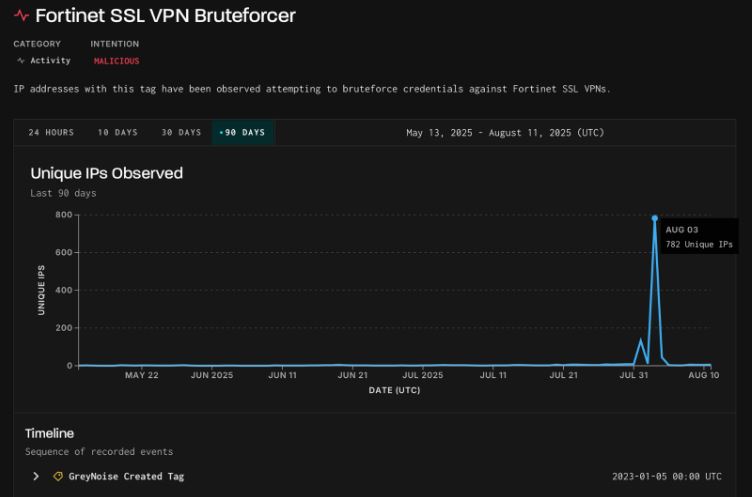
An unprecedented surge in brute-force attacks targeting Fortinet SSL VPN infrastructure, with over 780 unique IP addresses participating in coordinated assault campaigns.
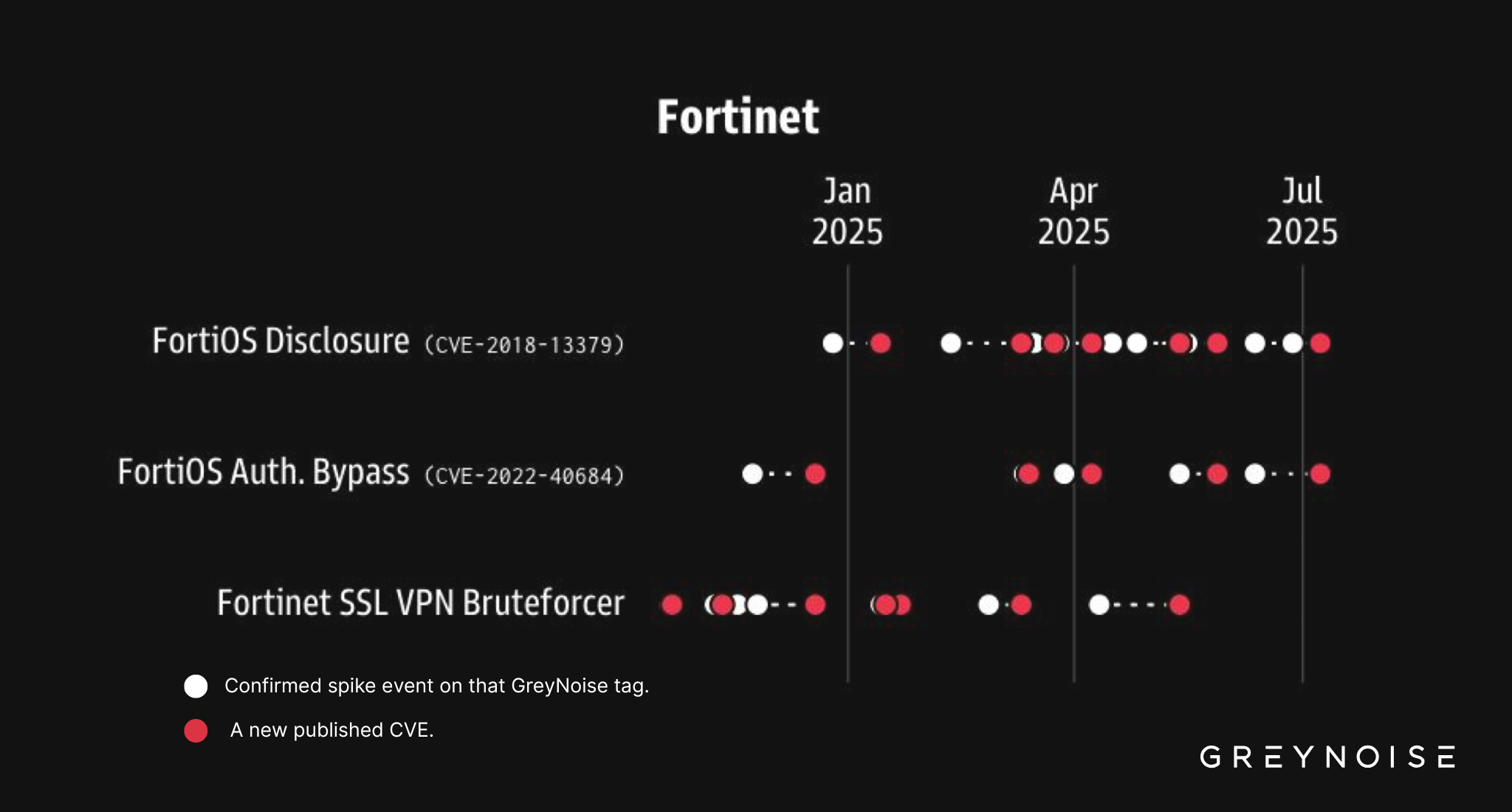
The August 3rd attack represents the highest single-day volume recorded on GreyNoise’s Fortinet SSL VPN Bruteforcer tag in recent months, raising concerns about potential zero-day vulnerabilities and sophisticated threat actor operations.
Fortinet Attack Waves Detected:
GreyNoise identified two distinct attack waves with markedly different characteristics and targeting methodologies.
The first wave consisted of sustained brute-force activity utilizing a consistent TCP signature that maintained steady traffic patterns over extended periods.
However, the second wave, beginning August 5th, demonstrated a completely different TCP signature profile and exhibited concentrated burst patterns that suggested coordinated infrastructure deployment.
The initial August 3rd traffic specifically targeted GreyNoise’s FortiOS profile, indicating precise reconnaissance and deliberate targeting of Fortinet’s SSL VPN implementations.
However, researchers observed a significant tactical shift when traffic fingerprinted with combined TCP and client signatures began consistently targeting FortiManager – FGFM profiles instead of FortiOS systems.
This behavioral pivot suggests either the same threat infrastructure adapting to new attack vectors or sophisticated toolset evolution targeting different Fortinet-facing services.
Key malicious IP addresses identified in the campaign include 31.206.51.194, 23.120.100.230, 96.67.212.83, 104.129.137.162, and 118.97.151.34, among others. Geographic analysis reveals Hong Kong and Brazil as the primary target countries over the past 90 days.
Investigation into historical data tied to post-August 5th TCP fingerprints revealed intriguing connections to residential network infrastructure.
GreyNoise discovered an earlier June spike featuring a unique client signature that resolved to IP address 104.129.137.162, identified as a FortiGate device operating within a residential ISP block managed by Pilot Fiber Inc.
This residential connection suggests either initial tooling development and testing from home networks or sophisticated use of residential proxy services to obfuscate attack origins.
The device showed recent detections by AbuseDB but remained undetected by residential proxy identification services like Spur.us, indicating potential evasion capabilities.
JA4+ signature analysis revealed clustering patterns connecting recent attack waves to prior traffic, establishing potential attribution links across multiple campaign phases.
GreyNoise research indicates that 80% of similar attack spikes precede CVE disclosure within six weeks, suggesting imminent vulnerability announcements affecting Fortinet infrastructure.
Organizations utilizing Fortinet SSL VPN solutions should immediately implement dynamic IP blocklists and monitor for traffic matching the identified attack signatures while preparing for potential emergency patching requirements.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind