Intel released 41 security advisories this Patch Tuesday, which contain information about over 90 vulnerabilities in their products. The company has fixed most of the vulnerabilities with patches and provided some mitigations for others.
The most significant flaw is CVE-2024-22476. It is rated as ‘critical’ and has a severity score of 10. This flaw has been found in Neural Compressor, an AI product that optimizes models to make them smaller and faster for deep learning applications on CPUs or GPUs.
By infosecbulletin
/ Wednesday , September 10 2025
Sophos fixed an authentication bypass vulnerability in its AP6 Series Wireless Access Points, preventing attackers from obtaining admin privileges. The...
Read More
By infosecbulletin
/ Wednesday , September 10 2025
Security researcher Jeremiah Fowler discovered a database containing sensitive information from gym customers and staff, including names, financial details, and...
Read More
By infosecbulletin
/ Wednesday , September 10 2025
Microsoft patched September 2025 Patch Tuesday 81 flaws, including two publicly disclosed zero-day vulnerabilities. This Patch Tuesday addresses nine critical...
Read More
By infosecbulletin
/ Tuesday , September 9 2025
Elastic reported a security incident caused by a breach at Salesloft Drift, leading to unauthorized access to an internal email...
Read More
By infosecbulletin
/ Tuesday , September 9 2025
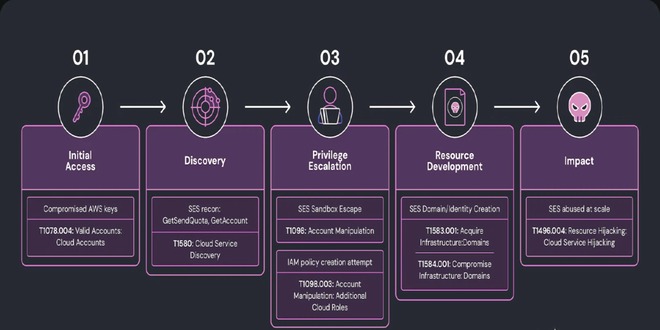
Researchers at Wiz discovered a complex phishing campaign using Amazon's Simple Email Service (SES) for large-scale attacks, showing how hacked...
Read More
By infosecbulletin
/ Monday , September 8 2025
The global ransomware landscape continues to shift in 2025, with SafePay rapidly emerging as one of the most active and...
Read More
By infosecbulletin
/ Sunday , September 7 2025
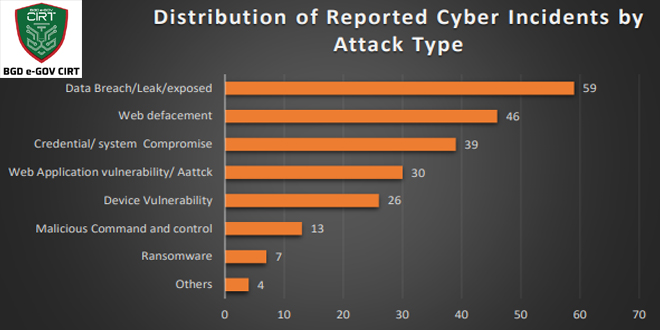
Bangladesh Cyber Threat Landscape 2024, by BGD e-GOV CIRT, reveals a sharp escalation in cyber threats across Bangladesh. The year...
Read More
By infosecbulletin
/ Sunday , September 7 2025
Investigations into the Nx "s1ngularity" NPM supply chain attack have unveiled a massive fallout, with thousands of account tokens and...
Read More
By infosecbulletin
/ Saturday , September 6 2025
ISC2 has launched a Threat Handling Foundations Certificate to assist cybersecurity experts in enhancing Digital Forensics and Incident Response (DFIR)...
Read More
By infosecbulletin
/ Thursday , September 4 2025
Jeremiah Fowler, a cybersecurity researcher, found an unprotected server revealing 378 GB of Navy Federal Credit Union files, including operational...
Read More
Intel says this critical vulnerability could allow an unauthenticated attacker to “enable escalation of privilege via remote access”.
Serious flaws were discovered in various server products’ UEFI firmware, including Arc & Iris Xe Graphics, PROSet/Wireless, Power Gadget, Trust Domain Extensions, Secure Device Manager, Dynamic Tuning Technology, Thunderbolt, Graphics Performance Analyzers, BIOS Guard, Platform Properties Assessment Module, and Ethernet Controller I225 Manageability products. These flaws can allow privilege escalation, DoS attacks, or information disclosure.
Medium-severity vulnerabilities in various products have been fixed. These products include Data Streaming Accelerator, Analytics Accelerator, Processor Diagnostic Tool, Graphics Performance Analyzers, Extreme Tuning Utility, Computing Improvement Program, Ethernet Controller Administrative Tools, Quartus Prime, Processor Identification Utility, Programmable Gate Array, Core Ultra processor, and Advisor.
Medium-severity issues have been found in various Intel products such as Inspector, Distribution for GDB, Data Center GPU Max Series, Performance Counter Monitor, VTune Profiler, Chipset Device Software, Driver & Support Assistant, and others.
Many of these flaws can be used to gain more privileges or carry out DoS attacks or information disclosure.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind