hosting Provider: M247 Europe SRL
Usage Type: Data Center/Web Hosting/Transit
Given M247’s past involvement in suspicious activities, it is very likely that this infrastructure is being used as a Command and Control (C2) server to steal sensitive data or control infected systems.
The analyzed malware from this attack is not currently listed in major threat intelligence databases.
MD5 Hash: 455a3eab4fc7d2f77cea7a3bc9eb92b9
SHA256Hash: fc0c2e389eb3be3f041f84e1a89ba93d40374109cd20a2395b68f8c698c788a
Any system running WinRAR below version 6.23 is at immediate risk. It is crucial for all government and military personnel to update their WinRAR software to the latest secure version.
Social Engineering Tactics:
Spoofed Identities: Attackers impersonate military officials to gain trust
Urgency and Importance: Messages demand quick responses to avoid scrutiny and security measure
Forwarded Messages: They imitate real message chains to evade detection
Impact on National Security:
Exposure of Classified Information: Compromised accounts can leak sensitive documents and communications.
Network Infiltration: Attackers can gain long-term access to military and government IT systems.
Operational Disruption: Malicious activities like ransomware can disrupt government services and operations.
Mitigation Measures:
User Training: Train government and military staff to recognize and report suspicious messages and attachment
Message Filtering: Default to blocking unknown archive and executable file
Threat Detection: Use behavioral analysis tools to identify unusual activitie
Endpoint Protection: Ensure all devices have up-to-date antivirus and endpoint solution
Multi-Factor Authentication: Implement MFA to reduce credential theft risk
Update WinRAR: Users must upgrade to WinRAR 6.23 or later to prevent CVE-2023-38831 exploitation
Network Monitoring: Monitor logs for connections to the known C2 infrastructure (146.70.158.177) and block any detected traffic
This campaign emphasizes the ongoing cyber threats to Bangladesh’s critical sectors. BCSI urges all government and military entities to be more vigilant and take proactive security measures. Investigations are underway to determine the source of the attack and lessen its effects.
This Adtech Company is Powering Surveillance of U.S. Military Personnel
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














