LockBit restarted their ransomware operation on a new infrastructure after law enforcement disrupted their servers. Now, they threat to target the government sector more with their attacks.
The gang posted a long message admitting their negligence and sharing their future plans. “Due to my personal negligence and irresponsibility I relaxed and did not update PHP in time.” The threat actor says that the victim’s admin and chat panels server and the blog server were running PHP 8.1.2 and were likely hacked using a critical vulnerability tracked as CVE-2023-3824.
By infosecbulletin
/ Wednesday , September 17 2025
Check point, a cyber security solutions provider hosts an event titled "securing the hyperconnected world in the AI era" at...
Read More
By infosecbulletin
/ Tuesday , September 16 2025
Cross-Site Scripting (XSS) is one of the oldest and most persistent vulnerabilities in modern applications. Despite being recognized for over...
Read More
By infosecbulletin
/ Monday , September 15 2025
Every day a lot of cyberattack happen around the world including ransomware, Malware attack, data breaches, website defacement and so...
Read More
By infosecbulletin
/ Monday , September 15 2025
A critical permission misconfiguration in the IBM QRadar Security Information and Event Management (SIEM) platform could allow local privileged users...
Read More
By infosecbulletin
/ Monday , September 15 2025
Australian banks are now using bots to combat scammers. These bots mimic potential victims to gather real-time information and drain...
Read More
By infosecbulletin
/ Saturday , September 13 2025
F5 plans to acquire CalypsoAI, which offers adaptive AI security solutions. CalypsoAI's technology will be added to F5's Application Delivery...
Read More
By infosecbulletin
/ Saturday , September 13 2025
The Villager framework, an AI-powered penetration testing tool, integrates Kali Linux tools with DeepSeek AI to automate cyber attack processes....
Read More
By infosecbulletin
/ Saturday , September 13 2025
Samsung released its monthly Android security updates, addressing a vulnerability exploited in zero-day attacks. CVE-2025-21043 (CVSS score: 8.8) is a...
Read More
By infosecbulletin
/ Saturday , September 13 2025
Albania has appointed the first AI-generated government minister to help eliminate corruption. Diella, the digital assistant meaning Sun, has been...
Read More
By infosecbulletin
/ Thursday , September 11 2025
On September 1, 2025, Qrator Lab identified and managed a major attack from the largest L7 DDoS botnet seen so...
Read More
LockBit ransomware continues attacks:
On Saturday, the gang said it was restarting its ransomware business and acknowledged that their carelessness led to law enforcement stopping its activity in Operation Cronos.
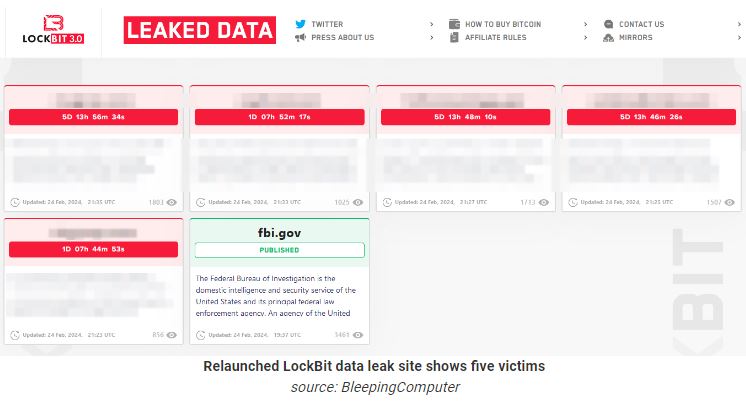
Keeping their name as usual, LockBit moved its data leak site to a new .onion address where five new victims name disclosed.
6 days back, “Operation Cronos” was led by the UK’s National Crime Agency (NCA) with support from Europol, Eurojust, and global law enforcement agencies. The task force was able to take control of 34 servers that made up LockBit’s primary platform, as well as 14,000 accounts used by the group to host tools and store data stolen from victims. The operation also seized 200 crypto-wallets and 1,000 decryption keys which were used to develop a decryptor tool that is now available to the public.

 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














